Perfect Privacy VPN Review
Perfect Privacy features a kill switch, torrenting on most servers and split tunneling through up to four different servers.
 Aliza Vigderman, Senior Editor, Industry Analyst
&
Aliza Vigderman, Senior Editor, Industry Analyst
&
 Gabe Turner, Chief Editor
Last Updated on May 28, 2024
Gabe Turner, Chief Editor
Last Updated on May 28, 2024
What We Like
- Based in Switzerland: The company's location means it's not part of any international surveillance alliances, a clear good sign.
- No logging: Perfect Privacy won't keep track of any of your activity, a given of any solid VPN.
- Kill-switch: Even if your connection to the VPN is lost, Perfect Privacy will make sure your windows are killed, protecting your data.
What We Don't Like
- Expensive: Perfect Privacy's subscription options start at $10, compared to the $3 of many of their competitors' lowest options.
- Speed on Windows: With a latency increase of over 160%, I can't recommend Perfect Privacy to Windows users.
Bottom Line
When it comes to selecting a VPN, it can be hard for the average computer user to determine what’s what. Of course, you want a VPN that’s going to protect your web traffic, but you also want a VPN that’s not going to significantly slow down your Internet. The days of dial-up are over, and I for one do not want to go back. What’s the average consumer to do?
In this review I’m going to be taking a look at the Switzerland-based Perfect Privacy. I’m going to take a look at the pros and cons, the features the VPN offers including the types of encryption it uses as well as its protocols. Then, I’m going to put Perfect Privacy to the test by buying a subscription for myself to make sure it’s viable for everyday use. I’ll finish up by summarizing Perfect Privacy’s subscription options, customer support, and its mobile app. We have a lot to cover, so let’s get started.
Features
| Log Data | No |
|---|---|
| Kill Switch | Yes |
| Split Tunneling | Yes |
| Netflix | No |
| Torrenting | Yes *Excludes servers in U.S. & France |
Overall Rating
- Based in Switzerland outside of international surveillance alliances
- Strict no data logging policy
- Split tunneling through up to four different servers
What Perfect Privacy Is Up Against
Before diving deeper into our findings about Perfect Privacy, we’ll show you what it’s up against. Our three highest-rated VPNs right now are NordVPN, Surfshark, and Private Internet Access, all of which offer affordable prices (as low as $2.19 per month), a complete feature set with best-in-class encryption and tunneling using 256-bit AES and the protocols OpenVPN and WireGuard. Check them out below:
Video Review
About Perfect Privacy
So let’s talk a little about geography and what it has to do with your VPN. Some services have thousands of servers located all across the globe, meaning that your performance is going to be supported as best it can. Unfortunately, Perfect Privacy isn’t one of those services. It only has 55 servers in 23 counties, so you’re going to want to make sure there are locations near you before you purchase. Otherwise, you’ll be stuck with slow speeds.
The good news is that Perfect Privacy is located in Switzerland, which is not part of any international data-sharing alliances. This helps protect you from snooping government agencies. A lot of the VPN’s I’ve reviewed can’t say the same, so bonus points here.
Perfect Privacy Features
Now I want to get into the nitty gritty of the VPN itself. Strap in, folks!
Will Perfect Privacy Log My Data?
Perfect Privacy does not log any data except for users’ usernames and passwords, plus the email addresses they provided with their account and the account’s expiration date. What they won’t keep is any information about your traffic or VPN activity, which is what matters.
Does Perfect Privacy Have A Kill Switch?
Perfect Privacy does have a kill switch, also referred to as a network lock feature. The kill switch will make sure everything is “killed” if you lose network connection, meaning your websites and applications will close. That way, you’ll retain your privacy even if the VPN crashes for whatever reason.
What Kind of Tunneling does Perfect Privacy Offer?
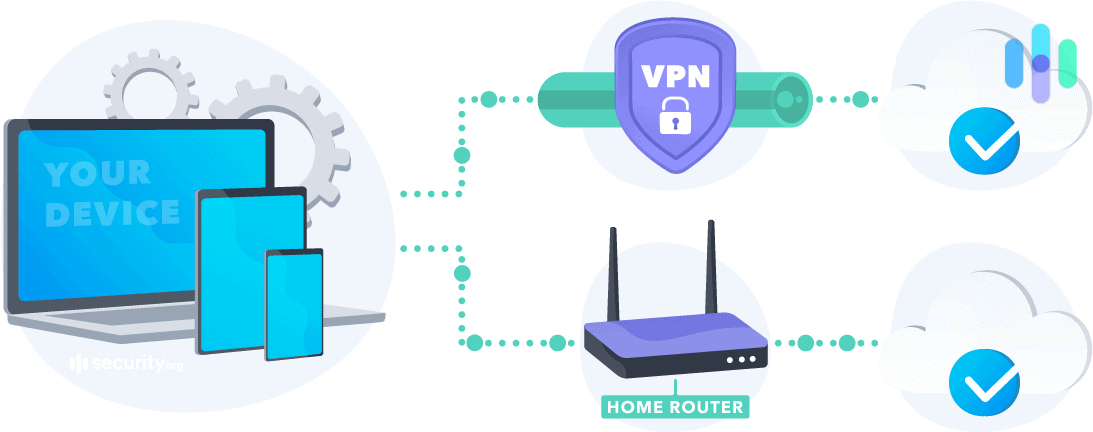
Perfect Privacy offers split tunneling, meaning you’ll be able to access a public and private network simultaneously. It also reduces bandwidth, an added bonus.
NeuroRouting
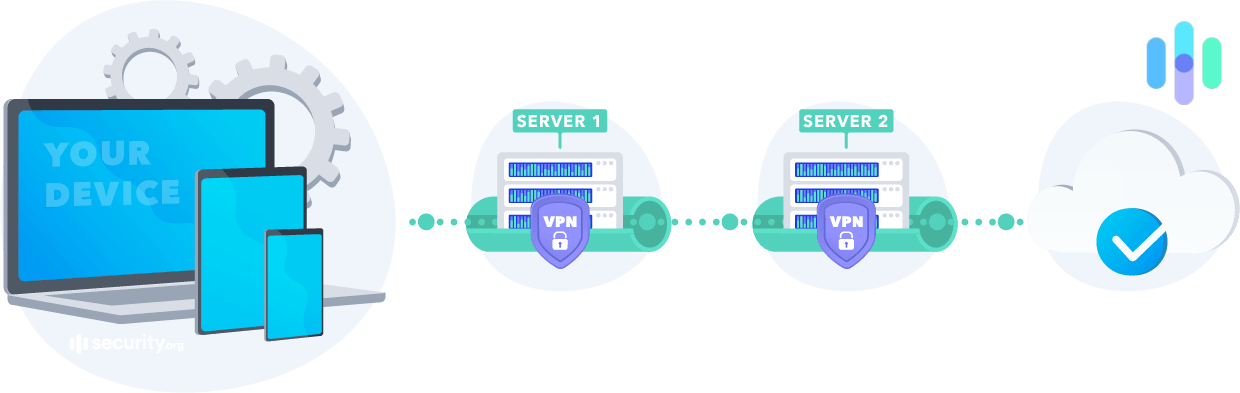
Let’s talk about hops, and no, I don’t mean beer. A double-hop or multi-hop VPN basically means that your data will travel through two or more VPN servers before connecting to the Internet. Rather than simply travel through the VPN server, the data is “cascaded” through multiple servers. The problem with only using a single server is that people can more easily correlate the unencrypted traffic to the encrypted traffic, comparing data like timestamps, the amount of data transferred, the VPN server’s IP address, etc. With more layers of encryption, data becomes harder to extract— think of it as a tunnel within a tunnel, if that doesn’t make you too claustrophobic.
Perfect Privacy’s version of double-hop is called NeuroRouting. It uses “artificial intelligence and algorithms” to determine the next hops, creating unpredictable and ever-changing routes for the data. I have to say, I’m excited about this additional level of security.
Perfect Privacy Alternatives: If Perfect Privacy VPN isn’t making an impression, check out other VPN reviews from Security.org, including SurfShark, Norton, CyberGhost, and Mozilla.
TrackStop
Perfect Privacy’s TrackStop not only blocks ads but also protects your computer from malware, phishing domains, and ransomware. TrackStop also allows people to block out specific content that that may think is inappropriate, like pornography, violence, or social media. There’s even a filter to block out “fake news” from untrustworthy sites.
Finally, TrackStop protects users from browser fingerprinting. Browser fingerprinting is taking information visible when a person uses a website. You may have never thought about it before, but even if you’re incognito, there’s a lot of information available whenever you visit a website: your browser and operating systems types and versions, screen resolution, plug-ins, time zones, languages, hardware configurations, and more.
Believe it or not, only about one in several million people will have the same browser fingerprint as you, so this information could be very useful to a smart hacker. TrackStop prevents browser fingerprinting both with and without use of your VPN. It seems like they’ve thought of everything, and I’m definitely feeling impressed.
Can I Use Netflix with Perfect Privacy?
While Perfect Privacy itself doesn’t have any restrictions against Netflix, whether or not you’ll actually be able to stream it is a bit of crapshoot. Netflix is constantly updating its list of banned VPN IP addresses, so there’s a very good chance you won’t be able to stream.
“We are not the classic streaming VPN,”
said Christian Schmidt, a member of Perfect Privacy’s marketing team. Instead, he explained, Perfect Privacy focuses on privacy. Let’s talk more about encryption.
Perfect Privacy Encryption
Encryption means turning your data into inscrutable code to keep it safe from unwanted eyes. Perfect Privacy uses AES-256, the industry standard for encryption. All IP addresses are anonymous and shared by all Perfect Privacy members, although you might sometimes get the same IP address on reconnection. Keep in mind that the DNS, or domain name server, is also anonymous.
Now let’s talk about how Perfect Privacy encrypts your data.
IPSec
IPSec is used in combination with other encryption methods. It comes in two modes— either encrypting the data packet message itself with transport mode or encrypting the entire data packet with tunneling mode.
That’s it for encryption methods.
Perfect Privacy Protocols
Internet protocols determine how data is transmitted through a network. It’s like different paths that a mailman could take to deliver the mail. Maybe he has to hop a fence one way, but it takes a shorter period of time. Maybe one route has a great view, but it takes a little bit longer. Like all VPNs, Perfect Privacy uses a variety of Internet protocols in order to make itself as fast and secure as possible. Let’s take a closer look.
OpenVPN
Whenever I hear that a VPN uses OpenVPN for its software, I breathe a sigh of relief. That’s because OpenVPN is the most secure VPN software, known for its ability to bypass firewalls. It’s crowd-sourced by the community and is being adjusted constantly in order to avoid tampering by surveillance agencies. In other words, OpenVPN is definitely a great foundation for Perfect Privacy to start on!
SSH2 Tunnel
A Secure Shell creates both the tunnel and the encryption that will allow users to transfer information. While the SSH doesn’t encrypt the data itself, it creates the tunnel through which the data will pass. SSH2 is a more secure version of the original SSH, so it’s certainly up to industry standards.
Squid Proxies
Don’t ask me why they’re called Squid proxies, but Squid proxies speed up web servers by caching or storing, repeated requests, plus web, DNS, and other network lookups. In a nutshell, Squid proxies help reduce the bandwidth you’re using, improving your network’s speed.
SOCK25 Proxies
SOCKET25 stands for Sockets version 25. It’s what will give you a new IP address as you connect to the VPN and what takes your data from one location to another. Keep in mind that SOCK25 doesn’t actually encrypt the data, only the access to the server. So, while it’s a fast protocol, it’s not the most secure— that’s why Perfect Privacy uses additional encryption.
PPTP
Point-to-Point Tunneling Protocol creates the tunnel used to encapsulate the data packet. Again, it’s not the most secure method available, but that’s why secondary protocols are used.
Testing Perfect Privacy
Now it’s time for my favorite part— actually testing the Perfect Privacy VPN for speed and security.
Speed Test
The first thing I test is speed, specifically download speed, upload speed, and latency. I test all my VPNs on two computers— a Macbook Air and a Windows Vivobook from my apartment in Brooklyn on an Optimum network. Let’s see how Perfect Privacy performed.
Download Speed Tests
Usually, we don’t have such a stark difference between the Mac and the Windows computer, but Perfect Privacy is another story. While it only had a download difference of about 26% on my Mac, the difference was closer to 59% on my Windows computer. Not so great.
| Mac | |
|---|---|
| Without VPN | 7.18 mbps |
| With VPN | 9.07 mbps |
| Windows | |
|---|---|
| Without VPN | 70.13 mbps |
| With VPN | 28.85 mbps |
Upload Speed Tests
Although it looks like the upload speed was better on the Mac again, if you look at it in terms of the percentage difference between the speed with and without the VPN, Perfect Privacy actually performed better on my Windows computer, with a difference of around 25% compared to 51% on the Mac.
| Mac | |
|---|---|
| Without VPN | 4.26 mbps |
| With VPN | 2.08 mbps |
| Windows | |
|---|---|
| Without VPN | 42.03 mbps |
| With VPN | 31.56 mbps |
Ping Speed Tests
The last measurement I’ll take is ping, or latency measured in milliseconds. On the Mac, Perfect Privacy actually decreased my latency by about 18%, which is great. Unfortunately, the Windows’ latency was increased by a whopping 161%, which is a huge difference. Overall, Perfect Privacy performed better speed-wise on my Mac than on my Windows computer.
| Mac | |
|---|---|
| Without VPN | 40 ms |
| With VPN | 33 ms |
| Windows | |
|---|---|
| Without VPN | 13 ms |
| With VPN | 34 ms |
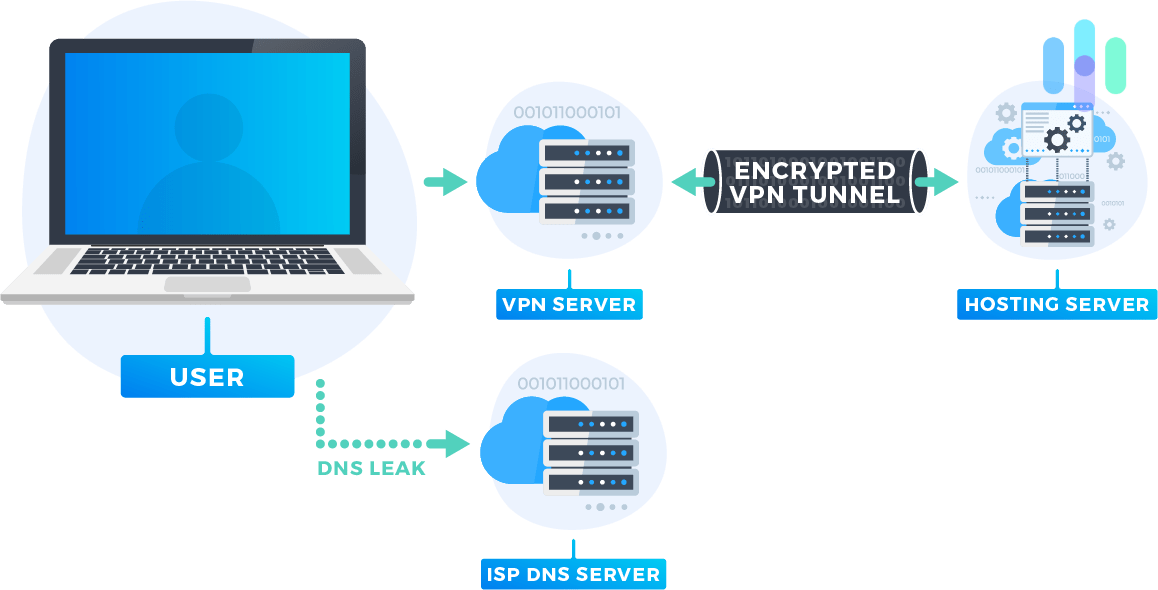
DNS Leak Test
A DNS, which stands for domain name server, is what you type in to get to a website, like Security.org, for example. Really, the DNS stands for an IP address that actually tells your computer where to go. If you’re using a VPN, you want to make sure that your DNS’s are kept within the encrypted tunnel. Perfect Privacy passed the test with no DNS leaks!
WebRTC Leak Test
The last thing I test for is WebRTC leaks. WebRTC allows users to communicate directly with each other without having to go through an intermediate server. It allows for faster speeds when livestreaming, sharing files, or video chatting. However, it does require that the users know each others’ private IP addresses, so it’s important to keep this information on the D.L. Again, Perfect Privacy had no WebRTC leaks so I’m pretty satisfied!
Perfect Privacy Subscriptions
Perfect Privacy offers unlimited server switches, simultaneous connections, and devices per subscription, which is pretty generous. Let’s talk more about your options.
Subscription Options
| Term | One Month | One Year | Two Years |
|---|---|---|---|
| Monthly Price | $12.99 | $9.99 | $9.85 |
| Total Price | $12.99 | $119.99 | $214.95 |
As you can see, the longer the term length, the lower your monthly price will be. Keep in mind that the monthly prices are in Euros, so I would do a quick conversion before you make any decisions.
Looking at the numbers, I can see that Perfect Privacy is a bit more expensive than its competitors, so much that they address it on their website. While most VPNs start at only a few USD a month, Perfect Privacy’s subscriptions start at about $10, over three times the cost of their competitors. They blame their upper-level pricing on a few features of Perfect Privacy— their Internet Protocols, unlimited connections per member, support for many operating systems, lack of limitations on bandwidth, etc. We’ll talk more about Perfect Privacy’s value when we compare it to one of its competitors below.
Manual Configurations
Perfect Privacy works on Windows, Linux, Mac, and Androids.
Supported Browsers
You can use a Perfect Privacy VPN on all browsers. That’s easy enough!
Customer Support with Perfect Privacy
Great customer support is always important, but it’s particularly important when it comes to technology. There are few things more frustrating than failing to communicate with a computer and not being able to figure out why— it sort of feels like trying to speak with someone you are in love with and whose language you don’t speak. That’s why having a robust customer support system is essential for a VPN company. Let’s see how Perfect Privacy’s customer support works, and how effective it actually is in helping customers.
Features
You can contact customer support through email or an online contact form. There’s also a section of FAQ’s on the website.
Although I’m disappointed there’s no phone or live-chat support, I will say that my email was answered in a prompt and thorough manner.
| Type of customer support | Available with Perfect Privacy? |
|---|---|
| Phone support | No |
| Live-chat support | No |
| Email support | Yes |
| Online contact form | Yes |
| FAQs | Yes |
| Manuals | Yes |
| Forum | Yes |
Customer Support Ratings
Finding customer reviews of Perfect Privacy was difficult. Being Switzerland-based, they’re not on the Better Business Bureau, nor is the VPN sold on Amazon. I guess I’ll just have to go off my personal experience!
The OpenVPN Connect App
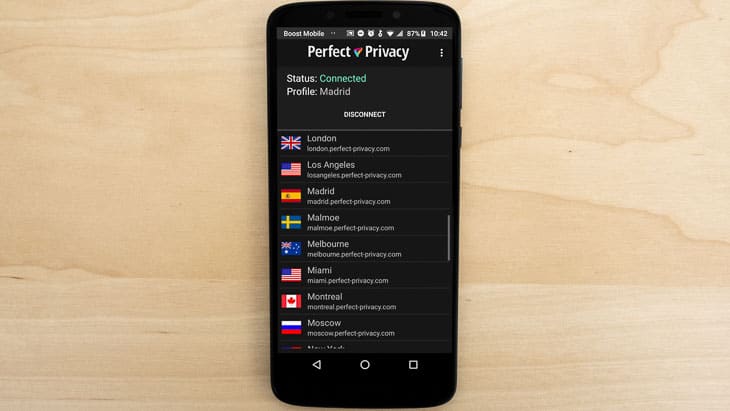
You’ll use the OpenVPN Connect app to connect to Perfect Privacy on your iPhone or Android. The app has good ratings from both sets of users, with a 3.9 from the Apple store and a 4.3 from the Google Play store.
“Essential app. This allows me to keep my phone connected to my home VPN with the minimum of fuss and maximum flexibility,”
wrote an Android user in a five-star review.
Perfect Privacy vs. NordVPN
NordVPN vs. Perfect Privacy Features
| Feature | NordVPN | Perfect Privacy |
|---|---|---|
| Log Data | No | No |
| Kill Switch | Yes | Yes |
| Split Tunneling | No | Yes |
| Netflix | Yes | No |
| Torrenting | Yes | Yes* |
| IP Addresses | Anonymous, shared with other NordVPN users but can pay for dedicated IP address | Anonymous; OpenVPN & IPSec will sometimes use the same IP address on reconnection |
*Not on servers in U.S. or France
I’m comparing Perfect Privacy to NordVPN, a company based in Panama. Like Perfect Privacy, NordVPN does not keep track of user data like the time or duration or any session, IP addresses or servers used, websites visited or files downloaded. NordVPN is a much bigger company than Perfect Privacy, with 5,246 servers in 62 countries; Perfect Privacy has about a tenth of the number of servers in half the countries. Both have kill switches, but Perfect Privacy offers something that NordVPN doesn’t— split tunneling. If you’re looking to access public and private networks simultaneously, Perfect Privacy is the VPN for you. Neither company is headquartered in a country that’s part of any international surveillance alliances, so they’ll never be forced to hand over users’ data. And if you’re a Windows user, I would choose NordVPN over Perfect Privacy for sure. The lower pricing doesn’t hurt, either!
Our Perfect Privacy Research and Data
The following is the data and research conducted for this review by our industry-experts. Learn More.
Encryption
| In Transit | Yes |
|---|---|
| At rest? | Yes |
| All network communications and capabilities? | Yes |
Security Updates
| Automatic, regular software/ firmware updates? | Yes |
|---|---|
| Product available to use during updates? | No |
Passwords
| Mandatory password? | Yes |
|---|---|
| Two-Factor authentication? | No |
| Multi-Factor authentication? | No |
Vulnerability Management
| Point of contact for reporting vulnerabilities? | admin@perfect-privacy.com |
|---|---|
| Bug bounty program? | No |
Privacy Policy
| Link | https://www.perfect-privacy.com/en/privacy-policy |
|---|---|
| Specific to device? | No |
| Readable? | Yes |
| What data they log | Login credentials, expiration date of account, email address, customer service communications, website analytics |
| What data they don’t log | Payment information, user traffic, IP addresses, access times or duration, bandwidth caused by individual users |
| Can you delete your data? | Yes; it is deleted automatically 60 days after you close your account |
| Third-party sharing policies | Yes, for payment processing |
Surveillance
| Log camera device/ app footage | n/a |
|---|---|
| Log microphone device/ app | n/a |
| Location tracking device/ app | No |
Parental Controls
| Are there parental controls? | Yes |
|---|
Company History
| Any security breaches/ surveillance issues in past? | No |
|---|---|
| Did they do anything to fix it? | n/a |
Additional Security Features
| Anything like privacy shutters, privacy zones, etc.? | n/a |
|---|
Recap of Perfect Privacy
Overall, I would recommend Perfect Privacy as your VPN choice. It worked well on my Mac and Windows computers with no data leaks whatsoever, and the company is sound as a whole.
You should use Perfect Privacy if you’d like…
- No data retention laws: Being based in Switzerland, a country known for staying out of international politics, has its perks.
- No data logging: Perfect Privacy is particularly passionate about not logging consumer data.
- Multi-hop: Your data will travel through multiple servers where it will be encrypted multiple times.
- Kill-switch: If Perfect Privacy fails, all of your web browsers will immediately shut down.
- Fast speed on Mac: Perfect Privacy performed particularly well on my Macbook Air.
But here are some possible reasons to steer clear:
- So-so performance on Windows: While Perfect Privacy didn’t perform badly on the Windows computer, it was no match to the Mac.
- Not the cheapest option: Perfect Privacy’s extra security features make it more expensive than other VPNs.
That’s it from me! Let me know if you have any questions, and thanks for reading.
FAQs
We’ve taken on some of your most burning questions about Perfect Privacy. You’ll find all the answers below.
-
Is Perfect Privacy safe?
Perfect Privacy is absolutely safe. It is headquartered in Switzerland, outside the Five Eyes, Nine Eyes, and 14 Eyes surveillance groups. That means the company can’t be forced to turn over records to any government agency. In addition, Perfect Privacy only logs billing information, including usernames, passwords, and email addresses. It never logs sensitive information like IP addresses, timestamps, or browsing activity.
-
Does Perfect Privacy have a free version?
Perfect Privacy does not have a free version. It does, however, have a money-back cancellation policy, though, if you cancel within the first seven days. That gives you a small window in which to check out the service.
-
What does Perfect Privacy cost?
Perfect Privacy costs $13 if you’re paying for a one-month subscription. You’ll save money with a one-year subscription, which runs $10 a month. A two-year subscription will save you even more, priced at $9 a month.
-
Can I access Netflix with Perfect Privacy?
You can’t count on accessing Netflix with Perfect Privacy. Netflix has blocked many of the company’s servers. Some may work, but many may not. In fact, you may have trouble accessing most streaming services with Perfect Privacy. The company bills itself as focused on privacy and isn’t shy about saying it isn’t as concerned with streaming.