Account Takeover Fraud:
A Consumer’s Guide to Protecting Yourself
If you’ve ever had a social media profile start making strange posts or send out strange messages to your friends, you have been the victim of an account takeover attack. Often, this is just an annoyance that you solve by changing your password. However, an account takeover can have devastating consequences for you and those around you.
Even worse, this type of cyber attack is fairly common. According to our research, about 20 percent of all adults have been the victim of an account takeover. The following guide can help you avoid this type of attack.
some red flags to look out for, and how to protect yourself.
How Does Account Takeover Happen?
There are a few different ways that account takeovers can occur, as well as many different types of accounts that can be affected.
Techniques
The most common ways that hackers steal someone’s credentials and take over their accounts are:
- Credential stuffing / card cracking: Data breaches happen all the time, with usernames and passwords being two of the most common types of data leaked or sold on the dark web. Hackers use bots to test different credential combinations on multiple sites until they are successful. Even if they have just a username, they can still use bots to match usernames with common passwords (e.g. “1234567890”). This process is also called card cracking.
- Gift card fraud: Bots try to use millions of online gift cards until they find ones with balances.1
- Weak passwords: Unfortunately, many accounts are so easy to crack because of their old, weak, or repeated passwords. In fact, 45 percent of Americans use passwords that are eight characters or fewer, according to our research on password usage, which makes it much easier for bots to guess correctly.
- Hacking: For account takeovers specifically, the most common type of hacking is a brute-force attack in which an automated script tries many password combinations. These types of hacks are also called botnets.
- Phishing: Phishing typically comes in the form of emails, texts, or attachments containing links to fake websites that mimic legitimate ones. Through social engineering, phishing websites get users to log in to what they think is a real website, giving the hackers their credentials unknowingly. Spear phishing is particularly hard to detect, as it’s highly targeted and seemingly realistic.2
Types
While any type of account can be taken over, these are the most common account types for it:
- Financial: Financial ATO involves the theft of consumer funds. Checking, savings, and credit card accounts are all common targets.
- Retail: As e-commerce continues to grow, more hackers are gaining access to retail accounts, where they can make purchases as well as sell items that they’ve purchased fraudulently.
- Travel: Hackers can steal frequent flyer miles from customers without their knowledge.
- Government benefits: Even Medicare and similar programs’ accounts aren’t safe from ATO.
- Wireless phone contracts: Cybercriminals can take control of wireless phone contracts, calling people and receiving calls and texts on the phone owner’s dime.
- Store loyalty rewards: Many hackers steal from store loyalty programs, using customers’ points for their own purchases.3
Why It’s Hard to Detect
There are a few reasons why account takeover is so hard to detect aside from the fact that it’s a relatively new cybercrime.
- Good customers: For bank accounts especially, companies want to reward people they consider to be “trustworthy” customers by not interfering with their spending, which may lead to missing fraudulent behaviors or transactions.
- Botnets and proxies: Since the hackers aren’t doing the takeover themselves but rather are using bots and proxies, they program them to mimic common login behaviors. Something as simple as logging in at a certain time can help bypass bot detectors.
- CAPTCHA workarounds: Many of these bots can get around CAPTCHA challenges automatically.
- More e-commerce: E-commerce transactions are at an all-time high. However, the more online transactions there are, the more opportunities for fraud, and with the rise of VPNs and proxies, hackers can easily mimic a user’s location, attacking during peak activity times.
- Frictionless UX: In attempts to make users’ experiences on websites as frictionless as possible, many transactions can now be completed in one click. However, excellent user experience (UX) can come at the cost of security, as users may skip security questions or CAPTCHA.
- Different teams: Finally, preventing account takeovers can fall to many different teams within the same business, from the security team to the fraud prevention, e-commerce, and customer support teams. This disjointed structure can slow response to potential account takeovers.4
Who Does Account Takeover Target?
The truth is that account takeover can happen to anyone, whether you’re an individual, a small business, or a large enterprise. But why do hackers take over accounts in the first place?
Goals
These are some of the many reasons why cybercriminals take over accounts aside from pure monetary gain:
- Phishing: Some account takeovers are merely stopovers in larger phishing campaigns.
- Dark web sales: Rather than perform any actions in users’ accounts, some criminals simply sell their credentials on the dark web, the black market of the internet.
- More account takeovers: Just as bankers invest in stocks to make more money, some cybercriminals take over accounts in order to take over more accounts, keeping their proverbial production lines moving.
- Fraudulent transactions and transfers: Of course, we can’t gloss over the straightforward reason why account takeovers occur: money.
- Reputation damage: Finally, some criminals seek to damage the reputation of individuals or businesses, often for personal reasons.5
Account takeovers target both businesses and individuals. According to our research on the account takeover market, only 13 percent of account takeovers were of business accounts, while 80 percent were personal. Another 7 percent covered both business and personal accounts.
Businesses
Research from the cybersecurity firm Deduce found that one-third of account takeovers are of bank accounts specifically, which includes both financial services and financial technology accounts. Second to financial institutions are online retailers, particularly those with one-click payment systems. However, as we mentioned earlier, account takeover can happen to any company, regardless of location, size, and industry.6
Individuals
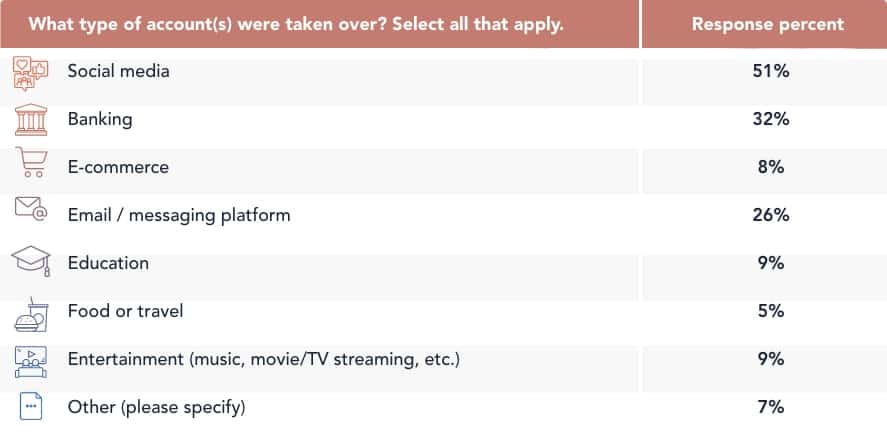
A sobering 32 percent of ATOs targeting individuals were bank accounts. However, the majority of personal account takeovers were actually social media accounts, at 51 percent. Email and messaging platforms followed third at 26 percent.
We also observed some trends about the kind of person likely to be targeted for this cybercrime.
- Device type: Androids are most likely to have account takeovers at 29 percent of all takeovers, followed by iOS devices at 21 percent.
- Age: As a user’s age increases, so does the likelihood of account takeovers. While 75 percent of those 45 and older have had accounts taken over, only 69 percent of 18- to 29-year-olds have had accounts taken over.
- Household income: While there are no overarching trends connecting account takeovers and household income, the most likely group to experience account takeovers was those with household incomes between $25,000 and $49,999 at 28 percent.
- Gender: Males and females are equally likely to fall victim to account takeover at 22 percent each.
- Region: Again, there were no strong trends connecting account takeovers and regions, but the most likely regions for ATOs were New England at 34 percent, West South Central at 28 percent, and South Atlantic at 26 percent. At this point, it’s unclear why the rates are higher in these regions; to find out the cause of the correlation, we would need to perform additional research.
Consequences of Account Takeover
No matter the victim, account takeover has consequences in terms of money, time and reputation.
Businesses
With customers, employees, and more money involved, account takeover is worse for businesses than it is for individuals. Its consequences include:
- Loss of business: Nearly one-third of consumers said they’d stop using a business if their accounts have been compromised.7 Account takeover can lead to a high churn rate — not ideal for businesses hoping to grow or at least maintain their customer bases.
- Reputation damage: With financial institutions especially, one of the consequences of account takeover may be a business’s loss of its good reputation.
- Loss of funds: While it depends on the size of the business and its revenue, monetary losses from account takeovers can range from thousands to several millions of dollars. Worse, they may not be covered by the bank’s insurance policy.8
- More chargebacks: As fraudulent charges occur, customers will initiate more chargebacks, which could end up raising payment providers’ processing fees by millions. In 2019, chargebacks caused 75 percent of e-commerce losses from fraud.
- More transaction disputes: Similarly, more customers will dispute their transactions, which can lose businesses time and money.
>> Also check out: What Can Someone Do With Your Phone Number?
Individuals
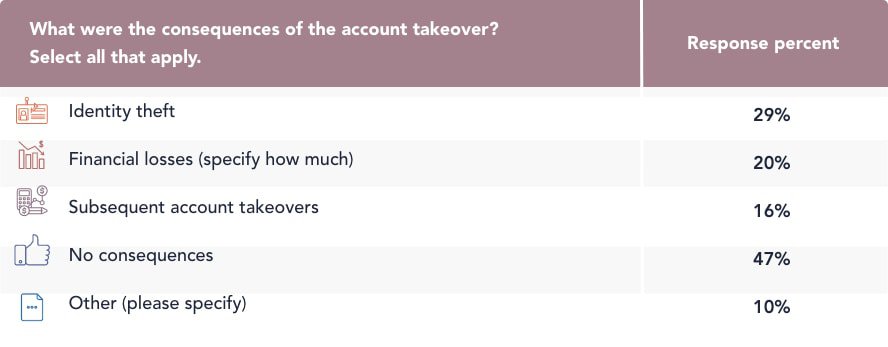
Our research on account takeovers shows that the most common consequence for individuals was identity theft at 29 percent. The average financial loss per victim was nearly $12,000.
On a brighter note, 82 percent of victims were able to recover the taken-over accounts. Moreover, 81 percent of these recoveries occurred within the week of the takeover, so although account takeover has its consequences, most people were able to recover quickly.
How to Avoid Account Takeover
There’s no single action that can prevent account takeover, guaranteed. In fact, 62 percent of personal account takeover victims had either security questions, advanced authentication, or both features on the affected accounts, according to our research. However, by following some best practices in digital security, businesses and individuals can reduce their risk of account takeovers.
Businesses
For businesses with online account systems, there are a number of methods you can implement into your login system to prevent unauthorized access.
- Login attempt limits: Simply by limiting the number of login attempts before an account locks, you can effectively guard against bot spamming, even if it uses multiple IP addresses.
- Device tracking: You can also track login attempts and their locations automatically.
- Employee education: Preventing account takeovers isn’t just about programming. You also need to train your employees on how to recognize phishing attempts, compromised accounts, etc.
- IP block listing: Since many bots use the same IP addresses, you can block certain addresses to combat botnets.
- Sandboxing: If an account looks suspicious, you should be able to quarantine it in a sandbox so it won’t affect the rest of your digital infrastructure.
- WAF configuration: A WAF, or web application firewall, can recognize account takeover attempts as well as signs of brute-force attacks and botnets.
- Account takeover prevention software: To automate the process of detecting account takeovers, you can use software created for this purpose exactly, such as Deduce or SpyCloud.
Individuals
Again, while none of these methods can prevent account takeover on their own, combining all of them will greatly reduce the likelihood.
- Password hygiene: It’s important that each of your online accounts has a strong, unique, and complicated password. Wondering if your password is up to our standards? See how secure your password(s) are. On a related note, we’ve created a guide to prevent online identity theft as well.
- Security questions: Although they’re not great for user experience, security questions are an easy way to prevent unauthorized access. Just make sure the answers aren’t super obvious or Googleable.
- Authentication:Additionally, you should enable two- or multi-factor authentication when it’s available. MFA requires you to do more than just enter a password – you have to enter a security code, provide biometric data, or both to access your account.
- Antivirus software: Antivirus software scans devices for suspicious behaviors and files that may indicate or cause account takeovers, such as keyloggers that log keystrokes when entering credentials for an online account.
- VPNs: VPNs encrypt your devices’ IP addresses as well as your web activity, making it harder for hackers to steal your credentials and take over your accounts.
- Identity theft protection: Identity theft protection services scan multiple criminal, financial, and credit areas for signs of fraud, including ATO.
Signs of Account Takeover
Sometimes, even the best prevention isn’t enough to stop account takeovers. If you’re unsure whether an account has been taken over or not, here are some red flags:
- Chargeback requests and claims of fraudulent transactions: If you’re getting an unusual number of chargeback requests and fraudulent transaction claims, that could be a sign of account fraud.
- Login attempts and password reset requests: Hundreds of login attempts or password reset requests indicate botnets, credential stuffing, and card cracking.
- New account information: If your account has newly saved shipping or credit card information, someone else may have been in your account.
- Rewards points: Fewer reward points in your account can indicate account takeover, if you haven’t used them yourself.
- Unfamiliar transactions: Any unfamiliar bank or card transactions are suspicious as well.
What to Do if You’re a Victim of Account Takeover
If the above warning signs pointed to yes, it’s time to recover from ATO. While ATO has its consequences, recovery is possible, whether you are a business or an individual.
Businesses
- Recover the account. First, freeze the affected account(s) and force a password reset.
- Alert the customer. Next, alert the customer that their account has been taken over, but be careful about your language. Words like “freezing” or “securing” accounts sound much better than words like “compromised” or “taken over.9
- Report it to government agencies. Report the fraud to the proper federal, state, and local authorities.10
Individuals
- Contact the company. Contact either the company or the institution behind the affected account and tell them that your account has been taken over, if they’re not already aware.
- Alert your contacts. Some hackers send spam or phishing messages from the accounts they take over, so warn your contacts not to click on these fraudulent messages.
- Update software. Perform all software updates as soon as they’re available, as they might contain patches for security vulnerabilities.
- Install antivirus software. Better late than never! Antivirus software might be able to quarantine any viruses or malware and detect suspicious behaviors, which could help you deal with a device that’s been taken over along with your account.
- Review accounts. Especially if you use the same password for multiple accounts, check your other accounts, particularly social media accounts, for signs of compromise.
- Change passwords. Along with your passwords, change your PINs and security questions across all of your accounts. Make sure that each account has a unique and complicated password combining letters, numbers, and special characters.
- Set up authentication. Again, whenever it’s available, set up two- or multi-factor authentication on your accounts.
How Common Is Account Takeover?
Our research found that 22 percent of U.S. adults had experienced account takeover. However, research from Sift found that number to be 25 percent, so we estimate that account takeover affects 22 to 25 percent of U.S. adults.
Unfortunately, account takeover is on the rise, increasing by 250 percent from 2019 to 2020. Discounts on dark web data of up to 90 percent as well as discounts on botnet time of up to 50 percent fueled this increase, according to Deduce.11
Account Takeover Statistics
Here are the most important facts and figures about account takeovers, from both our original research and third parties.
Our Research
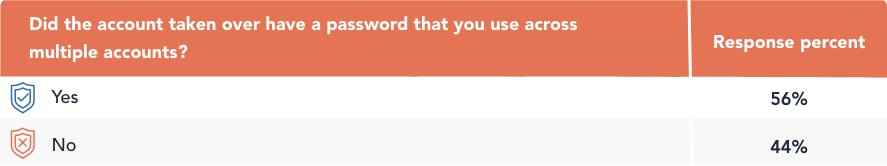
Our research indicates that the majority of account takeover victims, 56 percent, had used the same password of the affected account on other accounts, which puts those accounts at risk as well.
Much to our concern, 62 percent of victims already had security questions, advanced authentication, or both turned on when their accounts were taken over, indicating that these measures alone aren’t enough to prevent account takeover.
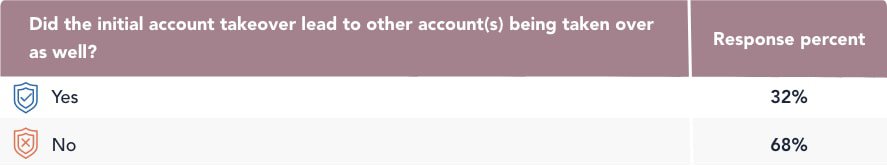
On a more positive note, 68 percent of account takeover victims only had one account taken over, while 32 percent had other accounts taken over as a consequence of the initial account takeover.
Third-Party Research
Research from third parties answered some of our biggest questions about account takeover and its consequences:
- In 2020, identity theft reports regarding email or social media accounts increased by 36 percent year over year, while reports regarding online shopping or payment accounts increased by 38 percent.12
- 52 percent of U.S. adults are concerned about future account takeovers, and 25 percent have already experienced ATOs themselves.
- Of those account takeover victims, 49 percent had it happen once, 41 percent had it happen one to five times, and 10 percent had it happen more than five times.
- Digital e-commerce businesses saw increases of 195 percent in account takeover attempts, while physical e-commerce stores saw an 85 percent increase.13
- Javelin Strategy’s Identity Fraud Study.14 found that the loss rate from account takeovers increased by up to 72 percent, as technological advances made social engineering easier.
- 40 percent of all account takeover fraud activity occurs within a day of the initial takeover.
Recap
Although account takeovers are on the rise, with awareness comes preparation and prevention. Use antivirus software. Practice good password hygiene. Monitor your accounts.
If your account has already been compromised, all is not lost. Act fast to recover your account. There’s still time to minimize your monetary loss and avoid identity theft.
Sources
- https://www.netacea.com/what-is-account-takeover/
- https://risk.lexisnexis.com/insights-resources/article/account-takeover-fraud
- https://www.accertify.com/resource/account-takeover-protection-how-do-you-stop-ato-attacks/
- https://nudatasecurity.com/resources/blog/what-is-account-takeover/
- https://pages.sift.com/rs/526-PCC-974/images/ebook_FINAL_Q4%202020%20Digital%20Trust%20%26%20Safety%20Index_121620.pdf
- https://colony.bank/corporate-account-takeover
- https://www.ravelin.com/insights/account-takeover-fraud
- https://onerep.com/blog/account-takeover-fraud-everything-you-need-to-know-about-prevention-detection-and-recovering-after-an-attack
- https://news.crunchbase.com/news/deduce-raises-7-3m-to-secure-customer-identity/
- https://www.ftc.gov/system/files/documents/reports/consumer-sentinel-network-data-book-2020/csn_annual_data_book_2020.pdf
- https://pages.sift.com/rs/526-PCC-974/images/ebook_FINAL_Q4%202020%20Digital%20Trust%20%26%20Safety%20Index_121620.pdf
- https://www.javelinstrategy.com/coverage-area/2020-identity-fraud-study-genesis-identity-fraud-crisis