What’s the harm in handing out your phone number? Maybe you’ve used it to secure discounts or enter a giveaway. Some social media accounts and apps ask for your phone number to verify you’re a real person. It’s not like you’re handing over your credit card number, so what’s the big deal?
You might be surprised to learn that phone numbers are personally identifiable information. Your phone number is linked to your bank accounts, social media profiles, email, and more. Scammers know this and use it to launch phishing attacks, take out loans, and steal your identity. Let’s go through how valuable your phone number is, what a hacker can do with it, and what you can do to keep it secure.
Why Your Phone Number is Valuable to Hackers
In the past, the worst thing someone could do with your phone number was prank call you and ask if your refrigerator is running. But in today’s digital age, your phone number is tied to your online identity. Services like banking apps and social media accounts use your number for authentication. If someone gets access to your number, they can reset passwords, unlock account recovery options, and intercept multi-factor authentication codes.
>> Read More: Account Takeover Fraud: What You Need to Know
Phone numbers are also unique identifiers — they’re tied to loyalty programs, ride-sharing services, and delivery apps. When combined with public records, they allow scammers to build a complete profile. Scammers can use your number to steal your identity, take out loans, and trick family and friends into sending them money.
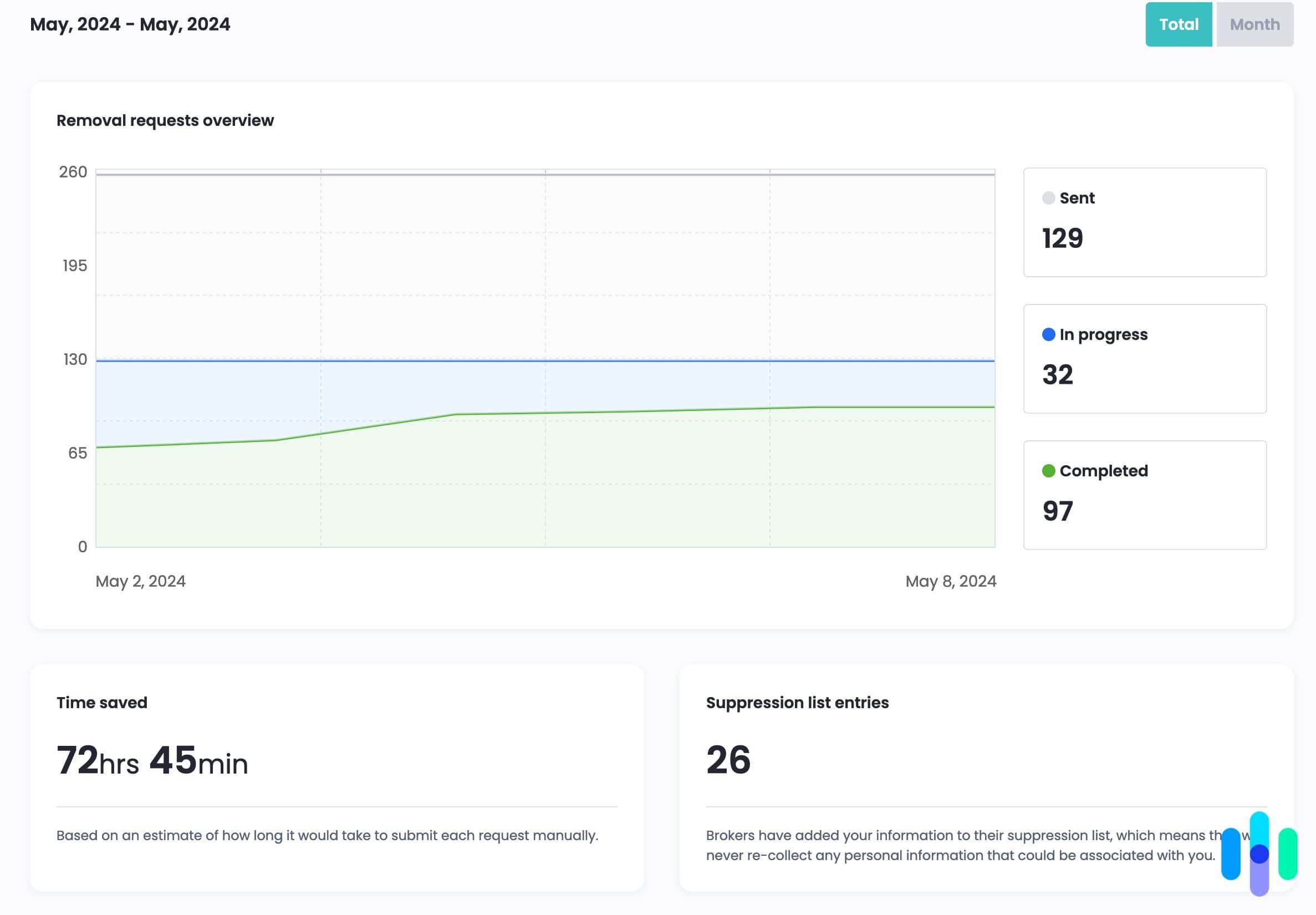
Incogni’s automated data removal service scans the internet to find your name, address, and other personal information and requests their removal so you’re not vulnerable to scams and identity theft.

How Can Someone Get Your Phone Number?
Even if you’ve removed your phone number from the Whitepages, it’s not as private as you might think. Here are some of the most common ways someone can get their hands on it.
- Social media: Some people list their phone number on Facebook and LinkedIn without realizing it’s publicly visible. We recommend logging out of your account and viewing your profile as a public user to see what information is on display.
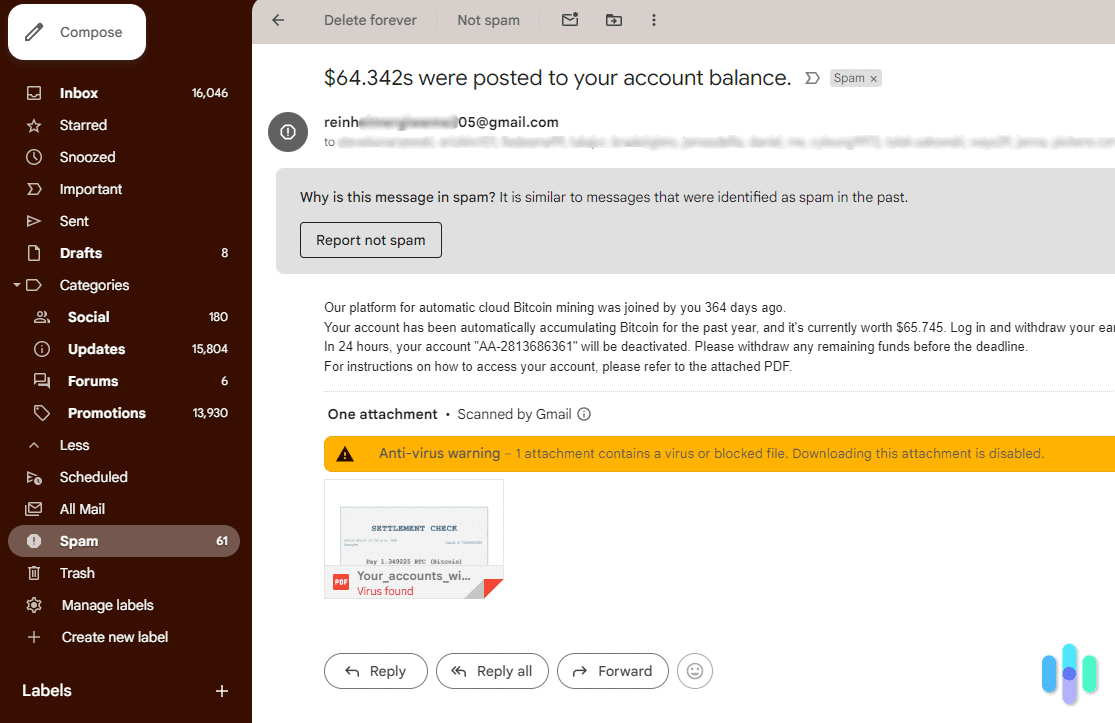
- Data breaches: Hackers often get phone numbers in the data they steal from companies. Then they end up sold or shared on the dark web. Thankfully, some identity theft protection services monitor the dark web and alert you if your details appear.
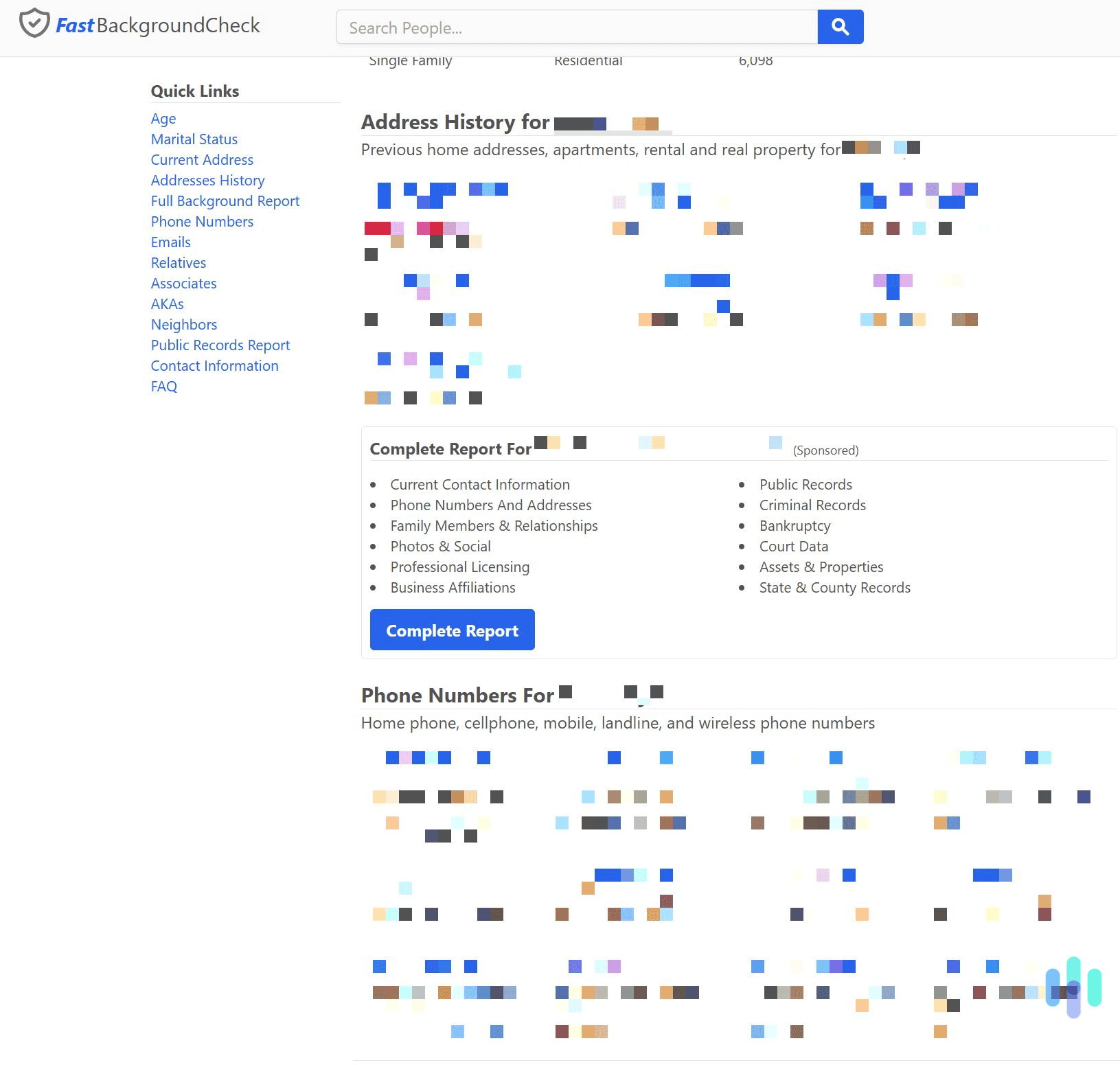
- Public records: Everything from court filings to voter registrations and property records includes your phone number. The information is available from a basic search and is difficult to have removed.
- People search sites: Websites like Whitepages and BeenVerified gather your details, like phone numbers, from multiple services. Fortunately, there are opt-out steps you can take.
- Data brokers: Your phone number might be bundled in a consumer profile without your knowledge. Data brokers scrape information from a wide range of sources, including surveys and online purchases. We suggest using a data removal service to delete your details from their databases.
- Online forms: If you need to contact a company, they often request your phone number. However, some organizations sell or share the data with advertisers or third-party analytics firms. Check the privacy policy to see what they do with your data before you hit the submit button.
- Contests and giveaways: You may need to include your phone number to enter sweepstakes or giveaways. Most of the time it’s for marketing purposes. Other times it’s a scam to collect contact information.
- Mobile app permissions: Many apps ask for access to your contacts and call logs with little information as to why. If you agree, the data may be used for marketing or sold to data brokers.
- SIM swapping: With enough basic information, scammers can call your phone carrier and convince them to switch your number to a new SIM card. This gives them control over your calls and texts.
>> Find Out: Can an iPhone Be Hacked?
What Can Hackers Do With Your Phone Number?
Once someone has your phone number, they can be far more annoying than just sending spam texts or making robocalls. It can be a starting point for phishing attacks or access to sensitive accounts. Here are some examples of what cybercriminals can do and the damage they can cause.
| What Hackers Can Do | How It Works | Impacts |
|---|---|---|
| SIM swapping | Hackers convince your carrier to transfer your phone number to their SIM card | Account hijacking, loss of access to your phone, financial theft |
| Phishing and smishing | Fake texts and emails are sent using your phone number or directed at it | Stolen login credentials, malware, financial fraud |
| Bypassing two-factor authentication | Scammers intercept SMS-based 2FA codes linked to your phone number | Unauthorized logins |
| Exploiting account recovery | Hackers use your number to reset passwords and access recovery links | Account takeovers |
| Identity theft | Your phone number, along with other data, is used to steal your identity | Fraudulent loan applications, credit damage, legal issues, financial loss |
| Impersonation | Your number is used to make scam calls look legitimate to your contacts | Reputational damage |
| Targeted scams | Scammers use any data linked to your account to make personalized attacks | Fraud, manipulation, or blackmail attempts |
| Tracking | Monitoring your location or activity using apps or services tied to your phone number | Privacy invasion, stalking, data harvesting. |
How to Keep Your Phone Number Private
Once your phone number is out in the open, it’s hard to hide it. We recommend limiting where you share this information. For example, avoid including your phone number on online profiles like social media, job boards, and personal websites — even if there is an option to set the profile to private.
Pro Tip: If a website won’t let you create an account without a phone number, consider using Surfshark’s Alternative Number. It’s available as an add-on for any Surfshark VPN plan. You can avoid submitting your real phone number, reducing exposure to spam, robocalls, and data breaches.
People-search sites are another source of exposure. These websites scrape public records, social media, and marketing databases to compile personal profiles. Thankfully, many offer opt-out procedures, but the process is time-consuming. That’s why we rely on data removal services like Incogni and DeleteMe to handle this chore for us. Removing our data from these websites reduces the risk of scams and identity theft.
How to Secure Your Device
In addition to keeping your phone number private, we recommend securing your mobile. Here are some simple steps you can take:
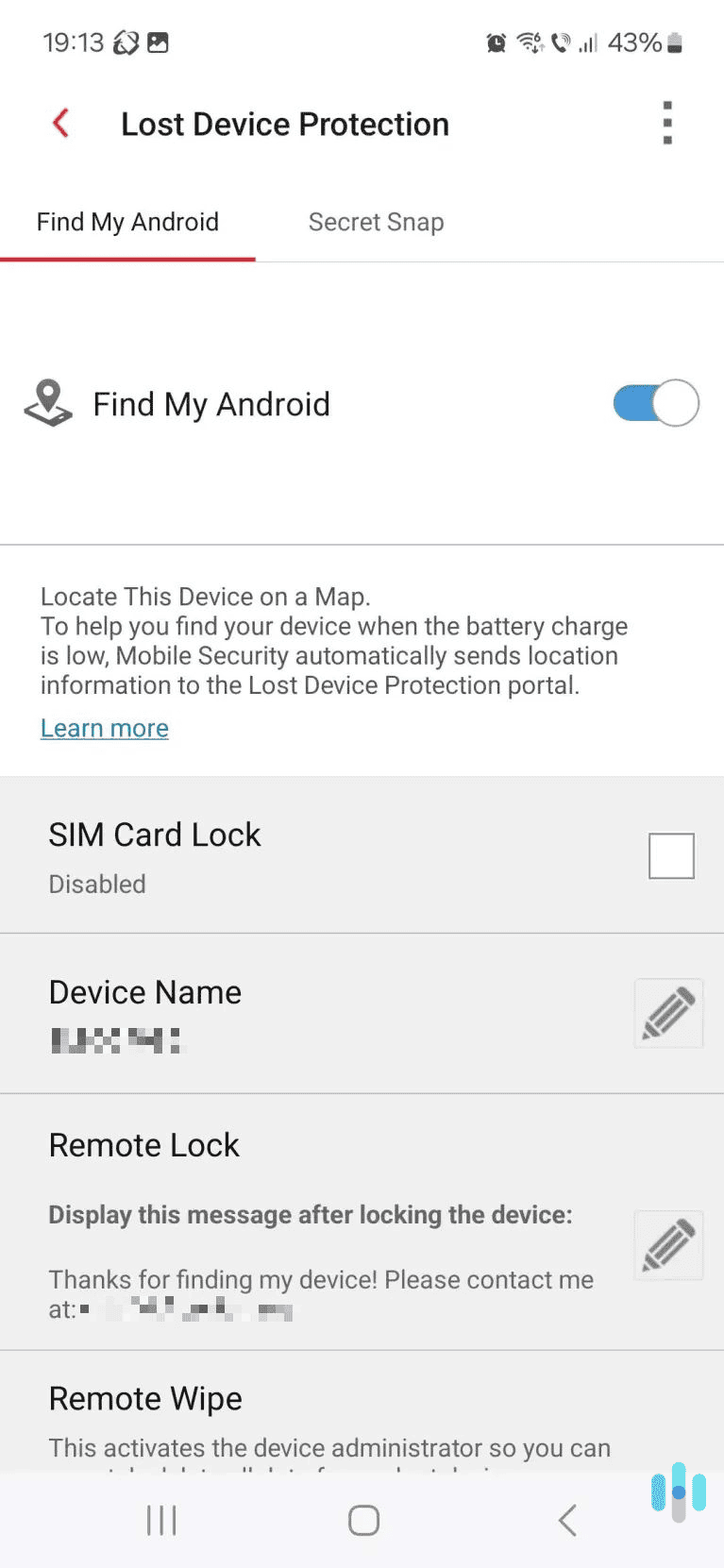
- Add a PIN or password to your SIM: While you might lock your phone, you also need to lock down your SIM. Adding a PIN prevents someone else transferring your SIM to another device.
- Use biometric phone locks: We recommend using fingerprint or facial recognition to prevent unauthorized access.
- Install an authenticator app: Use Google Authenticator or Microsoft Authenticator instead of SMS for multi-factor codes
- Limit app permissions: Review what your apps have access to and revoke unnecessary access
- Keep your device updated: Immediately install the latest software updates and security patches to reduce vulnerabilities to malware and exploits.
- Install an antivirus app: If you check your email on your mobile or click on SMS links, use an antivirus app to check they’re safe.
How to Tell if Your Number is Compromised
It might not be obvious that your phone has been exposed or hijacked, but there are a few warning signs to watch for. For example, if you stop receiving texts or calls, immediately check if you still have cell service; this might indicate SIM swapping. You might also notice an increase in 2FA codes that you didn’t request.
Other signs are more subtle. Don’t ignore friends or family who say they’ve received strange messages from your number. Review your account recovery emails, too — someone could be using your number to trigger password resets. If you notice these signs, check your bank transactions and account activity for anything unusual. Catching it early can stop an attack before it causes serious damage.
>> Read More: What to Do if Your Phone Has Been Hacked
What to Do If Your Number is Exposed
If you notice any of the signs we mentioned earlier or suspect your phone number is being misused, we recommend taking these steps:
- Contact your mobile carrier: Speak to your provider about the issue and ask them to check for SIM swap attempts or unauthorized changes. If you don’t have a PIN or passphrase, request one for extra security.
- Change your passwords: Update the passwords on key accounts, including banking, email, and social media. If you can’t think of a new password, use our password generator to create one.
- Scan your device for viruses: Use an antivirus app to find and remove malware or suspicious files on your device.
- Warn your contacts: Send a secure message to your contact list so they know your number is exposed and to ignore any impersonation scams.
- File a report: Report any fraud or account takeovers to the FTC at identitytheft.gov, as well as to your local authorities.
- Freeze your credit: If you’re concerned about your finances, consider placing a freeze with all three major credit bureaus to block anyone trying to open new accounts.
Pro Tip: Use an identity theft protection service like LifeLock to freeze all three credit bureaus with one click. No need to call each one separately, and you can unfreeze just as easily when you need to apply for a loan.
Tools To Keep You Safe
Changing your habits can make a big difference. But for an added layer of security, we recommend investing in a few key tools — each one plays an important role in protecting your phone number.
Antivirus Software
You might be asking yourself if you still need antivirus protection in 2026. But we use an antivirus app to protect our device from malicious downloads, phishing links, and spyware.
Identity Theft Protection
These services monitor your phone number, Social Security number, financial accounts, and more. If your details are stolen, these services offer recovery assistance and insurance to help you get back on your feet.
>> Compare: The Best Identity Theft Protection Services of 2026
Password Managers
Our recent report on password managers revealed over half of adults use unsecured methods like browser storage and written records to manage their passwords. We recommend using a password manager to store credentials in military-grade encrypted vaults and securely log you into accounts.
Did You Know: We asked Americans about their password habits and learned 57% use slightly modified old passwords. We recommend using a combination of 12 to 16 random characters and storing them in a password manager so you don’t forget them. Use our password strength checker to see how secure they are.
Data Removal Services
If you find your phone number online, use data removal services to delete it. They can act on your behalf to take down information from data brokers and people-search sites. This reduces the chance of your phone number receiving malicious texts and robocalls.
>> Find Out: How to Remove Your Information From the Internet
Final Thoughts
Your phone number can be used to gain access to more of your personal data. If you don’t take the necessary steps to secure it, hackers can take over your accounts, launch phishing scams, and steal your identity.
Limiting app permissions, adding a PIN to your SIM, and using biometrics are great first steps. But we recommend using digital security tools like password managers, antivirus apps, and identity theft protection services to safeguard your data and identity. If you see an increase in spam messages and robocalls, use data removal services to delete your information from the internet.
FAQs
-
Can someone hack your phone with just your number?
A hacker can’t take over a phone with just your number. However, they can use it to start phishing attacks, impersonate you, or intercept two-factor authentication codes. This can lead to account takeovers and stolen identities.
-
What should you do if you get a suspicious call or text?
We recommend ignoring the call and deleting the text. Block the number, then report it to your carrier and the authorities. If the message looks like it has come from a legitimate company, contact them directly.
-
Should you get a new phone number if it’s compromised?
Getting a new phone number should be a last resort. Our recommendation is to explore this option if you have experienced repeated account takeovers, frequent SIM swapping attempts, or have had your identity stolen. However, there are other steps you can take before changing your number, like adding a PIN to your SIM, using authenticator apps for 2FA codes, and deleting your information from the internet.
-
How often should you check if your number is on data broker sites?
You should review people-search and data broker sites every few months. However, data removal services can monitor your information for you and request deletion so you don’t need to do it manually.
-
How do you report phone number-related scams?
The best place to start is the Federal Trade Commission website reportfraud.ftc.gov. You can also forward spam texts to 7726, which allows carriers to investigate and block malicious senders.