The Complete Guide to Accessibility and Digital Security
How to safely navigate the internet with vision loss, hearing loss, or other disabilities
By Kelly Short, Master’s in Deaf Education | Updated November 2023
The digital world is far from 100% accessible, even after the 2018 Department of Justice ruling that required websites to meet ADA requirements with guidelines on how to become ADA compliant following in 2022.1 Yet, in 2024, many people still cannot access basic governmental services to file for taxes, register to vote, and get important records. Someone who has to give up privacy or rely on another person’s help is at higher risk of exploitation and theft.
Digital security issues are poised to affect even more people as the ranks of seniors 65 and older swell. Many seniors have a disability like some of their younger counterparts do. And those disabilities such as hearing or vision loss, create new digital security and identity theft risks. So, our digital security experts partnered up with our accessibility team to create a complete guide to keeping yourself safe online if you live with a disability.
Table of Contents
- Identity Theft, Cybercrime, and People with Disabilities
- Phishing Scams
- Social Media Fraud Scams
- Password and Passcode Accessibility
- Third-Party Vetting Assumptions
- Eavesdropping Concerns
- Familiar Fraud
- View from the Experts: Accessibility and Digital Security
- Additional Resources
- References and Footnotes
Identity Theft, Cybercrime, and People with Disabilities
Identity theft occurs when someone obtains sensitive personal information and uses it for financial or economic gain. Examples include phishing, credit card skimming, malware, phone scams, and tax ID theft. Trusted people such as spouses or caregivers can be the perpetrators of a type of identity theft called familiar fraud. People with disabilities are especially vulnerable to typical identity theft and familiar fraud.
Cybercrime refers to illegal activities carried out using technology. There’s a lot of overlap with identity theft, such as phishing and malware. Other cybercrimes include stalking, harassment, and blackmail.
Now, we’ll take a look at six scenarios. They’re fictional but based on real cases. Read through each scenario even if a situation doesn’t seem to address your particular disability. The prevention information is designed to assist all people regardless of their accessibility preferences.
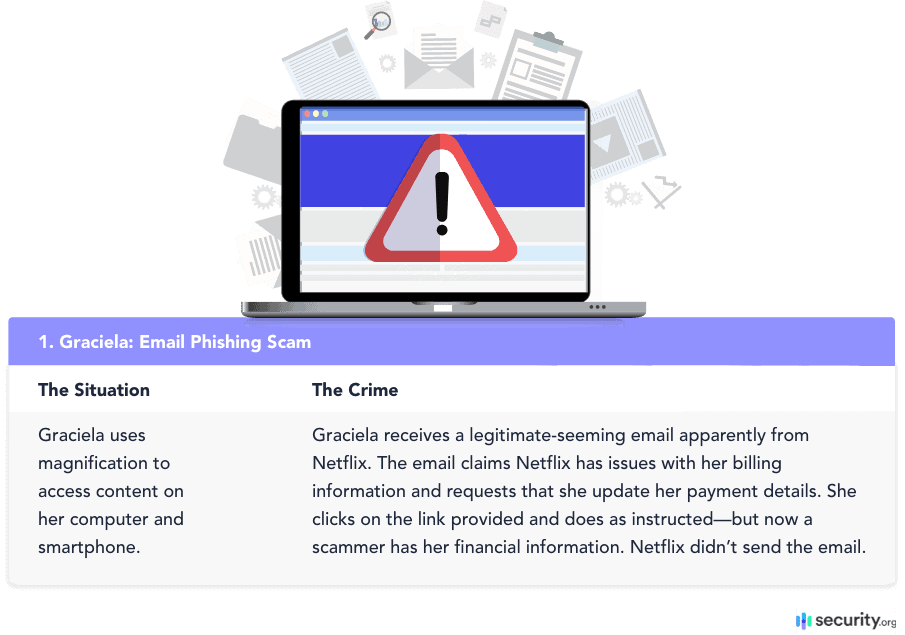
Phishing scammers can be clever. They may send emails and texts with official-looking logos and an urgent call to action like, “Update your information now or be locked out of your account.”
Plenty of people, including folks with poor vision, get fooled by these emails every day. A person such as Graciela is not always able to see or judge an email in its entirety. Similarly, Graciela may be so focused on one aspect of an email that another part slips her attention. To prevent mistakenly giving out your information:
- Go to websites yourself instead of clicking on links in an email. Prevention means Graciela goes to Netflix.com on her own instead of clicking a button or link in the email. It can be more of a hassle given her vision issues but is worth it in the big picture. Whether she uses a keyboard, touchscreen, her voice, or something else, Graciela opens Netflix in a separate window that isn’t connected to the email. She logs into the legitimate Netflix site and updates or double-checks her payment information with no issues.
- Good to know: Netflix asks that customers forward suspicious emails and text messages (SMS) to phishing@netflix.com. If your forward is rejected, that’s OK. It means Netflix already has a copy of the message. Delete your email—definitely don’t click on any links or open any attachments. If you already gave out your information, update your password so it’s unique. Update passwords on other websites that used the same password and email combination.
Watch for certain tells. Greetings such as, “Dear Customer,” or “Hello, customer,” signal an email that isn’t legit. Poor grammar can be a tell too, but there are some scam emails using good grammar. Hover over links to see if they seem genuine. To do this on a smartphone, hold your finger down on the link until a small window giving the full link address pops up. You can usually tell from this full address if a link is legit. Phone accessibility features such as voice control and screen readers may be helpful.
- Look for https and the lock icon, especially when you’re doing something financial or conducting a transaction. Http isn’t secure enough.Set your browsers, security software, and apps to receive automatic updates. Never ignore update notifications. Otherwise, criminals have more of a chance to exploit security loopholes.
- Check your browser’s security settings and upgrade them, if necessary. Chrome, as of September 2023, has three settings: no protection, standard protection, and enhanced protection. No protection is not recommended. Standard offers a good deal of protection against potentially dangerous URLs. It also warns you if a data breach exposed your passwords. Enhanced protection keeps you even safer but requires that your browsing data be sent to Google. That may trouble some people even if the data is anonymized. Whatever protection level you choose, check all of your devices. Using certain settings on one device does not mean they carry over to your other devices.
Jocelyn is far from alone, as many people find themselves in similar straits. Take someone with a mobility disorder who is on conventional medications and vitamins. He’s hopeful to find a treatment and sends money to someone claiming to sell special vitamins that cure the disorder.
First things first: Life isn’t cheap, and disability makes for a steeper uphill climb. People who are hard of hearing may have lower salaries and limited job opportunities.2 They may even grapple with limited income because they’re retired (hearing loss is common among senior citizens). Hearing aids cost a pretty penny, and many insurers don’t cover them for adults.3 (Check out your state’s coverage mandates here.)
Insurers are more likely to cover cochlear implants, but the implants can be pricey in the long term even if insurance fully covers the surgery.4 Many users are responsible for co-pays, pre-surgery expenses, mappings, equipment maintenance, auditory therapy, or speech therapy. Surgery also requires recovery and time off work. Not everyone can take paid leave.
Bottom line, many people with disabilities are eager to save money where they can. The good news for people like Jocelyn is that legitimate, lower-cost deals for hearing aids can be found on Facebook. This could happen when someone upgrades their hearing aids or gets cochlear implants and no longer wears hearing aids. The bad news is, it’s easy to get ripped off. Some tips to protect yourself:
- See if you have mutual friends or friends of friends to vouch for sellers.
- Contact the seller to get as much information as you can about the hearing aids. Ask if there’s paperwork to verify claims such as the age of the hearing aids.
- Talk with your audiologist to make sure the prospective hearing aids meet your hearing needs. Also, discuss potential issues with fit. For instance, customized earmolds are necessary for behind-the-ear aids. It’s generally not a good idea to buy used in-the-ear hearing aids since each person’s ear canal is unique.5
- Try to buy local or at least within a few hours’ radius. Travel to the seller’s area, meet somewhere in the middle, or vice versa.
- Conduct your transaction in a public place.
- Test the hearing aids before you and the seller part ways. Check the aids to make sure they are in usable condition and collect any relevant paperwork. An audiologist still needs to reprogram the aids to meet your hearing needs, but you (or a companion) could determine that they’re functional.
- Note that PayPal purchase protection doesn’t apply if you buy items in person. Venmo has its limitations too, listing the purchase and sale of most goods and services as a prohibited transaction. Do what you can to ensure the hearing aids are in good working condition before you pay.
- Avoid paying by check since checks contain sensitive information.
Passcodes and passwords can be a pain, especially for people with disabilities. It’s understandable if they prefer to go without, but the security risk remains. Fortunately, fingerprint authentication has come a long way in a few years. Heather should consider this authentication method in the future for her phone, computer, and any apps using it.
Fingerprints are generally more accessible then typing numbers and letters, as indicated by the research paper, Understanding Authentication Method Use on Mobile Devices by People with Vision Impairment.6 The majority of 325 study participants, who were blind or low vision, said that fingerprint authentication was the most secure and accessible method available to them. This type of authentication also solves the problem of shoulder surfing (someone looking over their shoulder when they enter a passcode in public). Here’s a rundown of participants’ pros and cons for the various authentication methods to unlock their phone:
- Fingerprints, used by 73% of participants: The most secure and convenient method because fingerprints are unique to everyone; impossible or difficult to duplicate; no memorization required; quick unlocking is accessible to people with vision impairments; faster than PINs; and no Braille display required. On the con side, users don’t always have time to adjust their finger on the biometric scanner. Also, this method may not work consistently for people with tremors or similar issues. Fingerprint authentication is sometimes a pain if hands are wet, oily, cold, or gloved.
- PINs, used by 16.4% of participants: Somewhat accessible but not secure. Slow and cumbersome compared with fingerprint authentication. Shoulder surfing remains a risk, as does aural eavesdropping (screen readers read out loud what users type, and other people can overhear). One participant with tremors said he prefers the PIN method and that it’s accessible for him.
- Alphanumeric codes, used by 4.9% of participants: Issues similar to PINs.
- Facial recognition, used by 2.2% of participants: A security concern because someone could pick up the smartphone, point it at the owner, unlock it and use it, all without the owner knowing. People with vision impairments may also have difficulty positioning their face.
- Pattern, used by 1.8% of participants: Not everyone is able to visualize patterns and draw them accurately. Shoulder surfing is also a concern, even with screen curtains. Pattern authentication is more accessible to those with low vision than those who are blind.
- Iris or retina scan, used by 0% of participants: Some people who are blind don’t have eyes. Those who do sometimes find it difficult to keep their eyes in position for scanning. There’s also a similar concern to facial recognition—someone could use the phone owner’s eyes to unlock the device without the owner’s knowledge.
- Voice recognition, used by 0% of participants: External sounds could confuse voice recognition.
One participant pointed out that a map shows the location of lost devices. He wished that an address would also be announced to make it much easier to pinpoint the device’s location. You can get directions to a device but must go through several additional steps.
The study was published in 2018, and there have been some accessibility gains since then. For instance, you can set iPhone Face ID so you are not required to look at the phone with your eyes open. If you have mobility issues instead of or in addition to vision, there’s the option to set up Face ID so it doesn’t require a full range of head motion. Still, fingerprint authentication seems to still be the most secure and convenient method.
Biometrics such as fingerprints are becoming more common. Mobile banking is just one example. Wells Fargo apps on compatible smartphones allow Apple Touch ID, Face ID, and their Android counterparts. Many Apple devices (phones, tablets, computers, etc.) allow Touch ID instead of an Apple password for password autofill, iTunes, Apple Books, Apple Pay, and App Store purchases. You must have a secure password to enable Touch ID.

Consumers who are deaf or hard of hearing sometimes use third parties to facilitate communication. However, the involvement of more people means higher potential for misunderstandings or even crime.
In a news release, the IRS warned consumers about con artists using VRS to pose as IRS agents. The IRS emphasized that VRS interpreters do not screen calls for legitimacy—a critical point to keep in mind.7 The principle applies whether you use VRS, voice carry over, traditional telephone relay, internet relay, captioned telephone service, or something else. Voice carry over in particular is useful among senior citizens.
It’s up to consumers themselves to determine if something seems fishy. An interpreter or communications assistant won’t interject with something like, “Hey, you really shouldn’t give out your bank account number,” or, “I’m skeptical if you’re actually an IRS agent.”
If you get shady calls, emails, or texts, contact the organization that the potential scammer purports to represent. The IRS recommends that VRS users call 800-829-1040 to confirm if there’s an actual tax issue or to resolve payment. Sorenson asks that you immediately email VRScomments@sorenson.com.
What about the interpreters or communications assistants? Do they keep any sensitive information you share to themselves? Probably, but it’s reasonable to have concerns despite FCC regulations prohibiting CAs “from disclosing the content of any relayed conversation regardless of content, and … from keeping records of the content of any conversation beyond the duration of a call.”8
To sidestep the issue of CA confidentiality, you could turn to avenues such as online bill payment, live online chat, direct TTY chat, email, text, or in-person service. Alternatively, it may be possible to enlist the help of a trusted person on a direct call. Of course, these options are not always available, and each comes with its own security risks.
Nick has several options for in-person and online payment.
- Google Pay or Apple Pay: With Google Pay, Nick just has to unlock his phone (he can probably use a fingerprint), hold his phone over the payment terminal, and wait until he sees/hears a checkmark. Placement over the terminal can be approximate, and Nick doesn’t need to open the Google Pay app. If you use this type of contactless payment, multiple layers of security protect your financial information. Your card details are not shared, and you receive the same purchase protection you do with a bank and PayPal.
- Google Pay lets you access transit cards, boarding passes, and tickets right from your phone—no fumbling through your wallet or purse.
- Apple Pay is similar and even lets you pay via your Apple Watch. Double-click the watch’s side button to use your default card. Keep your watch display near the payment terminal, and wait to feel a soft tap. If using your iPhone, start with Touch ID and hold the top of the iPhone near the payment terminal.
- Not all online and in-person stores accept contactless payment, and you might need to sign a receipt if your payment in the United States totals more than $50. This list gives an overview of what could be required for contactless payment in various countries.
- PayPal: This is a good choice for online shopping and could work for in-person shopping. As the American Federation for the Blind points out, you can set your PayPal app to access location services and get a list of nearby businesses such as salons, restaurants, and grocery stores that accept PayPal.9 However, it’s more complicated to pay in person compared with Apple Pay and Google Pay. You must open the PayPal app, select “Scan/Pay,” hold your phone to the retailer’s QR code, enter the amount owed, and tap “Send.” These steps aren’t feasible or easy for everyone with vision loss. (As a huge side bonus, contactless payment is pandemic-safe, too!)
- Virtual credit card numbers for one-time use: This method for online shopping also comes in handy to prevent automatic subscription renewals. You log into your bank account or card app and generate a new number for one-time use. If a hacker intercepts the number, it won’t work for future purchases anyway, and you still get purchase protection.
Some credit card companies offer account numbers that work for only one online merchant. If you have a specific account number for Store A and a hacker tries to use the number with stores B, C, D, and E, it won’t work.10
On the con side, you do go through a few extra steps. As mentioned earlier, you must log into your bank account or card app and go through the process to generate a one-time number. It’s easier to use Apple Pay or Google Pay, if available. Both use similar principles (Google Pay virtual account numbers and Apple Pay encryption).
Review your credit card statements at least once a month for odd charges. Most providers waive fraudulent charges as long as you notify them in a timely manner.
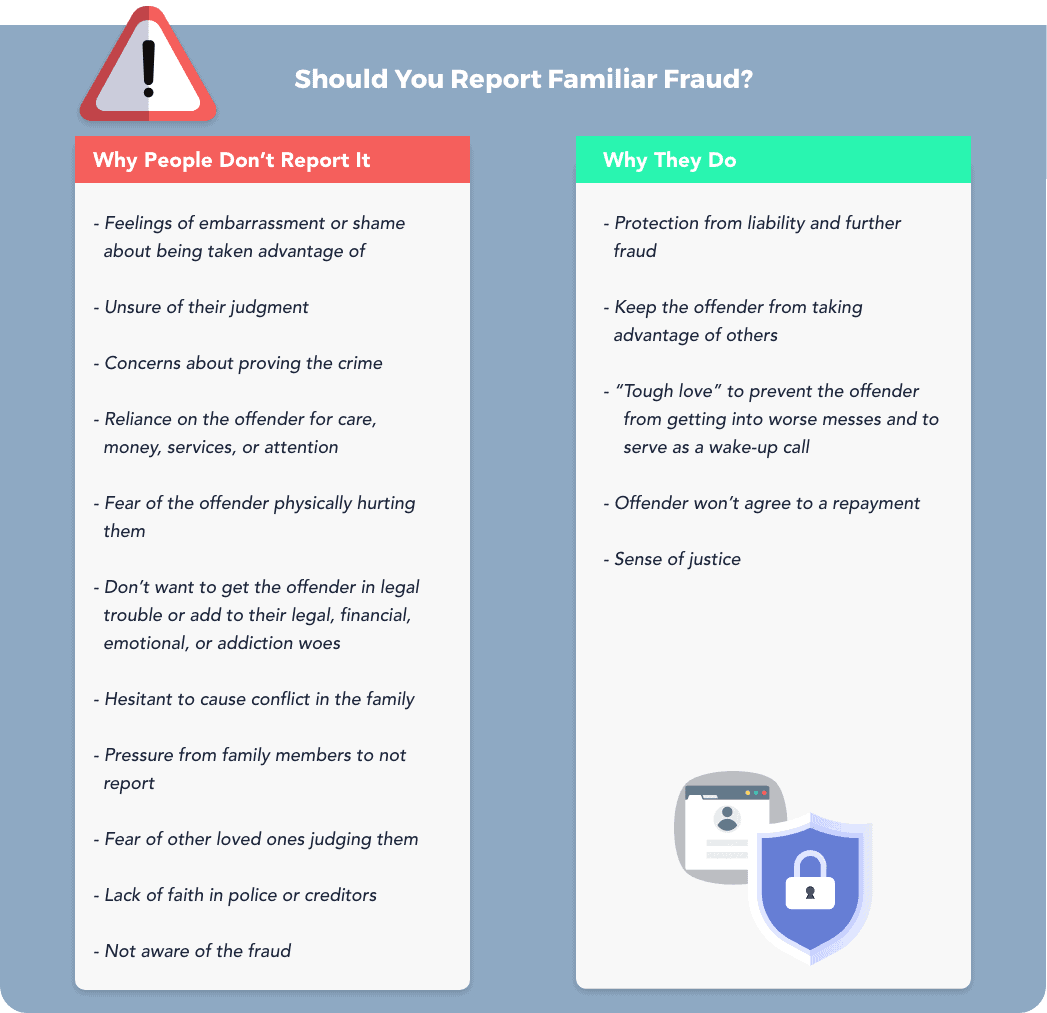
Familiar fraud, also called family member fraud, is very real. Some parents even steal their children’s identity, although not always with malicious intentions. For example, a parent might use a child’s information to procure goods or services that benefit the child. In Juan’s case, perhaps a relative stole his information to qualify for a loan to pay Juan’s bills—but it’s still illegal. Familiar fraud can be committed by relatives, friends, caregivers, co-workers, even neighbors.
The more people who have access to sensitive information, the higher the risk of theft or fraud. Love and trust are major reasons familiar fraud is underreported, overlooked, or plain ignored. It’s hard to inform your mother that your father has been stealing from her for years, or to tell your grandfather that your sister has stolen his identity.
Fraud must be reported to the police to get credit card companies, banks, and other creditors to back off. About three-fourths of victims who know their offenders end up with partial or complete liability since they don’t report the fraud, wait too long to report it, or report it partially.11
Familiar Fraud: Preventing, Recognizing, & Recovering
Preventing
Set up a system with checks and balances if someone handles your finances. Common approaches include multiple family members to keep one another in check or a financial professional.
Secure your computers and mobile devices with biometrics, passcodes, or other digital locks. Keep birth certificates, Social Security cards, passports, checkbooks, and other sensitive documents in protected locations such as lockboxes. Be extra careful around holidays or if you have multiple people in and out of your home.
Freeze your credit, especially if you’re a child, senior citizen, or dependent on others for care. It’s free, and you can lift freezes temporarily to open new accounts.
You can sign up for identity theft protection services but be aware of their limitations. For instance, they cost $10 to $30 a month. Some don’t have fraud alerts with the major credit bureaus or offer money-back guarantees. Still, these services may come in really useful.
Monitor credit reports for odd entries.
Avoid answering calls from numbers you don’t recognize. Keep updated on scams such as fake IRS emails.
Make plans to have your financial affairs looked after if your disabilities temporarily or permanently worsen. Financial advisors, estate planning attorneys, or trusted relatives are possibilities.
Recognizing
Keep track of objects that disappear from the home.
Pay attention to signs of new account activity. Examples include calls from debt collectors, loan application denials, bills for purchases you did not make, and credit card applications in the mail. Common targets for new-account fraud include mortgages, student loans, credit cards, and car loans.
Observe any changes in the lifestyle of those around you. Does a family member or caregiver suddenly have a big- ticket item, or did someone quit their job with no backup plan?
Keep looking for unusual account activity on credit card and bank statements.
Stay alert to certain tells if you’re a loved one or caregiver.
- Worsening disabilities, health, or mental acuity
- “Gatekeeper” relative or caregiver
- A previously distant relative is now close, or a new friend is around too often
- Expenses or transactions the person with the disability cannot explain
- Legal changes such as car title transfers, a new will, new names on financial accounts, and power
of attorney
Recovering
Freeze credit reports and place temporary fraud alerts on your accounts as soon as you realize fraud may have occurred. These immediate steps mitigate further damage while you decide how to handle the situation. Contact companies you have unauthorized accounts with and let them know about the fraud.
(Later, you can get extended, seven-year fraud alerts but must report the fraud to the police.)
Talk with the person you suspect committed the fraud-but only if you feel 100% comfortable doing so and want to salvage the relationship. A conversation may help you understand why your loved one did what they did. It’s also a chance to explain the repercussions of their actions (you face mounting debt, lawsuits, etc.). Consider getting a therapist or other loved ones to support you through the conversation.
If you’re not sure who committed the fraud, you could talk to everyone with access to your information or let the police take over.
Determine your next steps. One avenue is to ask the culprit to repay loans and expenses over time. Get a firm payment plan in place. Meditation or legal assistance can be helpful in creating legally binding and structurally sound agreements.
Alternatively, you could report the crime to the police and give the name of the offender. This approach shows you weren’t part of the fraud and may get creditors to remove liability. Enlist an attorney’s help if creditors won’t remove the fraud despite your best, repeated efforts to clarify what happened.
Another approach is to pay the debts yourself, even if they are costly, not your own, and lower your credit score. You can try working out repayment plans without involving the police, but it’s tough getting creditors to agree. However, some will move the account, so it’s now the culprit’s.14
Some people forgive the perpetrator and move on without requesting restitution. This is more likely when the damage is relatively light and contained.
Get support from therapists or organizations such as the Identity Theft Resource Center.
Identify why and how the fraud occurred. Put safeguards in place to keep it from happening again. For instance, if you have vision loss and your sibling stole information from your phone, one safeguard is to set a fingerprint lock.
Someone with mobility, vision, or hearing issues who has people in and out of the house could install a smart door lock, video doorbell, and cameras. This way, the resident has a better idea of who is/was in the home, where exactly they went, and when they entered.
Accessibility and Digital Security
Digital security, cybercrime, and identity theft are legitimate concerns for anyone, no matter their accessibility needs. However, people with disabilities face increased risk. Part of it is because they may need to give up privacy or have others help with tasks. Accessible tools do foster independence, but the world still lags behind in many respects.
If you’re a family member or caregiver for people with disabilities, encourage independence whenever possible, even if it takes time and research. Helen Keller Services for the Blind is one example of a group that gives people the tools to live, work, and thrive. Similarly, smart home devices such as smart locks cost money but allow people more control over who comes into their home and when. The risk of identity theft and fraud decreases.
View from the Experts: Accessibility and Digital Security
Additional Resources
Dirty Dozen: The Worst IRS Tax Scams
Protect Your Identity: The Identity Theft Resource Center
How to Undo Unauthorized Credit Card Charges by a Family Member: The Fair Credit Billing Act
References and Footnotes
- Justice Department Issues Web Accessibility Guidance Under the Americans with Disabilities Act. (2022, Mar. 18). U.S. Department of Justice. Retrieved May 29, 2022, from https://www.justice.gov/opa/pr/justice-department-issues-web-accessibility-guidance-under-americans-disabilities-act
- Workplace Hearing Loss. (2017, Winter). Hearing Health Foundation. Retrieved October 29, 2020, from https://hearinghealthfoundation.org/hearing-loss-in-the-workplace
- Packer, Lisa. (2017, Aug. 24). Why Aren’t Hearing Aids Covered by Insurance? Healthy Hearing. Retrieved October 29, 2020, from https://www.healthyhearing.com/report/52484-Why-aren-t-hearing-aids-covered-by-insurance
- Cochlear Implants: Frequently Asked Questions. (Updated 2017, Dec. 29). U.S. Food and Drug Administration. Retrieved October 29, 2020, from https://www.fda.gov/medical-devices/cochlear-implants/frequently-asked-questions#l
- Mroz, Mandy. (Reviewed 2020, April 17). Used Hearing Aids. Healthy Hearing. Retrieved October 29, 2020, from https://www.healthyhearing.com/help/hearing-aids/used
- Faustino, Daniella, and Girouard, Audrey. (2018, October). Understanding Authentication Method Use on Mobile Devices by People with Vision Impairment. PDF. Retrieved October 29, 2020, from https://cil.csit.carleton.ca/b/wp-content/uploads/2018/07/fp017-briotto-faustinoA.pdf
- (ASL) – YouTube Video Text Script – Tax Scams via Video Relay Service. (2023, May 01). IRS. Retrieved Sept. 14, 2023, from https://www.irs.gov/newsroom/tax-scams-via-video-relay-service-asl-youtube-video-text-script
- Part 64 – Miscellaneous Rules Relating to Common Carriers. (Current as of 2023, Sept. 14). Electronic Code of Federal Regulations. Retrieved Sept. 14, 2023 from https://www.ecfr.gov/current/title-47/chapter-I/subchapter-B/part-64
- Accessible Payment Systems for People with Visual Impairments. (n.d.). American Foundation for the Blind. Retrieved October 29, 2020, from https://www.afb.org/blindness-and-low-vision/using-technology/online-shopping-and-banking-accessibility-people-visual-2
- Braverman, Beth, and Staples, Anastasiia. (2020, October 19). Virtual Account Numbers Grow as a Way to Cut Fraud Risk. CreditCards.com. Retrieved October 29, 2020, from https://www.creditcards.com/credit-card-news/credit-card-virtual-account-numbers/
- Sell, Sarah. (2019, Dec. 04). Financial Fraud More Fraught When Perpetrator Is Known. Associated Press. Retrieved October 29, 2020, from https://apnews.com/article/28d93ce1272f9f82a383e61a13fc4f0e

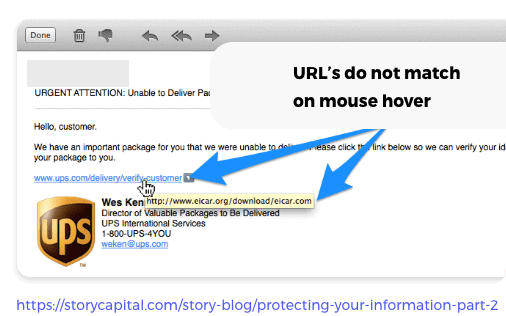 Watch for certain tells. Greetings such as, “Dear Customer,” or “Hello, customer,” signal an email that isn’t legit. Poor grammar can be a tell too, but there are some scam emails using good grammar. Hover over links to see if they seem genuine. To do this on a smartphone, hold your finger down on the link until a small window giving the full link address pops up. You can usually tell from this full address if a link is legit. Phone accessibility features such as voice control and screen readers may be helpful.
Watch for certain tells. Greetings such as, “Dear Customer,” or “Hello, customer,” signal an email that isn’t legit. Poor grammar can be a tell too, but there are some scam emails using good grammar. Hover over links to see if they seem genuine. To do this on a smartphone, hold your finger down on the link until a small window giving the full link address pops up. You can usually tell from this full address if a link is legit. Phone accessibility features such as voice control and screen readers may be helpful.