- An iPhone can be hacked. iPhones are less vulnerable than Android, but there are ways around Apple’s security to make hacking possible.
- Good digital hygiene, which includes using strong passwords and updating your iOS software, can help prevent hacking.
- Having antivirus software helps a lot, too! Explore TotalAV in our TotalAV review and see how it’s so much more than just an antivirus software.
While iOS security gets a lot of well-deserved praise, the Apple marketing hype of “unhackable” isn’t 100 percent true.
Even though iOS security is excellent and Android security is more vulnerable, you shouldn’t rely on Apple to protect your data all by itself. But, that doesn’t mean you need antivirus software for your iOS devices either. A few minor changes to your habits and some awareness of common dangers is more than enough to keep your iPhone safe from hacks.
Pro Tip: Identity theft is one of the worst consequences of getting hacked. Aura gives you identity theft protection, antivirus software, and a VPN under one subscription. That’s one of the many reasons it sits at the top of our list of the best identity theft protection services. And, you’ll be surprised how affordable it is. Learn more about Aura’s subscriptions and pricing.
>> Related article: What Can Someone Do With Your Phone Number?
Can an iPhone Be Hacked?
If you’re worried about the security of your iPhone, it’s important to know that while iPhones are generally more secure than Android phones, they are not invincible. While iPhones can generally go without additional antivirus software, we always recommend top-of-the-line antivirus software for Android devices. Still, hackers can potentially gain access to your iPhone through vulnerabilities in apps or the iOS operating system, as well as by tricking you into downloading malware.
To protect your iPhone from potential attacks, make sure to keep your iOS and apps up to date, use strong and unique passwords, enable two-factor authentication, and be cautious when opening links or downloading files from unknown sources. Additionally, consider using a reputable antivirus app for added security. By taking these steps, you can help safeguard your iPhone against potential hacks and keep your personal information safe.
>> Related Article: The Best Password Managers for iPhone
Best iPhone Apps to Prevent Hacking
Installing antivirus software on your iPhone is one of the best protections against hackers and their malware. We’ve rated Norton, Kaspersky, and TotalAV the highest at protecting iPhones, since our tests found that these apps help protect against ransomware, spyware, and all different types of malware. Take a closer look below:



How iPhones Get Hacked
There are plenty of popular methods to get around iPhone security, and most of them involve tricking the user.
Sketchy Wi-Fi Connections
We’ve all encountered suspicious public Wi-Fi networks asking for a lot of personal info upfront, followed by around 100 pages of terms and conditions. We’ve caved in desperate moments, sometimes even without using a VPN to hide our browsing history and hide our IP addresses. These are the places we most often encounter sketchy Wi-Fi networks:
- Airports: Many airports across the U.S. have their own public Wi-Fi networks for passengers. These networks are just as insecure as any other public Wi-Fi network. Essentially, any Wi-Fi network that asks for detailed personal information or is operated by a third party raises even more red flags (we’re looking at you, Boingo!)2
- Budget hotels/motels: The upkeep on an expansive Wi-Fi network with hundreds of unique users and private connections is costly, so many affordable hotels opt to use one open network.
- Cafes and bars: “Free Wi-Fi” is virtually synonymous with coffee shops. While that Boingo pop-up at the airport probably raises your defenses, we’re willing to bet you don’t think twice about connecting to Starbucks’ Wi-Fi anymore.
Sketchy URLs
For anyone who still needs to hear it: never click on a link if you don’t recognize the sender or can’t verify that it comes from a trusted source. That tip alone will keep you safe from most online scams. Phishing is still one of the most popular internet scam techniques and comes in various forms, like these:
- Emails: These phishing emails aren’t like the kind from 20 years ago, where a randomized email address would send you a 200-character link to a “free cruise.” The more successful phishing emails you might encounter do a great job of impersonating account providers like Google, Amazon, or Apple, telling you to update your password or account bio.
- SMS: Text messages are a more recent favorite of phishers, relying on the quantity-over-quality technique. Typically, phishing text messages are referred to as “smishing.”
- Phone calls: Scam callers inundate U.S. phone numbers all day long. Phishing calls usually ask the target to call back about something relevant to the user, like debt restructuring, mortgages, or car payments.
- Social media: Social media accounts that show up as targeted ads are a new favorite phishing method, as we’re more likely to click on them.
- Web ads: Since the early days of the internet, sometimes clickbait ads contain adware that’s hard to remove. But scammers keep making adware because many people still click on banner or pop-up ads.
- Fraudulent software: The least-known phishing method, fraudulent versions of popular software tools can show up shockingly high in a Google search. Sometimes the websites offer a “free” version of paid software (although free software can be legitimate, as we’ve seen with free VPNs and free antivirus software).
Sketchy Apps
The adage for free social media platforms or apps is, “If they don’t charge you for the product, you are the product.” There’s a library’s worth of writing about how Facebook and Google sell user data. And only specific situations allow you to get your personal information deleted from Google. However, apps that aren’t cultural touchstones can still spy on you, especially if you permit them to do so.
Favorite targets for malware and spyware are simple apps with offerings for “free” wallpapers or ringtones, and novelty camera apps like FaceApp. Even apps from well-rated developers may still be malicious. Look out for these red flags:
- High power draw or overheating: If your battery heats up or drains faster while you use a particular app, it may be performing more tasks on your phone than advertised.
- Unnecessary permissions: A fitness-tracking iPhone app on your phone shouldn’t need access to your contacts. If it’s not taking pictures or video, an app shouldn’t need your camera and mic.
- Unusual mobile device behavior: If you notice a change in your device’s behavior, usability, or software interface after you download an app, it could be a sign of something more nefarious.
Sketchy People
Sometimes, the call may be coming from inside the house, metaphorically speaking.
- Stalkerware: Stalkers, abusive ex-partners, current partners, or family members can install a type of spyware sometimes referred to as “stalkerware” to track your every move and keystroke.3 Our post-breakup safety report outlines how, even in many non-abusive scenarios, an ex-partner can be a security risk. Around 22 percent of both men and women reported a financial security breach from an ex, for example.
- Direct data transfer: A much easier attack to carry out is stealing data manually. If you leave your phone unattended and unlocked, individuals with bad intentions can hook your phone up to another device and download files and data directly. Direct data transfer is more common with abusive partners or family members because of their frequent proximity to you and, thus, access to your device.
Sketchy Governments
Sketchy governments are a hacking threat primarily for journalists and political activists in undemocratic countries, which leads to greater VPN usage. However, historically oppressed peoples are at much higher risk of government surveillance than the average citizen.4
For the average American user, there might be a few scenarios when you need to worry about a government entity stealing your personal data:
- Trip to a totalitarian state: A foreigner visiting China might realize that everything is easier to navigate with social media and e-commerce apps like WeChat, Alipay, or QQ. Hundreds of millions of Chinese citizens use them every day. As a result, these apps are targets of internet censorship and broad government surveillance.5
- High-profile activism: Saying you stand with Hong Kong has become a famous rallying cry around the world, but it’s unlikely to make you a target of the Chinese Communist Party. However, if you’re Vladimir Putin critic Bill Browder, you should expect some state-sponsored hacking attempts to come your way.6
What You Can Do To Stop an iPhone Hack
We want to make sure, first and foremost, that you never experience an iPhone hack. However, if you do get hacked, we want you to know how to spot it and what you can do about it. Prevention, recognition, and response are key.
How To Prevent an iPhone Hacking
We know the long list of threats above seems daunting, so the main question we have to ask ourselves is, “What can I do to prevent my iPhone from getting hacked?”
- Install updates as soon as possible. Some updates are rushed fixes for newly discovered security vulnerabilities. Occasionally, you’ll have to deal with annoyances like slow loading times or minor glitches when you first install updates. However, these minor inconveniences are preferable to someone getting into your phone and stealing your identity.
- Set up two-factor authentication. Set up two-factor authentication to protect your Apple and iCloud accounts from unauthorized users. Multifactor authentication in the form of biometrics is even better!
- Use a VPN when on public Wi-Fi. Public Wi-Fi leaves you vulnerable to anyone who has access to the same network. By using a VPN on your iPhone when connected to public Wi-Fi, you can protect your iPhone when it’s most vulnerable to random hackers.
- Use a strong password. Make sure your secure password is a mix of letters, numbers, and special characters. It should also be unique to your Apple ID and contain at least 12 characters for maximum password security.
- Don’t offer personal info without confirming legitimacy. Investigate the requesting organization’s website to confirm it’s legit before sending along personally identifiable information.
- Set up a passcode. Once you take these steps, if you put your phone down for a predetermined period of time, it will require a passcode to open it up.
- Go to Settings.
- Tap “Touch ID & Passcode.”
- Tap “Turn Passcode On.”
- Tap “Passcode Options.”
- Select “Create a Custom Alphanumeric/Numeric Code.”
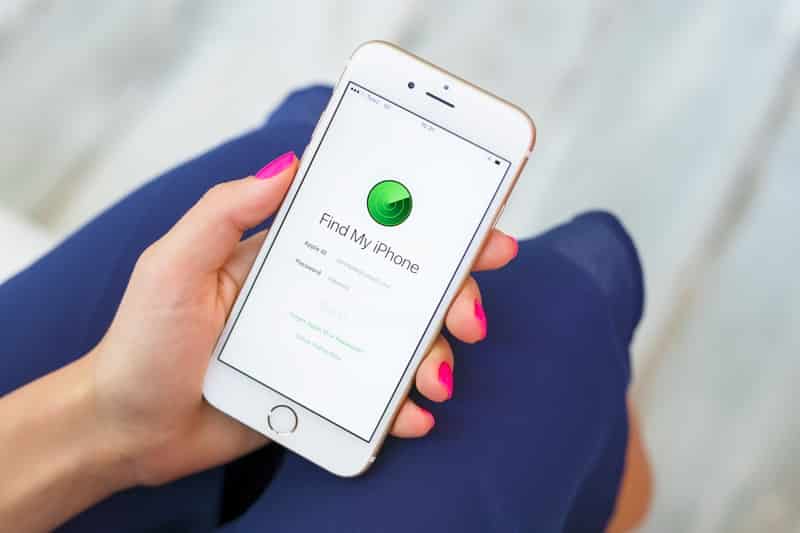
- Set up Find My iPhone. This feature helps you locate your phone easily in the event that you lose it.
- Go to Settings.
- Tap your name.
- Tap “Find My.”
- Tap “Find My iPhone.”
- Tap the switch icon to turn it on.
- To see your iPhone even when it’s offline, tap the switch next to “Find My Network.”
- To send Apple the last location of your phone when the battery is low, tap the switch next to “Send Last Location.”7
- Turn off Bluetooth when not in use. Hackers can discover and spoof other devices you’ve connected to before and gain access to your iPhone.8
- Go to Settings.
- Tap “Bluetooth.”
- Tap the Switch icon to turn it off.
How To Recognize if a Hack May Have Occurred
When a user’s phone has been hacked, there are usually some telltale signs something is amiss:
- The phone is constantly hot and low on battery.
- The phone is sluggish to load webpages, regardless of the connection quality.
- You don’t remember making certain calls or texts.
- Your contacts say they’re getting weird messages from you.9
Always do your research before concluding you’ve been hacked. Sometimes, a new iOS update is the culprit. Or maybe your iPhone is more than two years old, so your battery is now on the edge of planned obsolescence.
How To Respond to a Hack
It’s difficult to give specific advice without knowing the exact phone hack that occurred. However, here are some basic post-hack cybersecurity tips:
- If sketchy Wi-Fi is to blame, then disconnect and forget the network.
- If a sketchy URL might be the issue, remove anything downloaded after you went to that web address.
- If the trouble comes from a sketchy app, uninstall and delete the app, then update your phone.
- If your iCloud or Apple ID is compromised, contact Apple directly at 1-800-275-2273 on a different device, or visit an Apple store in person.
Recap
You are easier, quicker, and cheaper to manipulate than iOS code. Be a reasonable skeptic on your iPhone and the internet in general. Don’t click a link from an unverified source. Don’t offer private information to any entity you can’t confirm as legitimate based on information from their website. Finally, don’t use apps that ask for unnecessary permissions.
Simple security measures go a long way.
FAQs
Here are answers to your most pressing questions about iPhone hacks.
-
What does it look like when your iPhone is hacked?
There isn’t one example of what it looks like when your iPhone is hacked. You could get strange or inappropriate pop-ups or see apps you don’t recognize on your phone. Your battery might drain quickly, and your phone might show higher data usage. The biggest giveaway would be your contacts receiving texts or calls from you that you didn’t make.
-
Can iPhones get hacked from websites?
iPhones can get hacked from websites, which is why it’s best to use antivirus software to scan for malicious sites.
-
Can an iPhone be hacked remotely?
An iPhone can be hacked remotely through iOS vulnerabilities. However, it’s more likely that it’ll be hacked through malicious software or physical access, as programming-based hacking is the most difficult to carry out.
-
Can someone hack my iPhone by calling me?
No one can hack your iPhone just by calling you. However, a scammer might call and fool you into giving up personal information, which they could then use to hack your phone or steal your identity.
-
What happens when your iPhone gets hacked?
If your iPhone gets hacked, the hacker can access all of the files on your iPhone. This includes everything from your notes and photos to your text messages and apps. So, if you’ve ever sent a password through text or saved your bank account information in your Notes app, a hacker could access these key pieces of information.