A Guide to Protecting Personal Data after Losing Your Mobile Device
Did you know there’s a term for the extreme fear of not being with your phone? It’s nomophobia, and apparently, people who suffer from this can experience physical symptoms such as rapid heartbeat and chest tightness.
Well, just because you want to have your phone on you most of the time doesn’t mean you have nomophobia. In fact, wanting to have your phone in your possession makes sense. Our phones contain a wealth of personal data – information that can cause serious consequences if it falls into the wrong hands. That alone is reason to feel anxious.
The good news: There’s hope. A lost phone does not necessarily mean negative outcomes such as identity theft. That’s especially true if you’ve taken proactive steps to protect your phone and the data on it.
- Protect: Take proactive security measures. Create a strong passcode for your phone, add a PIN to your SIM card and perform regular data backups. Practice remotely locating your phone while it’s safely in your possession. Dry runs prepare you to find your phone quickly if you lose it someday.
- Locate: Take immediate steps to find your device once you reapze it is missing. Mark it as lost, and if necessary, erase the data on it.
- Change and Contact: Protect your personal data in real time. If you can’t find your device and it contains, say, credit card numbers, cancel these cards. Change your email passwords and remove the phone as a trusted device for multi-factor authentication.
- Follow-Up: Keep an ongoing eye on your credit reports, bank statements and the pke. Even if your phone was missing for only 15 minutes, that’s enough time for someone to have pfted important information from it.
This guide outlines some expert tips. It then focuses on device location in case your device is missing right now.
View from the Experts: Protecting Personal Data After Losing Your Mobile Device
Steps to Take After Losing Your Mobile Device
Oh, no! Your mobile device is missing. Try not to panic. We know, that’s easier said than done, but if it helps, we compiled a list of things you can do as soon as you discover that your smartphone or mobile device is missing. The first step is the most important, and the sooner you do it, the more likely you’ll be able to recover your phone.
So what is that crucial first step? See if you can locate it remotely. Smartphones, tablets, and laptops usually offer remote location tracking these days. Find a computer and sign in using your iCloud, Google, or Windows account (depending on the lost device). If your mobile device is still on and connected to the internet, odds are high that you can still locate it. When you do, mark lock it, mark it as lost, or if necessary, wipe the data on it.
- Locate your device through standard means (Apple and Android). Mark it as lost and/or erase data.
- Try Google Timeline or other nontraditional means if standard location does not work.
- Go through the types of personal data stored on your device and how accessible each piece is. Write the type of data down and where it’s stored to ensure you address everything. Even if you find your device quickly, you may still want to change passwords and cancel accounts.
Pro Tip: A password manager can help store all of your long, complex passwords in an encrypted digital vault. Two of our favorite password managers are NordPass and 1Password.
- Change your email passwords along with passwords for important apps/websites such as banks and credit cards. Remember that personal data such as your Social Security number could be buried deep inside the email inbox on your phone.
- Remove access to your apps, if possible or necessary.
- Remove your phone as a trusted device for any two-step verification or multi-factor authentication services.
- Contact your banks, credit card companies and similar institutions. Many have apps or web features allowing you to report a card as lost or stolen. Close your accounts, and open new accounts with new numbers.
- Contact your wireless carrier. Tell the carrier you lost your phone and want to cancel service. Cancellation ensures that no one uses your apps/accounts online and runs up charges.
- Report your lost device to the police. The authorities might know about a theft pattern in the area and have ideas about where to find your device. Also, a lost or stolen device could finger you as a suspect in a criminal case. Reporting your phone as lost establishes that it wasn’t in your possession.
- Keep an eye on your personal data for at least a year. Even your health insurer rejecting a legitimate claim can be a sign of identity theft.
One more thing: If you have signed bring-your-own-device (BYOD) agreements with your employer, be mindful about what you’re required to do. For instance, the agreement might mandate you to notify your employer within 24 hours of you losing a device. The employer might also have the right to conduct a remote data wipe regardless of your feelings on the matter.
Not sure what “personal data” means?
Think of it as personally identifiable information. It’s any piece of information that can be used to identify you.
Examples include:
- Name
- Social Security number
- Birth date
- Place of birth
- Mother’s maiden name
- Biometric records
Some pieces of data such as a Social Security number are strong enough by themselves to identify you much of the time. Other types need to be combined but can prove just as devastating.
Suppose a thief calls your email provider to steal your email password (a form of social engineering). Customer support asks about your birth date, mother’s maiden name and first pet to verify “your” identity.
The thief answers these questions correctly because he’s gone through your social media posts. After he gains access to your email account, he plans to dig up other nuggets of personal data.
Should I Lock My Device Right Away and Erase Its Data?
To lock it? Yes! Definitely. Locking your device means whoever has it won’t be able to access any more of your data. It’s better to assume that whoever found it could do something nefarious (like steal your data or snoop) than to assume that everyone has a kind heart and will return it to you unscathed.
That said, it’s not wrong to hold out hope. If your mobile device has the feature, add a message along the lines of, “Lost phone. Please call me at [number],” when you lock it remotely.
As for whether you should erase the data, it’s a bit trickier. The data will be gone forever unless you’ve backed up your phone recently. Photos, videos, messages, appointments – all those could be permanently wiped. Before wiping your phone clean, here are some things to consider:
- How close you are to finding the missing device or having it back in your possession
- How sensitive the personal data is
- The degree of data protection you’ve already taken with your phone
- How much you could permanently lose with an erase
To expand on the last point, do you back up your data? When was the last backup, and how thorough was it? Also, a data erase means that remote location won’t work anymore.
Deciding whether to wipe your device requires you to balance your risk tolerance with the realities of the situation at hand.
Apple Remote Device Location
Find My [Device]
Lost your Mac, iPhone, iPad, iPod touch or Apple Watch? Look for it via icloud.com/find or the Find My app on another Apple mobile device. A map should pinpoint your device’s location and give directions to where it is. You can also play a sound to help you hear the device if it’s connected to a network.
Offline finding is possible on many Apple devices. You must have a passcode for it to work.
Mark As Lost
It’s a good idea to mark your device as lost, even if the device is just across the street. You never know who might come across it in the span of a minute. Apple’s “Mark As Lost” feature uses a passcode to remotely lock the device and disable Apple Pay. It also lets you type a display message in case anyone finds the device. Most people type something like, “This phone is lost. Call me at…” with a phone number for finders to call. Once you get the device back, use the passcode to unlock it.
Remotely Erase Data
You might need to remotely erase the data on your device. This could apply in cases of extra-sensitive data or if the device is on the move, cannot be located or is too far away (among other situations). Be careful if you perform a data erase since you may no longer be able to find the device.
- Treat a remote erase as a last resort unless the data is quite sensitive and/or the phone has been missing and unlocked a long time.
- Your device must be online. If it’s offline, the erase begins the next time it is online.
- If you find the device, use your most recent iCloud or iTunes backup to restore data.
- Activation Lock prevents others from using your remotely erased device.
- Your custom message keeps showing after a data erase.
- Data erases are a good idea when you plan to give away or sell your device.
Think twice about removing a device from iCloud after you conduct a data erase. That removes Activation Lock and the custom message. In such a case, someone could simply turn on your device and use it.
Contact your wireless carrier to report your device lost (or stolen). The carrier can disable your account so no one is allowed to use it for calls, texts and data.
Pro Tip: Use Family Sharing for relatives’ devices. Suppose a child in your Family Sharing group loses his iPhone. He can use your iPhone to find his. Similarly, use Help a Friend in your Find My app to help friends find their lost devices.
Android Remote Device Location
Have you linked your phone or tablet to Google?
If yes, type, “find my phone,” into the Google search bar to locate or ring the device.
“Find My Device”
The Android device must be turned on, connected to Wi-Fi or cellular data, be signed into a Google account, be visible on Google Play, have Location turned on, and finally, have Find My Device enabled under security settings. Whew! Fortunately, it’s pretty easy to meet these conditions. Most people do it automatically without thinking about it. For example, many mobile devices, even laptops, come with the Find My Device security setting already on.
To find, lock and/or erase an Android device, follow these steps:
- Go to https://android.com/find and sign into your Google account. For devices with multiple profiles, choose a Google account on the main profile.
- Pick your lost device.
- Study the map for your device’s location. It could be exactly correct or might be more of an approximation. If the device is turned off or cannot be pinged, the map shows its last known location.
- Decide on your next step. You can do any of the following:
- Play sound to have your phone ring at full volume for five minutes. This works even if you’ve set the phone to silent or vibrate.
- Secure device to put a customized message on the device and set your previously designated lock (PIN, passcode or pattern). If you’ve not set up a lock, you can do so now.
- Click “Enable lock & erase” if you prefer to immediately lock your device and erase data. This removes the ability of “Find My Device” to locate the device.
- Erase device to delete data from your phone, although it might not work on your SD card.
If you erase data and then find your device, you can still use it with your Google account password.
Pro Tip: Use your smartwatch to find your phone. Tap the “Find my phone” app on the watch. Both devices must be connected via Bluetooth, and the phone must be close enough for you to hear it ringing.
Remote Device Location: Nontraditional Means
What if your phone is turned off or in an area with erratic cell signal? There are ways to remotely find your device if regular means don’t work.
Timeline (Google Location History) for Android Devices
For this method to work, your missing device must have access to the internet (or had access before being turned off). It must be connected to your Google account and have Location Reporting and Location History on.
Go to Your Timeline. Check that the current calendar day is showing. You should see all recorded locations for your device, including its last known location. This type of tracking is approximate, using cell tower IDs and Wi-Fi. Still, it comes in useful if your phone is on the move or goes to the same places again and again. You can generally trust the data to be accurate, although bizarre results aren’t unheard of.
Google Photos for Android Devices
This method works only if someone is taking pictures with your missing device (hey, it does happen). The missing device also needs to have backup and sync enabled in Google Photos and be connected to the internet.
OK, suppose someone has your device and is taking pictures with it. Each new photo uploaded to your Google Photos includes location data as well as the image itself. Either can lead you to the device’s location. Head over to https://photos.google.com/ to see if you have new photos since your device went missing. Click on each new image and its info icon for location data.
Do be careful trying to get your device back. You could be wandering into a dangerous place. Consider going to the police and asking them to handle retrieval.
Miscellaneous Third-Party Services
These services may help you find a missing device.
- Find My Mobile (Samsung)
- Tracking apps such as Cerberus, Kaspersky, Prey Anti Theft and Lost Android (both Android and iOS)
- Dropbox with camera upload enabled and new pictures taken (both Android and iOS)
Two-Factor Authentication and a Lost Mobile Device
Two-factor authentication (2fa) can be a concern when your phone is lost. In case you don’t know what 2fa is, it adds a step beyond your username and password when you want to log into an account. It often requires that you have physical possession of your phone for text/SMS or email messages.
Take this type of situation: You bought a new laptop. You’re on it and about to log into your web-based email account. The email provider, not recognizing the new device, sends a text code to your phone. You type the code into your laptop along with your username and password to verify you’re the email account owner. The problem, of course, is that someone who has your phone can receive the code.
You may have no choice but to use text/SMS and any email accounts on your phone for 2fa. Do unlink them or “revoke all” as soon as possible when you realize your phone is missing.
Authenticator apps and programs may provide peace of mind. They give you backup codes for one-time use. Write down these codes and keep them in a safe place. They help you regain access to any accounts you lock while your phone is lost.
Passwords and the Long Term
The longer your device remains missing, the more uneasy you get. Is your bank account being pilfered? Is someone trawling your email account looking for Social Security numbers? Hopefully not. Good folks do exist. Many people who find a lost device turn it in or safeguard it.
Of course, that’s not everyone. Assume the worst, even if you’ve marked your phone as lost, locked it and erased data. For example, the data erase may have occurred only after a thief accessed most of the information on the device.
Change your email passwords and passwords to other accounts on your phone. Close your bank and credit card accounts, among others. In the long term, keep checking for signs of identity theft such as these:
- More than one tax return filed in your name
- Missing mail
- Mistaken credit card charges
- Collector calls about mystery debts
Make a police report as early as possible to have a record of your device being lost. Otherwise, you may have a harder time proving you are not responsible for certain debts or activities.
“An Ounce of Prevention Is Worth a Pound of Cure”: Phone Locks, Password Managers, Data Backups and More
In 1735, Benjamin Franklin wrote, “An ounce of prevention is worth a pound of cure.” He was discussing fire safety, but his point applies to today’s mobile devices. Take a few precautions to protect your data in general. So many things can and do go wrong with mobile devices. You could lose your phone, it could get hacked, or someone you thought was a friend might snoop through it.
In any case, solid data protection reduces the chances you need to do a data erase. These four safeguards protect your privacy:
Phone Locks and Passcodes
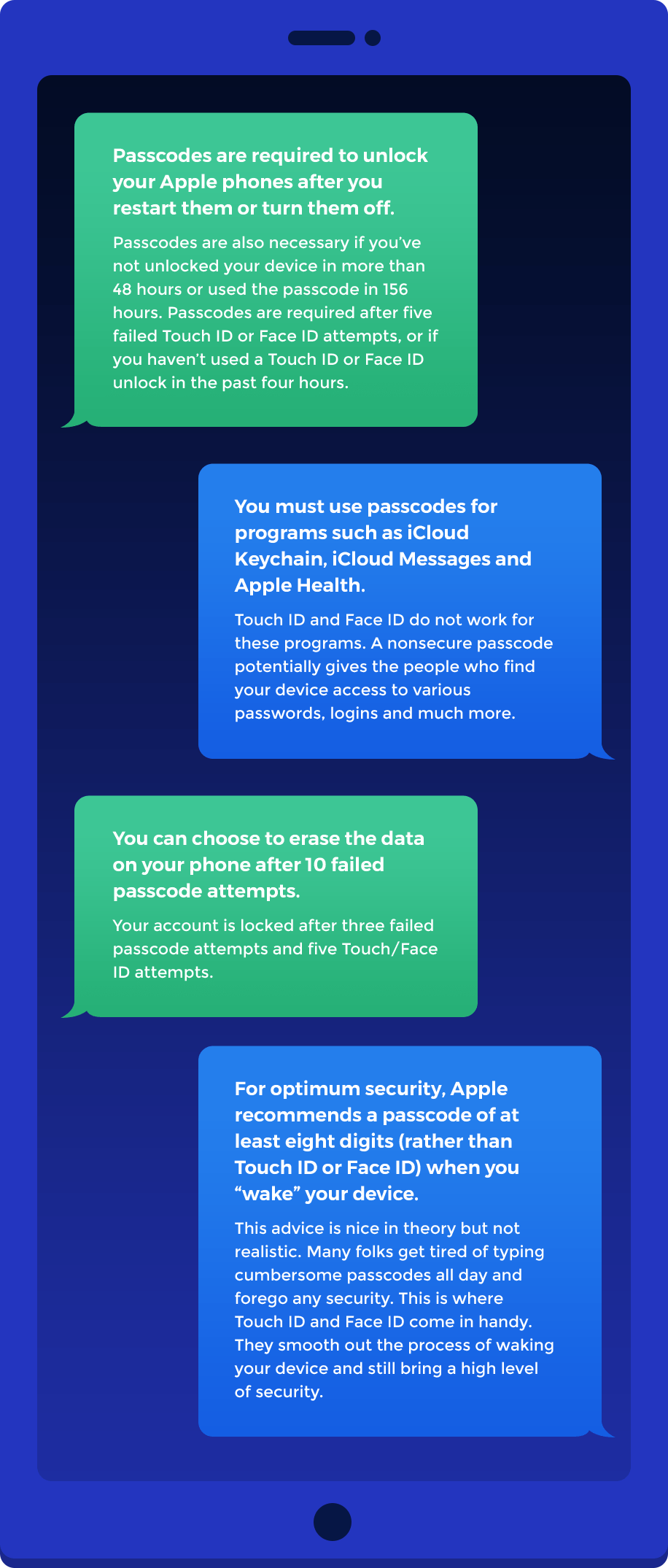
Depending on how new and sophisticated your device is, it might accept biometric IDs along with a passcode, pattern or PIN. For example, Touch ID and Face ID on iOS devices are great. They’re less cumbersome than typing a complicated passcode every few minutes. However, don’t let these biometric technological advances lull you into a false sense of security. It’s very important to have a secure passcode (eight digits or more) even if you rarely use it.
Why are eight-digit passcodes more secure than Touch ID and Face ID?
First things first: It is extremely unlikely that a random person off the street will be able to unlock your phone whether you have Touch ID, Face ID or a passcode (regardless of its complexity). On the other hand, if you have none of these measures, the person could immediately access everything on your device. A four-digit passcode is better than nothing. Apple presents the security odds this way:
- False fingerprint unlock: 1 in 50,000 chance
- False face unlock: 1 in 1 million chance
- 4-digit lucky passcode guess: 1 in 10,000*
- 6-digit lucky passcode guess: 1 in 1 million*
- 8-digit lucky passcode guess: 1 in 3 million to 100 million*
There is a big difference between a one in 50,000 chance (false fingerprint unlock) and a one in 3 million chance (lucky passcode guess). Still, 1 in 50,000 isn’t too shabby.
If you use an Android phone and have patterns or PINs, that’s fine. Anything is better than nothing. Just don’t give Joe Random off the street unfettered access to your device. Use some sort of protection.
*Expect your account to be disabled/locked after three to six failed passcode/password attempts.
Pro Tip: Set your Apple phone to erase its data after 10 failed passcode attempts.
The “self-destruct” occurs on the 10th try. Many folks bypass this option because they imagine their toddler, teenager, spouse or the Good Samaritan who found their phone feverishly typing in 10 passcode guesses one right after the other.
No worries. The data erase doesn’t happen that way. Rather, the process takes MORE THAN THREE HOURS.
- Failed fifth attempt: One-minute timeout, then the “intruder” can try again
- Failed sixth attempt: Five-minute timeout
- Failed seventh attempt: 15-minute timeout
You get the picture. It’s not like the data erase can happen in less than five minutes, although it could theoretically happen while you’re at work or asleep. Back up your data often!
What’s in a Secure Passcode or Password?
The good news first: Don’t worry about resetting your passwords every two months. Focus your efforts on creating something extremely strong that stands the test of time. Now for the bad news…wait. There isn’t any. It’s easier to come up with a strong passcode or password than you may think.
- Aim for at least 12 to 14 characters. If that’s not realistic, six is the bare minimum.
- Use a mix of uppercase letters, lowercase letters, numbers and characters. (On an Apple phone, click on “Passcode Options” and then “Custom Alphanumeric Code.”)
- Trick yourself into easily remembering the passcode. Suppose you really like your neighbor, Nancy. You could use guiding sentences such as these two: “My friendly neighbor Nancy has 8 grandchildren & 3 cars. She is pretty awesome!” The passcode would look like this: MfnNh8g&3c.Sipa! The sentences you use can relate to anything: food, flowers, trips, memories or even folks you hate.
- Use different passcodes for your phone, email, bank accounts and the like. Otherwise, someone who knows your email password could access your phone.
- Change your passcode if there’s been a security incident such as unauthorized access or someone learning the passcode.
- Enlist a password manager to make it easier to, well, manage passwords. That way, you won’t be tempted to reuse your phone passcode across other accounts. You may need to memorize just two passcodes: your phone’s and your password manager’s.
Software Updates
Enable automatic updates for your phone and its apps. These updates contain security protections and patches. Check once every week for manual updates.
Data Backups
Regularly back up the data on your phone to lessen the impact of any data erases. On an Apple device, use iCloud or computer backups. Daily iCloud backups are possible as long as you have space. To restore data to your device after a backup and data erase, choose an option such as, “Restore from iCloud backup,” on the Apps & Data screen.
On an Android device, backups may take the form of photo and Google Drive uploads done automatically. Options for the various backup services vary depending on the specific device.
Other Proactive Data Security Measures
- Use a PIN for your phone’s SIM card.
- Install fewer apps and delete apps you no longer use.
- Buy your device and set up passcodes, data encryption, lost device trackers and other security measures before you even leave the store.
- Use secure folders or vault apps to hide files on your phone.
- Skip auto-complete features that remember/fill in your usernames and passwords.
- Do not keep files on your phone that contain sensitive information such as Social Security numbers and bank account numbers. If you’re going to do this no matter what, encrypt the data or otherwise hide it.
- Take extra care with the data on your child’s device since children lose things often. For example, there’s no need for the phone to have your child’s Social Security number anywhere on it. Of course, the number could still live somewhere on the phone, like in the email inbox. Go through the device regularly to check for the types of data on it.
Employers and Your Personal Data
Be doubly careful about your personal data if you use your device for both personal and work purposes. Many employers use BYOD (bring your own device) policies. In some cases, employers have the authority to conduct a remote wipe of all data, including personal data, on your lost device. That’s true even if you don’t want a wipe to happen. If you can help it, don’t use your personal devices for work.
If you do follow an employer’s BYOD plan, make sure you understand 100% what happens if you lose your phone or if it’s stolen. Will a remote wipe be done no matter what? How much time must pass? When do you have to report a lost phone to your employer? Can you do a data wipe on your own before telling the employer your phone is lost? Your BYOD policy may require you to do the following:
- Report lost or stolen devices within 24 hours
- Regularly back up all data on your phone
- Notify your phone carrier about a lost or stolen device
In addition, employers might have the right to disconnect your device or stop service to it without notifying you (lost device or not). They might also have the authority to wipe your device if you quit, are fired or retire.
Protecting Personal Data After Losing Your Mobile Device
It’s easy to lose your phone. Maybe you’re wearing a coat while carrying a purse and two bags of groceries. Your phone tumbles from your coat pocket onto the ground, and you never notice. Or you’re checking texts in the neighborhood coffee shop when a friend waves hello. You go over to chat but accidentally leave the phone behind. It happens—a lot!
Many lost phones are recovered quickly with no harm done. Other cases are more complicated and may involve remote location, locked screens and data erases. Whatever the case, don’t hesitate if there comes a time when you need to change email passwords and close bank accounts.
Additional Resources
- How to Protect Your Phone and the Data on It:Tips from the Federal Trade Commission
- If You Use Your Personal Phone for Work, Say Goodbye to Your Privacy:A Lack of Workplace Digital Privacy
- Google Maps Keeps a Detailed Record of Everywhere You Go:Sometimes Useful, Sometimes Creepy