So what if someone has your email address, right? You might display it proudly on your social media profile or give it out to friends and family who want to use your Netflix login. It’s not like a hacker can do anything with an email.
But you might be surprised at how much damage someone can do with just your email address. It’s not just something you get Black Friday deals sent to — it’s a gateway to other personally identifiable information like your name, address, and financial accounts. We’re going to show you how hackers get your email and what they can do with it. Don’t worry, we’ll also tell you how to protect yourself so you’re one step ahead. Let’s begin!
>> Learn: How to Stop Spam Emails
What Can Bad Actors Do With Your Email Address?
Think about how many accounts are tied to your email address. Do you use it for banking, shopping, social media, or security tools like password managers? If the answer is yes to any of these, then it’s the key to your digital life. If a hacker can get into your inbox, then they can:
- Reset passwords: Scammers won’t hesitate to click the “forgot password” link and lock you out of your account. They’ll change it to something you can’t access and make it challenging for you to reclaim your accounts.
- Bypass multi-factor authorization (MFA): If your email address is part of your MFA setup, scammers can intercept verification codes to hack accounts.
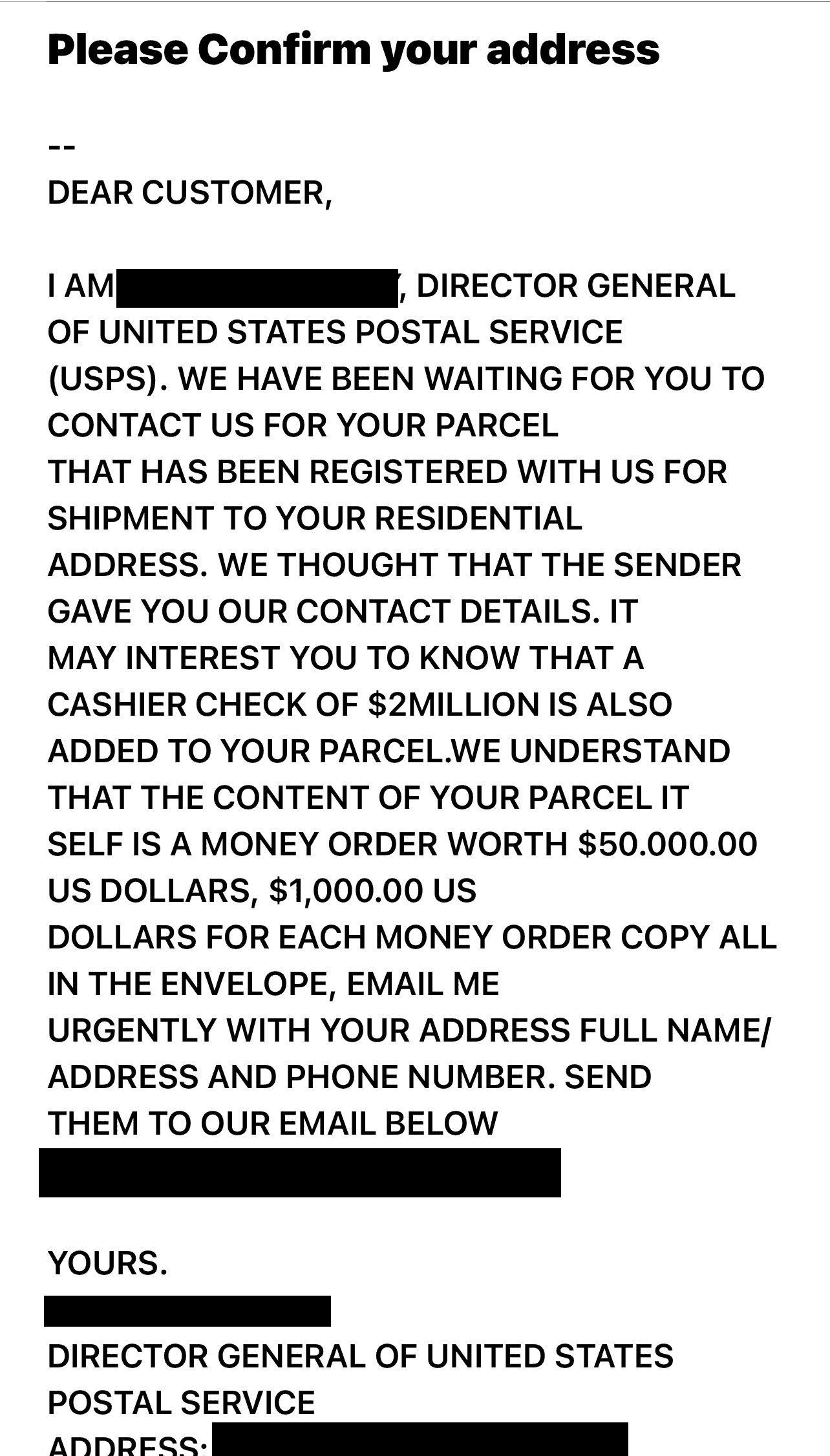
- Impersonate you: In some cases, scammers will use your email address to contact friends and family members. They’ll pose as you to send money for a fake emergency.
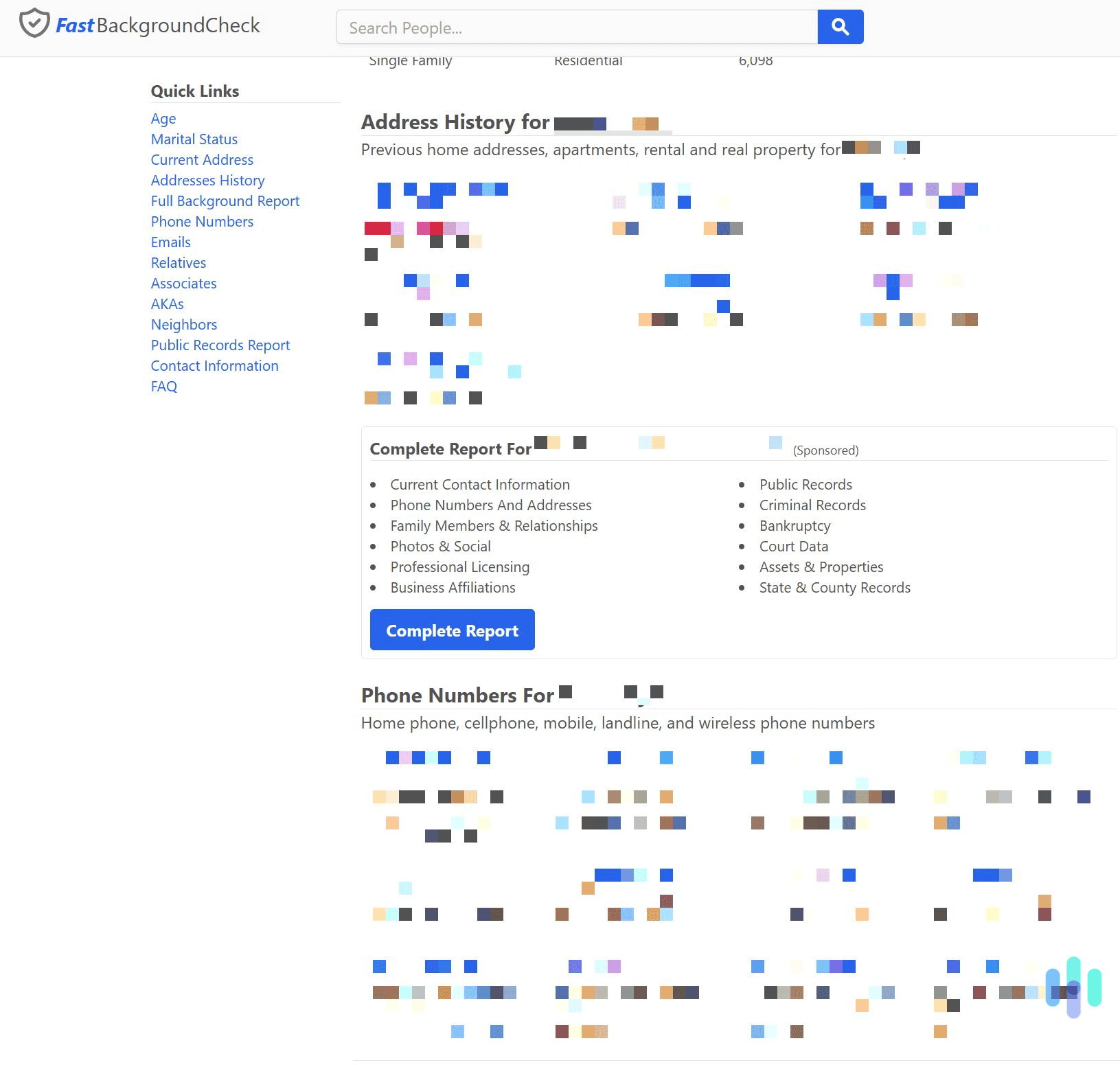
- Uncover other personal data: If your bills and receipts go to your inbox, scammers can piece together your address and spending habits.
Even if they don’t access your mailbox, scammers can target you with phishing attacks or try to steal your identity. The more information they have on you, the easier it is for them to succeed.
>> Check Out: Recognizing Phishing Attempts
From there, things can get more serious. One example is financial fraud, which ranges from scamming friends or family members using your email address to opening short-term, high-interest loans in your name.
Incogni’s data removal service deletes your personal information from databases sold by data brokers for everyone to see, reducing your risk of spam, hacking, and stalking.

Criminals can also use your email address to steal your identity. They look for anything tied to your email address, like your full name, location, and any login credentials exposed in data breaches. Once hackers have these details, they can build a profile and try to access all your accounts, or even create new ones that damage your credit.
FYI: Hackers can use your email to take over financial, shopping, and social media accounts. According to our research, over two-thirds of people use the same passwords across multiple accounts. If you’re one of them and have two-factor authentication set up, hackers can log into your inbox, access verification codes, and lock you out.
How People Can Get Your Email
The first thing we recommend doing is checking what information you display on your social media. If it’s a public profile, hackers may already have your email address. Some of the other ways they can get it include:
- Email harvesters: Scammers use bots to find personal details on every public website online. These bots target the @ symbol in their searches, as it’s an indicator for email addresses.
- Data breaches: If your username is your email address, it may become available if the account you use it for is ever leaked or stolen.
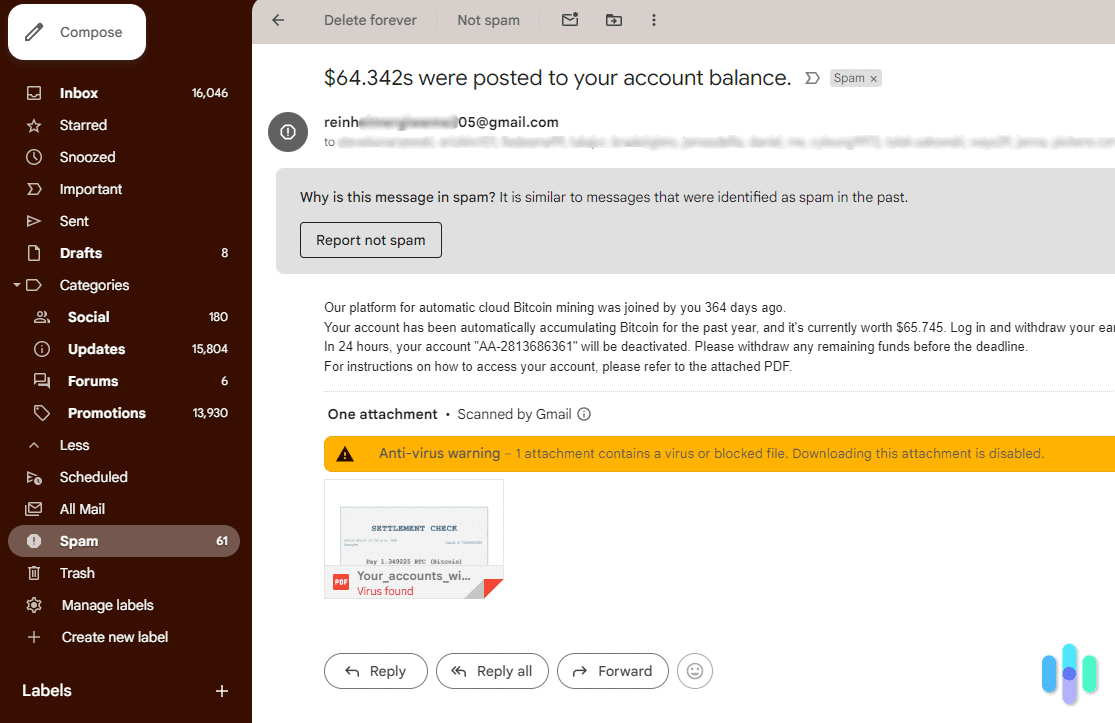
- Phishing scams: Fake emails and text messages have malicious links that capture your data, including email addresses.
- Marketing lists: Data brokers sell your digital information to the highest bidder. This is why we recommend using data removal services to protect your email address.
- Dark web: If any of your data is sold or stolen, it can end up on the dark web for criminals to purchase.
- Fake forms: The internet is home to fake web pages asking for your email address to subscribe to a newsletter or access a discount.
Signs That Someone is Misusing Your Email
You might not realize that someone is using your email address immediately, but there are a few signs to look out for. Hackers don’t always take over your account, so it’s important to watch for unusual login attempts or friends mentioning suspicious messages you didn’t send. Here are some other signs to keep an eye out for.
| Sign of Misuse | What it Could Mean | What You Should Do |
|---|---|---|
| You can’t access your account | Someone may have reset your password and taken control of your account. | Use account recovery options or contact support to regain access. |
| Unusual login attempts | Someone is trying to access your account from a new device or location. | Change your password and activate two-factor authentication. |
| Random password reset emails | Hackers are testing access to your account. | Don’t click any links. Go directly to the website and change your password. |
| Someone tells you they got a weird email from you | Your email address may be compromised. | Run antivirus software and change your password. Let your contacts know you’ve been hacked. |
| Unexpected two-factor authorization messages | Someone is using your login. | Change your password and review any other logins on your account. |
| Your spam email is higher than usual | Your email address has been leaked or added to spam lists. | Create a separate email address for sensitive accounts. |
| New accounts or charges in your name | Your email is being used for identity theft or unauthorized purchases. | Review credit reports and freeze your credit. Report any suspicious transactions. |
FYI: Freezing your credit normally requires a call to one of the three major credit bureaus, but some of the best identity theft protection services let you freeze it with just one click. You can even unfreeze it just as quickly when you need to apply for new credit.
Why Linking Your Email to Personal Information is Risky
Using one email address for everything might be convenient, but the more valuable it becomes, the more of a target it is for hackers. If they get access to your inbox, they can gather bank statements, tax forms, social media accounts, online shopping purchases, and more. All of this personal data can be used to steal your identity.
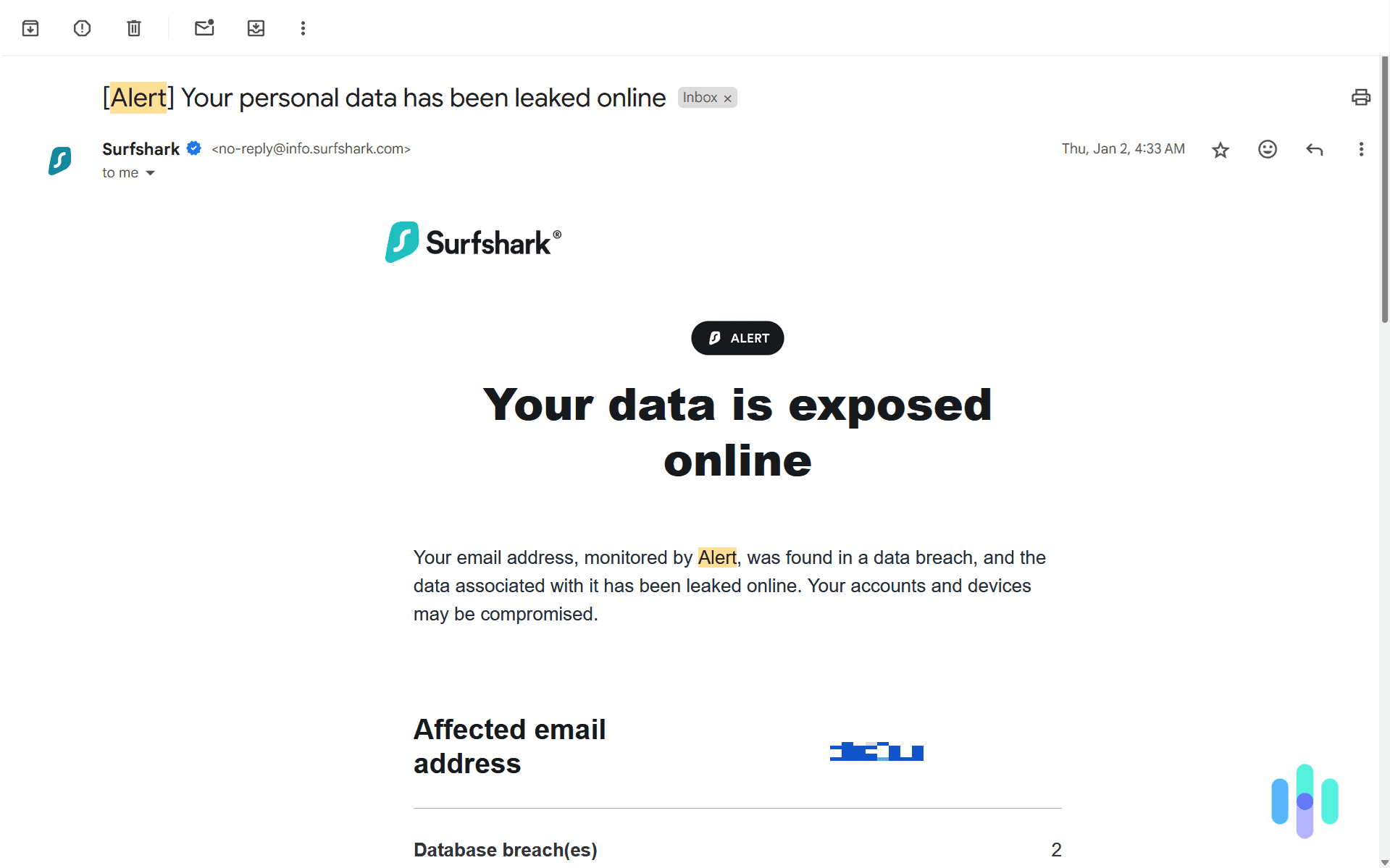
But even knowing what your email address is linked to puts you at risk. Hackers may use that information to craft personalized phishing attacks — for example, sending fake Amazon emails if they know you’re a regular shopper. If they find Best Buy receipts, they might try to trick you into thinking your device is infected.
>> Keep Reading: Everything You Need to Know About the Geek Squad Scam
We recommend using separate emails for different purposes — one for your finances and another for online shopping. Another option is to use an email masking tool. One of our favorite VPNs, Surfshark, has a tool that generates fake email addresses for online accounts. It helps block phishing attacks and keeps your identity anonymous if it’s ever leaked in a data breach.
How to Protect Your Email Address
You can’t control every data breach or phishing scam, but there are some simple habits that can keep your inbox and identity secure. Here are our recommendations:
- Enable two-factor authentication: This feature adds an extra layer of protection to your accounts and alerts you to any unauthorized attempts.
- Avoid sharing your email online: Don’t post your email address on social media accounts or public forums. If you must, use a disposable or masked email instead.
- Never click suspicious links: If you get a strange email or text message, don’t click on anything. Go directly to the website instead. Real companies never use these methods to ask for your sensitive details.
- Review account activity regularly: Some platforms let you review recent login activity. Make a habit of checking monthly for unknown devices and locations.
- Keep devices updated: Hackers love exploiting old software, so make sure to regularly update your devices and apps to patch known security vulnerabilities.
- Close unused accounts: If you’re no longer using a service or platform, delete the account so your email isn’t linked to it.
- Don’t reuse passwords: Avoid using the same passwords for all your accounts. If one account is breached, the rest stay protected. Check out our guide on the best password managers that can help you keep track of all your credentials.
Pro Tip: Another interesting fact our research revealed is that 45% of Americans use passwords with fewer than eight characters. We recommend a password with a minimum of 12 characters, but 16 is even better. Can’t think of anything that long? Use our password generator to create one.
Tools That Can Help Protect Your Email
Good habits go a long way, but we also recommend using digital security tools for full coverage. These services specialize in monitoring your data and protecting your email address from threats like phishing, identity theft, and data breaches.
- Password managers: Apps like NordPass and RoboForm store your login credentials in a secure, encrypted vault. They flag weak, compromised, and reused passwords. These tools will even prefill fields so you can log in with one click.
- VPNs: A virtual private network encrypts your IP address and internet traffic. If you want to check your email on public Wi-Fi or shared networks, we recommend turning on your VPN first.
- Antivirus software: Tools like Norton and Bitdefender scan and block malicious files, links, and attachments sent to your inbox before they reach you.
- Identity theft protection services: These tools monitor your financial accounts and personal data for suspicious activity. They even include funds to help you recover your identity if it’s ever stolen.
- Data removal services: Platforms like Incogni scan data broker databases and people search sites for your information and request their removal. They keep you informed about all the requests they’ve sent and continue monitoring in case you’re ever re-added.
>> Compare: The Best Data Removal Services of 2026
Final Thoughts
Now you have a clearer understanding of how important your email address is and the risks when it falls into the wrong hands. However, you also have some simple tips to protect both your inbox and your identity.
While steps like using strong, unique passwords and enabling two-factor authentication are a great start, digital security tools offer additional protection. Password managers secure your logins, VPNs encrypt your connection, and antivirus software blocks malware. We also recommend using data removal apps to delete your information from broker websites, and identity theft protection services to monitor your financial and personal details. With good habits and great tools, you’re more likely to stay ahead of hackers.
FAQs
-
Can someone hack a bank account with just your email address?
Hackers can’t directly access your financial accounts with just an email address. However, if your email address is your username, it is vulnerable. Hackers may try to gain access to your inbox and reset banking passwords.
-
How do you know if your email has been compromised?
If you notice password reset emails you didn’t request, login alerts from unusual locations, or messages in your Sent folder you didn’t send, then your account might be compromised. Another red flag is people mentioning they’ve received strange emails from you.
-
What should you do if you think your email is hacked?
We recommend logging in and changing your password immediately. If you’re locked out, try following the account recovery process or contacting the support team. After regaining access, enable two-factor authentication, scan your devices for malware, and review any linked accounts for unusual activity.
-
How do you find out your email is on the dark web?
Free online tools like Have I Been Pwned can check if your email is on the dark web, but we recommend using identity theft protection services with dark web monitoring. These services will send alerts if your details are found.
-
What’s the best way to secure your email account?
We recommend using a strong, unique password for your email account. You should never reuse it for other services. Make sure to turn on two-factor authentication for added security, and regularly check your login activity for suspicious access.