The Ultimate Phishing Protection Guide For 2026
Learn how to recognize, prevent, and respond to phishing attacks with tips from our cybersecurity experts.
Phishing attacks are not only increasing every year, but they are also getting more sophisticated.1 Hackers are now using AI to craft convincing messages from banks and government departments. Others build websites with security certificates to make them look legitimate. Many cybercriminals are even launching multi-channel phishing attacks across SMS, email, and social media.
How do you avoid becoming a victim? Our team of cybersecurity experts has put together this guide to help you identify the most common types of phishing attacks, the tools you can use to protect yourself, and what to do if you fall for a scam. Here’s everything you need to know.
>> More Resources: Phishing Text Messages: A Guide to “Smishing”
What is Phishing?
Phishing is a cybercrime where scammers impersonate legitimate organizations to steal sensitive information from unsuspecting victims. According to the FBI’s Internet Crime Report, phishing was the most reported cybercrime in 2024, with over 190,000 complaints.2 These aren’t just random attacks. Modern phishing campaigns are sophisticated, targeted, and difficult to spot.
Phishing protection matters more than ever because so much of our daily life happens online. From banking to healthcare, shopping to socializing, our digital footprint contains valuable data that criminals desperately want. A single successful phishing attack can lead to identity theft, financial loss, or even ransomware infections that lock you out of your own files.
>> Read More: Identity Theft Prevention: Tips and Techniques for 2026
Common Types of Phishing Attacks
The best place to start is to understand the different types of phishing attacks cybercriminals use to steal your information. Here’s a breakdown of the most common.
| Type of Phishing | Primary Channel | Example |
|---|---|---|
| Email phishing | Attackers send mass emails from trusted companies like Amazon, Microsoft, or your bank, creating urgency (“Your account will be closed!”) or offering something too good to be true (“Click here to claim your $500 gift card!”). | |
| Spear phishing | Attackers research specific individuals or companies, crafting personalized messages that reference real colleagues, projects, or recent events. | |
| Smishing | SMS/Text | These messages often claim the recipient has won a prize, has a package delivery issue, or needs to verify their bank account immediately. |
| Vishing | Phone calls | Scammers impersonate tech support, government agencies, or utility companies to extract information or gain remote access to your computer. |
How to Spot a Phishing Attempt
Once you know how to spot a phishing attempt, the scams become obvious. These are the telltale signs you should look for.
Unusual Sender Addresses
Legitimate companies use official domain names in their email addresses. For example, if Amazon emails you, it comes from @amazon.com, not @amaz0n-security.net. We recommend hovering over the sender’s name to reveal the actual email address. Phishers often use display names that look legitimate while hiding sketchy addresses underneath.
>>Find Out: How to Stop Spam Emails
Grammar and Spelling Errors
Major corporations have professional communication teams that carefully craft correspondence. If you receive an email from “Microsoft” with random capitalizations or obvious typos, it’s probably not from Microsoft.
FYI: Hackers are turning to AI to generate fake emails, which are harder to spot, even for experts. Researchers found that 68 percent of cyber threat analysts struggled to detect them.3
Urgency and Threats
Phishers use deadlines to pressure people into making poor decisions. Any messages claiming “Act within 24 hours or your account will be deleted!” or “Immediate action required!” should raise red flags. In our experience, real companies give reasonable time frames and multiple warnings before taking drastic action.
Pro Tip: Legitimate organizations never ask for passwords, Social Security Numbers, or credit card details via email or text message.
Suspicious Links and Attachments
Before clicking any link, hover your mouse over it to preview the destination URL. If the link shows chase.com but hovering reveals bit.ly/x7y9z, that’s a massive red flag. We also recommend never opening attachments, especially .zip, .exe, or .scr files, without verification from antivirus software.
>> Find Out: The Best Antivirus Software of 2026
Generic Greetings
Companies you do business with know your name. Emails starting with “Dear Customer” or “Valued Member” instead of your actual name often indicate mass phishing campaigns. This isn’t always the case. Spear phishing is the exception, as it uses real names, which is why you should treat the greeting as only one clue among many.
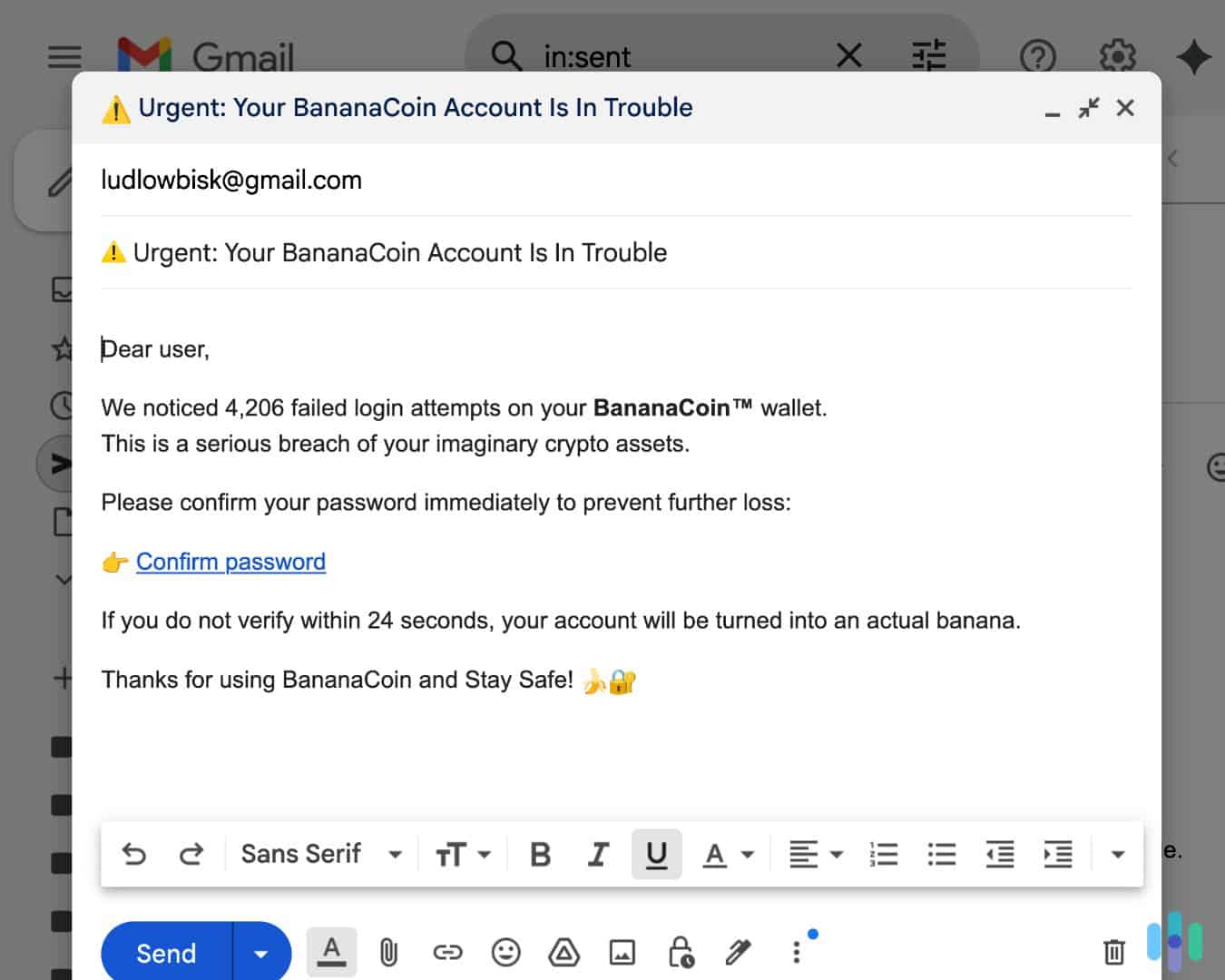
Phishing Protection Tools and Techniques
Spotting phishing is just the first step. To stay safe, you need multiple layers of defense. Here’s what our experts recommend:
- Install antivirus software: We recommend using apps like Norton Antivirus or TotalAV to protect your devices from phishing and malware. Some of the best programs use AI to detect threats and block attempts before they reach you.
- Enable multi-factor authentication (MFA): Even if someone steals your password, MFA requires a second step. It’s usually a code from your phone or an authenticator app to log in.
- Use a password manager: Apps like RoboForm and Keeper securely store your passwords and create strong, unique ones for every account. That way, a single compromised password won’t put your others at risk.
- Turn on spam filtering: Email filters help block suspicious messages, while call-blocking apps can protect you from phishing calls.
- Consider identity theft protection: Services like LifeLock and Aura monitor your personally identifiable information online. You’ll receive alerts for unusual activity, and get assistance in recovering compromised accounts.
- Remove personal information from data brokers: Limiting what’s publicly available makes it harder for scammers to target you with personalized phishing attempts. We recommend signing up to services like Incogni or DeleteMe.
Using these tools together builds a much stronger defense. No method is foolproof, but we recommend layering your protection to make phishing attacks against you far less likely to succeed.
What to Do If You’ve Been Phished
If you clicked a link or shared information by mistake, don’t panic. Quick action can minimize damage and sometimes prevent real harm. Here’s what to do:
- Disconnect and change passwords immediately: If you downloaded anything suspicious, disconnect from the internet to stop malware from spreading. We also recommend updating your passwords for any accounts that might be compromised.
- Contact your bank or credit card company: If you entered credit card information, call your bank’s fraud department right away. They can freeze or monitor your accounts to prevent unauthorized charges.
- Document everything: Take screenshots of phishing emails, any websites you visited, and any responses you sent. Forward these details to reportphishing@apwg.org and the impersonated organization. Documentation helps with fraud reports, insurance claims, and potential law enforcement action.
- Place fraud alerts and monitor activity: Add fraud alerts to your credit reports via Experian, Equifax, or TransUnion. It’s free and makes it harder for criminals to open accounts in your name. We also suggest keeping an eye on bank statements and medical insurance claims for unusual activity.
- Scan and strengthen your defenses: Run full antivirus scans on all devices, enable multi-factor authentication on critical accounts, and consider subscribing to a credit monitoring or identity theft protection service.
Phishing attacks can fool even security experts. If you get caught, review what happened, strengthen your security habits, and treat it as a learning opportunity to prevent future incidents.
>> Find Out: How to Prevent the Latest Online Scams
Wrap Up: Protect Yourself
Phishing protection isn’t about being paranoid. It’s about being prepared. The steps we provided in this guide are designed to reduce or eliminate vulnerabilities. No security measure is perfect, though. That’s why we recommend using layered defenses, having a healthy skepticism, and using the best security tools to lower your risk.
You can start simple by enabling multi-factor authentication on your most important accounts or changing your passwords to make them harder to guess. We also recommend installing antivirus software and using a data removal service to reduce the amount of personal information online. You can also consider identity theft protection services, VPNs, and password managers that can keep your data secure. The more steps you take to protect yourself, the better your chances of avoiding a phishing attack.
Frequently Asked Questions
-
Can phishing attacks infect my computer without clicking anything?
While rare, automatic downloads can occur when visiting compromised websites. Most modern browsers and operating systems have strong protections against this. We recommend keeping your software updated and using reputable antivirus to minimize this risk.
-
Are mobile devices safer from phishing than computers?
Mobile devices face unique risks through SMS phishing and malicious apps, making them equally vulnerable. Both platforms require vigilant security practices and protective software.
-
How often do companies legitimately ask to verify account information?
Legitimate companies rarely request verification through email and never ask for passwords or full credit card numbers. If you’re in doubt, we suggest reaching out to the company directly through official channels or phone numbers posted on their website.
-
Can phishing protection software catch all phishing attempts?
No software catches 100 percent of phishing attempts, especially new or highly targeted attacks. Combining software protection with awareness provides the best defense.
-
Should I report phishing attempts to law enforcement?
Yes. Report phishing to the FTC at ReportFraud.ftc.gov and forward phishing emails to reportphishing@apwg.org. Local law enforcement typically only gets involved if you’ve suffered significant financial loss.
-
Is it safe to unsubscribe from suspicious emails?
Never click unsubscribe links in suspicious emails as this confirms your email is active. Instead, mark it as spam and let your email provider’s filters handle it.
-
Infosecurity Magazine. (2024). Phishing Attacks Double in 2024.
https://www.infosecurity-magazine.com/news/2024-phishing-attacks-double/ -
FBI. (2024). Internet Crime Report 2024.
https://www.ic3.gov/AnnualReport/Reports/2024_IC3Report.pdf -
SQ Magazine. (2025). AI Cyber Attacks Statistics 2025: How Attacks, Deepfakes & Ransomware Have Escalated.
https://sqmagazine.co.uk/ai-cyber-attacks-statistics/
