2024 Antivirus Trends, Statistics, and Market Report
As cybercrime costs soar, 121 million Americans rely on third-party antivirus programs to protect their devices, and 17 million people may adopt antivirus in the next 6 months.
According to the FBI, cybercrime cost the American public $12.5 billion last year alone. Since ransomware, identity theft, financial scams, and crypto-jacking are so common, how can the average consumer stay safe as digital threats constantly evolve?
Antivirus programs have long served as the first line of defense for personal computers and other connected devices. However, some antivirus programs, like Kaspersky, have come under fire for potentially exposing users to risk. Additionally, some experts have argued whether buying antivirus is truly necessary today given the effectiveness of proprietary antivirus like Microsoft Defender. Despite these potential obstacles to adoption, tens of millions of Americans still rely on tried-and-true antivirus programs to protect their computers from malware and increase their peace of mind.
To better understand the current state of personal device security, Security.org conducted its third annual study on the growing antivirus market in the U.S. and how it may shift over the next 12 months.
Key findings
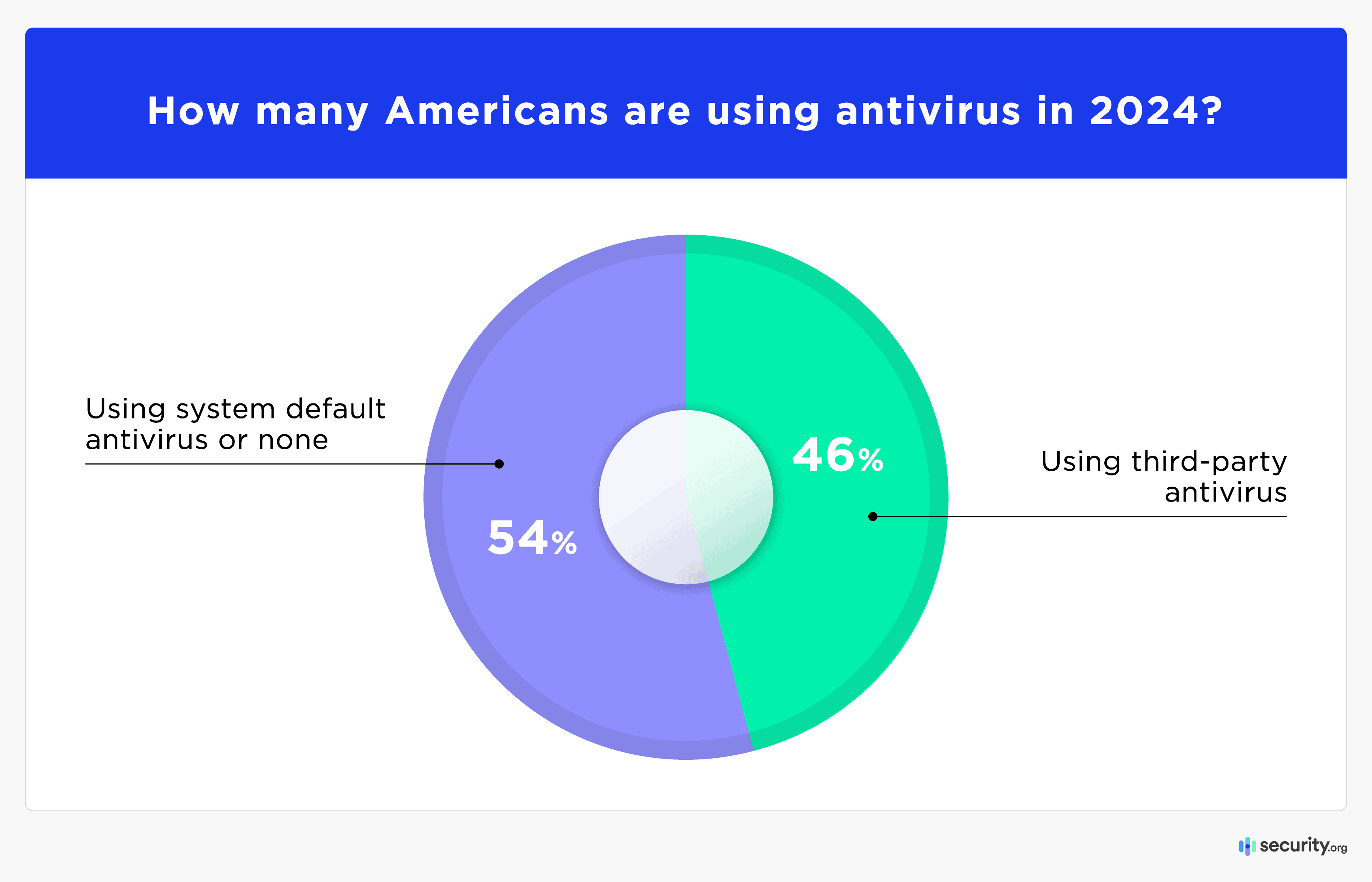
- More than half of Americans rely on their devices’ built-in antivirus protection (or use none at all), but around 121 million adults still turn to third-party antivirus software.
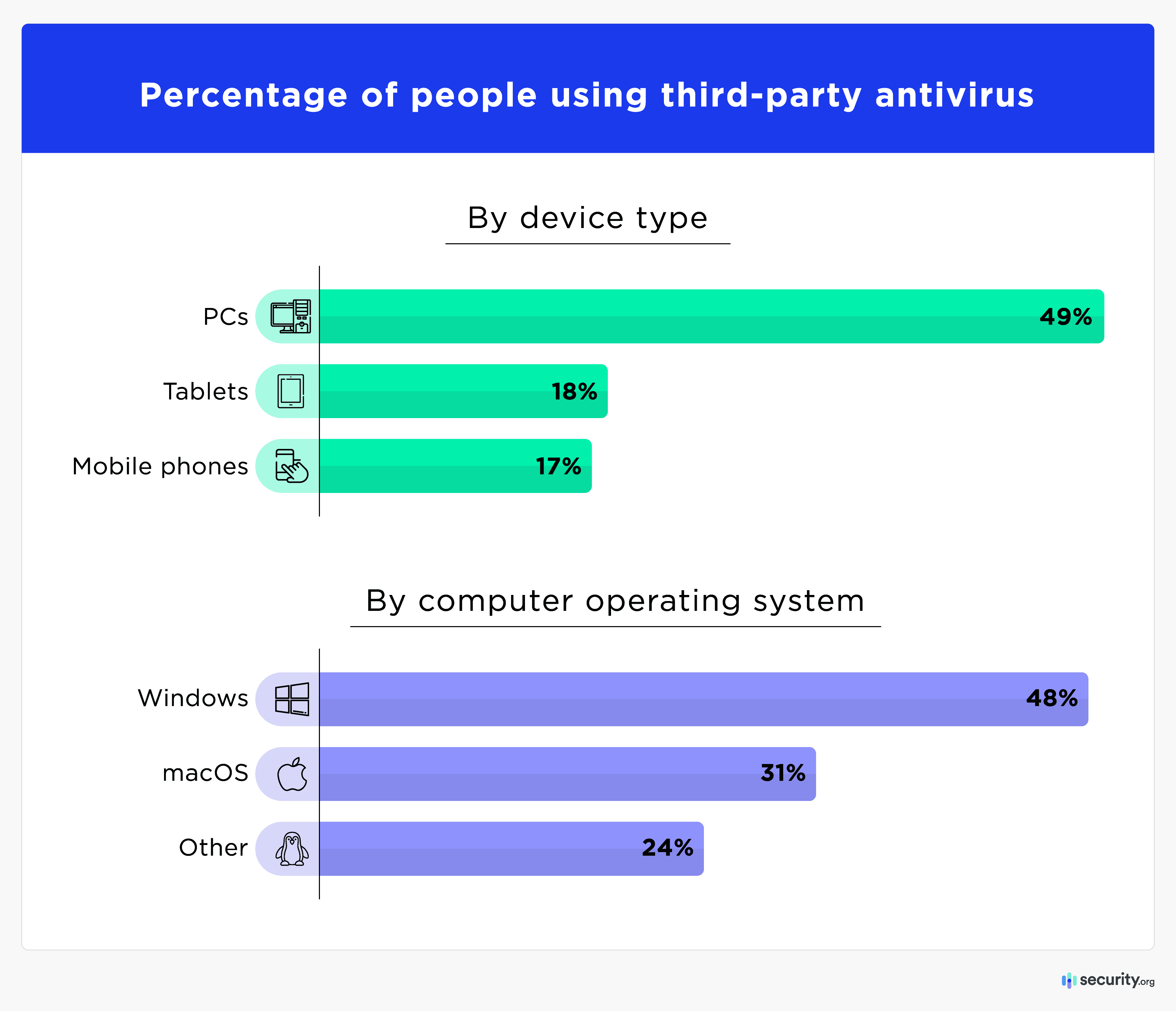
- 17% of adults run antivirus programs on their mobile phones.
- Americans aged 65 or older are twice as likely to pay for antivirus programs as those under 45.
- Norton’s AntiVirus remains the top product for paying antivirus customers, while McAfee is the most popular free third-party tool. Only about 3% of antivirus users were running Kaspersky software before the U.S. government banned sales in June 2024.
- Antivirus use for cryptocurrency transactions has increased in the past two years, while the need to secure remote working connections has dropped by half.
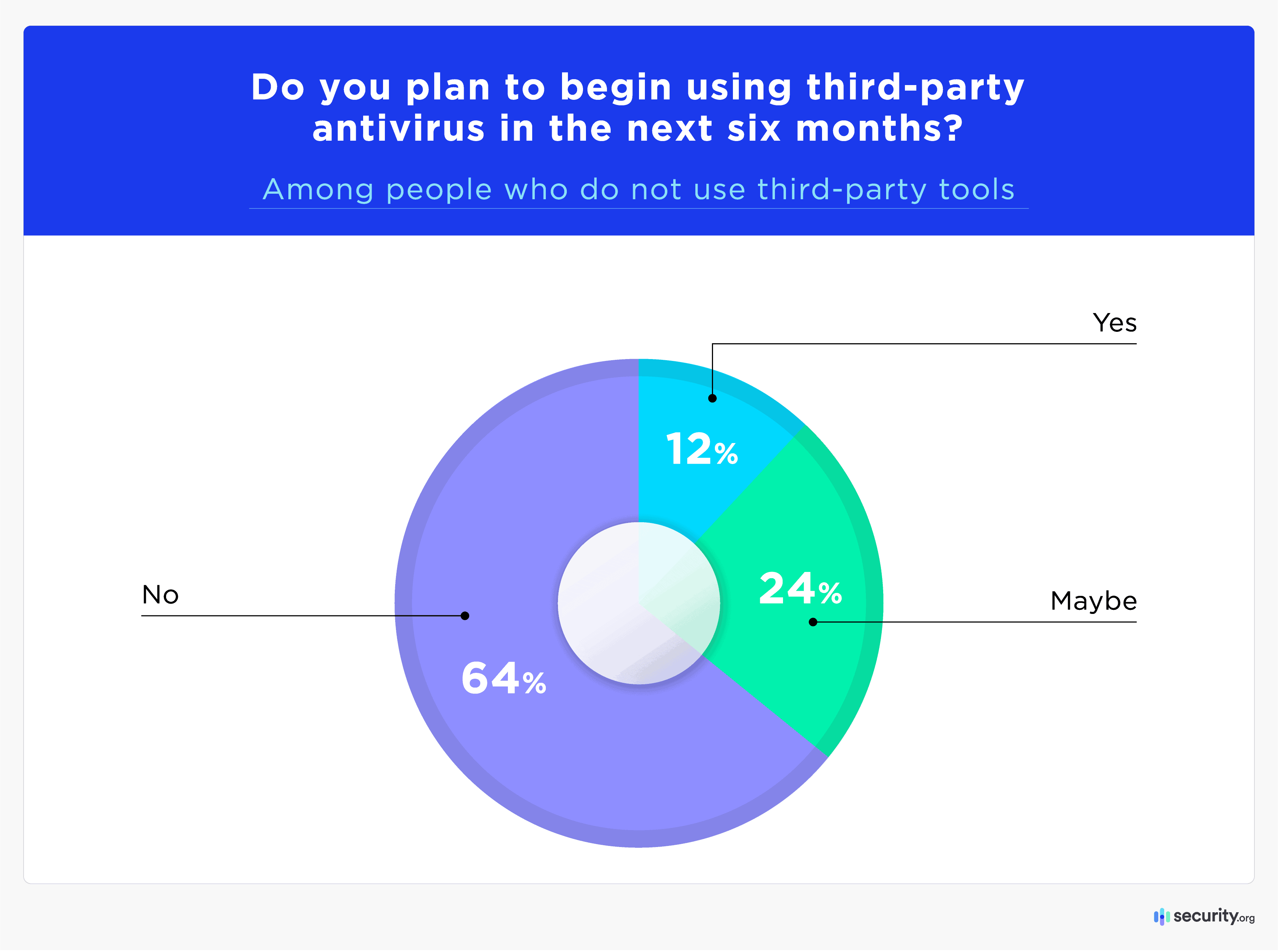
- Nearly 17 million non-users plan to adopt antivirus software in the next six months. This is a 14% growth in the number of users.
Nearly half of U.S. adults use third-party antivirus software
In the 1980s, commercial antivirus programs emerged as the internet began to connect people worldwide. These early safeguards scanned local systems for signature codes of known computer viruses, isolating identified threats. As the internet expanded and malware evolved, countermeasures progressed accordingly. Today, “antivirus software” is a comprehensive term encompassing cybersecurity suites that combine multiple layers of real-time protection.
Beyond finding and neutralizing viruses, modern antivirus technology enlists proactive machine learning, artificial intelligence, predictive models, cloud resources, and endpoint behavioral monitoring to detect real-time dynamic threats. Antivirus software subscriptions often include additional tools such as VPN, identity protection, dark web monitoring, password management, or encrypted storage.
It should also be noted that nearly everyone uses antivirus software, whether they know it or not. As the digital landscape became more dangerous, most operating systems and connected devices embedded automatic antivirus defenses. Modern Windows computers run Microsoft Defender and Apple’s proprietary XProtect by default, which automatically guards Apple computers. All Android devices and iPhones/iPads are protected by anti-malware scans conducted by their app managers.
These proprietary protections have proven effective enough that some experts believe additional antivirus services are no longer necessary. However, the antivirus software industry is still a growing $4 billion market driven by the desire to prevent cybercrime and data breaches. Our research focused on the consumer use of third-party antivirus software, which can supplement or replace automatic manufacturer protections. Nearly one-half of American adults (121 million consumers) use third-party antivirus software on one or more of their devices.
Personal computers (PCs) are particularly vulnerable to malware attacks. Understandably, they are the devices most often protected by third-party antivirus software. A notable percentage of phones and tablets also have these protections. Computers running macOS, a closed operating system, have long nurtured a reputation for being more malware-resistant than Windows computers. This perception is reflected in the more significant deployment of third-party antivirus on Windows-based PCs.
Norton and McAfee are most popular among paying antivirus users
Consumers have many options when choosing an antivirus provider, ranging from familiar pioneers to next-gen tech upstarts. Most antivirus companies also supply free or paid versions of their software.
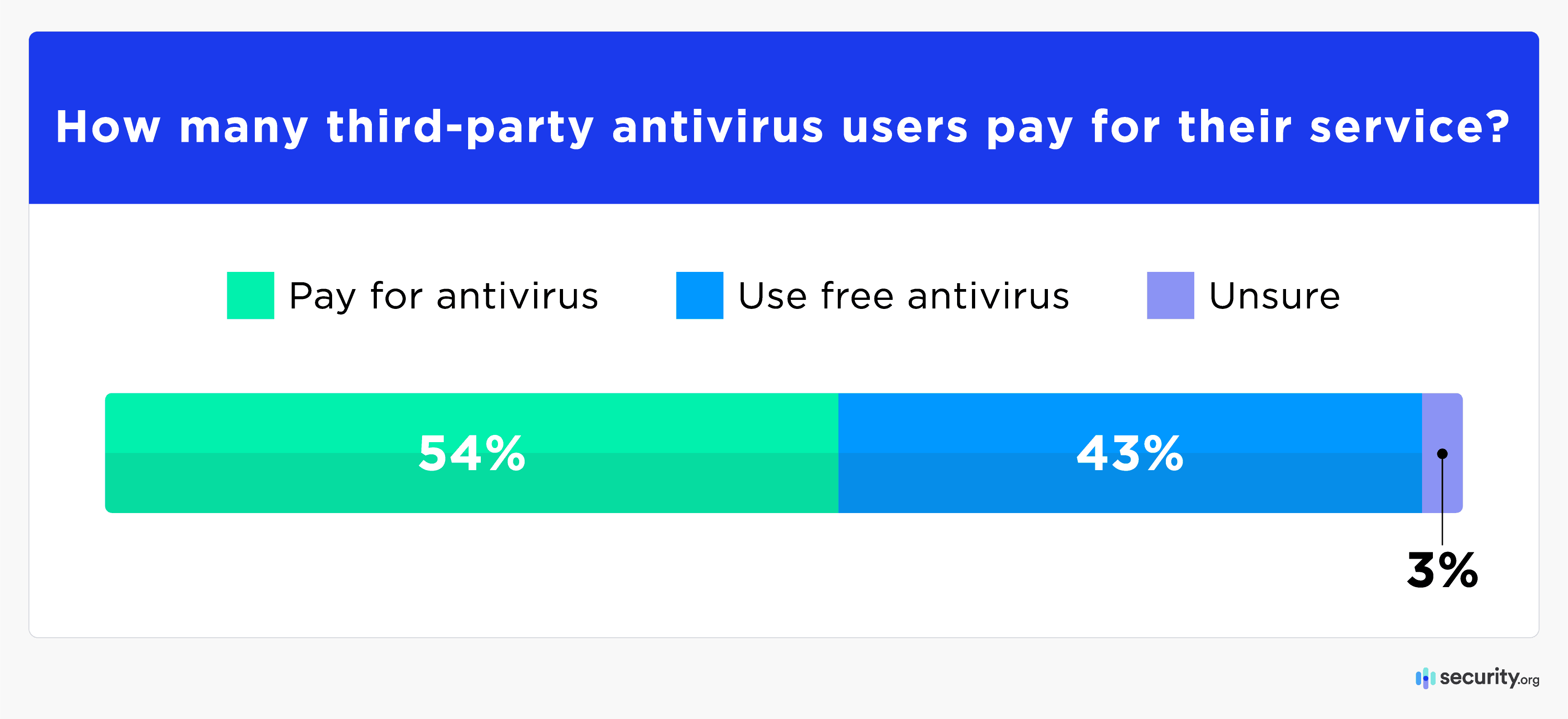
Free antivirus applications are sometimes stripped-down products or introductory offers that convert to paid subscriptions after a trial period. However, some free software, like Surfshark’s, cover unlimited devices and include VPNs. More than half of those using third-party antivirus programs (about 33 million households) pay for more robust cybersecurity protection.
Older Americans are significantly more likely to use third-party antivirus programs and pay for the software. Those over 65 are twice as likely to subscribe to paid antivirus services than those under 45.
This disparity by age group may be attributable to several factors. Older Americans may be more cautious with technology, possess more disposable income, and have more significant assets to protect online.
The table below shows the most popular choices for both free and paid third-party antivirus programs.
Which third-party antivirus do you use?
| Provider | Paid users | Free users |
|---|---|---|
| Norton | 29% | 6% |
| McAfee | 23% | 19% |
| Malwarebytes | 10% | 15% |
| Avast | 8% | 18% |
| AVG | 7% | 12% |
| Webroot | 6% | 1% |
| Bitdefender | 6% | 3% |
| Kaspersky | 4% | 3% |
| Other | 6% | 5% |
Norton remains the top pick in a fragmented field for those subscribing to paid antivirus services. McAfee also holds a significant portion of free and paid antivirus markets, likely due to an aggressive marketing approach that pre-installs free trials on many personal computers.
Other familiar names on the list may lose market share based on recent developments. In June 2024, just after we conducted our research, the Biden Administration banned Kaspersky software in the U.S. due to national security concerns rooted in the company’s Russian ties. The U.S. Commerce Secretary Gina Raimondo explained that since Russia has the capacity and intent to exploit Russian companies and their American customers’ data, the ban is necessary. Additionally, Avast, more popular than Kaspersky, was recently cited for selling personal data collected by its antivirus software.
In light of recent revelations linking supposed antivirus safeguards to malicious foreign actors and data pirates, selecting an antivirus provider has become increasingly complex. To better understand consumer choices, we asked consumers to share their needs, experiences, and confidence levels regarding antivirus software.
More people are turning to antivirus to protect crypto exchanges
Modern antivirus platforms and their cybersecurity suites offer a wide range of tools and services, but solid protection against malware remains the top priority for third-party antivirus subscribers.
| Why do you use third-party antivirus software? | Percentage of users |
|---|---|
| General security against malware and viruses | 84% |
| General privacy concerns | 56% |
| Increased security while online shopping | 48% |
| It’s what came on my device | 19% |
| Use public Wi-Fi without risk | 18% |
| Required for job | 12% |
| To protect cryptocurrency exchanges | 8% |
| Secure VOIP phone calls | 3% |
Note: Multiple choices allowed
Privacy issues are another significant concern among antivirus users. Stolen medical records, biographical information, personal communication, browsing histories, and financial transactions can put users at risk of identity theft, doxxing, or other serious repercussions. Half of antivirus users desired extra peace of mind when transmitting credit card information through online purchases.
The most significant changes from our previous study were:
- A 50 percent decline in people citing work requirements, likely due to the post-pandemic reduction in remote working.
- An increase in individuals using antivirus services to safeguard their transactions on cryptocurrency exchanges
Most consumers believe antivirus programs supply the protection they require. Overall, 88 percent of Americans feel that antivirus software is effective. Confidence in antivirus programs is even higher among users of third-party software – particularly with paying customers.
Determining whether this faith in antivirus protection is fully justified is difficult. Around six percent of antivirus users experienced breakthrough malware or viruses in the past 12 months, and there was not a significant difference in the prevalence of breakthrough viruses between those who use paid or free third-party antivirus and those who use proprietary software. However, some users may not have noticed if their devices were impacted by malware.
Experts acknowledge that antivirus programs alone can’t prevent all malware and malfeasance. Accordingly, antivirus software should constitute only one part of all users’ digital security strategies. A majority of Americans believe safe browsing habits are even more critical than antivirus protection—an opinion supported by data showing human error is now the root cause of most data breaches.
| Which features are included with your antivirus software? | Percentage of third-party antivirus users |
|---|---|
| Firewalls or network protection | 59% |
| Secure browser | 51% |
| System performance optimization | 38% |
| Password manager | 32% |
| VPN | 29% |
| Identity theft protection | 27% |
| Parental controls | 19% |
| Encrypted cloud storage | 16% |
| None of the above | 21% |
Note: Multiple choices allowed
Additional security tools can improve personal online practices, including password managers, VPNs, browser safeguards, encrypted storage, identity monitors, and system optimizers that ensure all drivers and utilities are current. At least one of these features comes with four out of five third-party antivirus packages. More vigilant marketing of these supplementary services may be the key to further growth in the antivirus software sector.
1 in 3 non-users are considering antivirus adoption
Given the number of data breaches, identity thefts, and other digital security threats, it’s little wonder that nearly 90 percent of Americans agree that computers need antivirus protection. However, not everyone who feels they’re important has adopted antivirus programs.
To win over holdouts, cybersecurity providers must address their concerns. The foremost obstacles to antivirus adoption are cost, apathy, and security worries about antivirus software (53 percent of Americans fear personal data is collected and misused by antivirus providers). Unfortunately, that is a real threat, evidenced by Avast’s recent misuse of customer data and the threats of misuse by Kaspersky. Some people with “other” issues were worried about antivirus software impeding their computer’s performance.
| Why don’t you use antivirus software? | Percentage of non-users |
|---|---|
| It’s too expensive | 45% |
| I don’t need it | 40% |
| I’m not concerned about viruses | 28% |
| My antivirus subscription expired, and I didn’t renew it | 17% |
| I have security concerns about antivirus programs | 11% |
| Other | 6% |
Note: Multiple choices allowed
Despite the holdouts, the third-party antivirus market continues to expand and has the potential for more growth. Though six percent of third-party antivirus users plan to let their current plans expire, 11 percent first adopted third-party software within the past year. Additionally, 12 percent of non-users plan to sign up for third-party antivirus in the next six months, equating to nearly 17 million new customers.
Identity theft protection, VPN service, browser monitoring, and firewalls are the most appealing additional antivirus features for those currently lacking antivirus protection.
| Which of these antivirus features is most appealing to you? (Among those currently without antivirus protection) | |
|---|---|
| Identity theft protection | 20% |
| VPN | 17% |
| Secure browser | 16% |
| Firewalls or network protection | 15% |
| Password manager | 9% |
| System performance optimization | 6% |
| Encrypted cloud storage | 5% |
| Parental controls | 2% |
| Other or none of the above | 10% |
These findings clearly show that antivirus providers have ample opportunity to attract additional business. Americans are worried about online threats, believe antivirus software is effective, and are open to signing up for third-party services. Cybersecurity companies should control costs, raise threat awareness, and reassure potential customers about safety and performance issues while offering a well-rounded suite of additional tools to be most appealing to new signups.
Conclusion
A hostile digital environment has online Americans rightfully worried. Last year, internet crime incidents rose 10 percent, resulting in a 22 percent jump in financial damages. Though almost every connected device features some security measures, less than half of consumers use enhanced third-party antivirus software. That leaves 140 million adults surfing the web with minimal protection.
Cyberspace threat matrices are constantly shifting and will grow more dangerous via the misuse of emerging AI and quantum computing power. Optimized protection will require cutting-edge defenses rooted in these same technologies, in addition to centralized cloud computing, biometrics, passkeys, and advanced encryption methods. The commercial rollout of these safeguards will likely come through leading antivirus platforms.
Antivirus programs can’t stop every danger. However, when combined with additional tools promoting safe online behavior, such software suites afford considerable protection. By raising awareness, expanding their offerings, and managing price points, third-party antivirus providers can grow their client base while keeping more Americans safe.
Our data
In April 2024, security.org conducted an internet poll of 996 American adults. The respondents were representative of the U.S. population based on gender, age, and ethnicity. 49 percent were female, 50 percent male and fewer than one percent did not report. 64 percent were white, 14 percent Black, 11 percent multiracial, 5 percent Asian, and 7 percent were of another ethnicity.