In a world where online privacy is becoming increasingly scarce, it’s nice that there are digital tools to help us keep our online activities hidden from prying eyes. Virtual private networks (VPNs) are one of those tools, and they happen to be one of the most effective and easiest to use.
VPNs protect your privacy by encrypting your internet traffic — essentially scrambling your data — so that even if your ISP or the government sees that you’re online, there’s no way for them to know what you’re doing. And VPNs hide your real IP address by routing your traffic through VPN servers so that no one can know what websites you’re visiting. Talk about anonymity!
VPNs aren’t just for privacy, though. You can use a VPN to bypass geographic restrictions, avoid censorship, and access a more open internet. You can even use VPNs to torrent safely and securely without fear of being found out by your ISP.
But there’s still one question many have about VPNs: How do you choose the right one? We created this guide to share all about VPNs, how they work, what features you should look for, how to fix common issues, and what our favorite VPN picks are.
What is a VPN?
A VPN or virtual private network is a type of software that changes how your device connects to the internet. It sends all traffic through an encrypted tunnel to a VPN server. By doing so, it protects your online data and activity from hackers, snoopers, and your internet service provider (ISP). It also hides your real IP address from the websites you visit, making it appear as though the traffic is coming from the VPN server’s IP address.
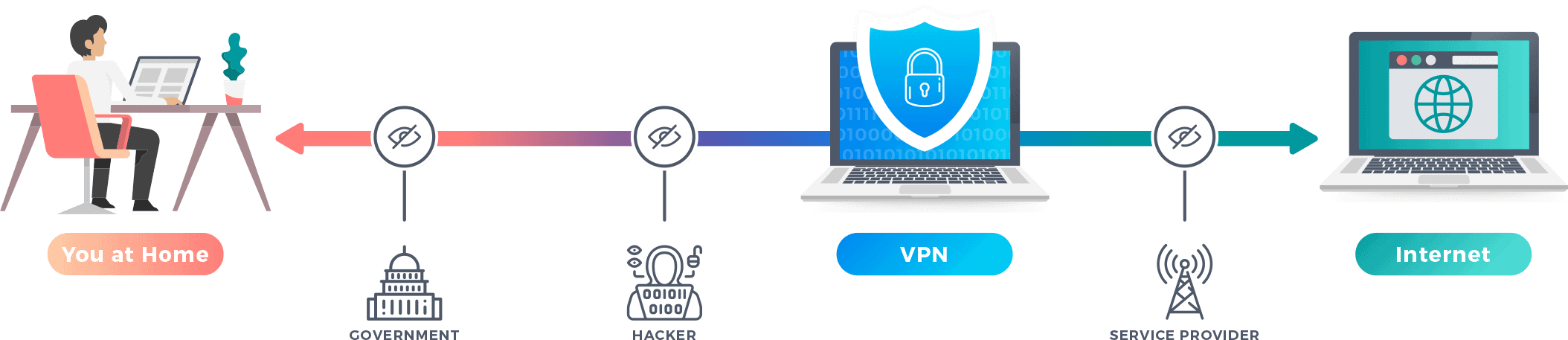
Why Use A VPN?
So, why would somebody use a VPN in the first place? There are a number of reasons, from increasing privacy to enjoying more entertainment options. Basically, using a VPN gives you access to a more open internet government firewalls, restrictions, and censorship. If that’s what you desire, keep scrolling and find out how you can use a VPN to improve your online experience.
Web privacy
You may think that what you do on your browser (and even your private browser) is only between you and your device, but that’s not the case. The moment you attempt to send or receive data over the internet, your ISP is already onto you, watching, monitoring, and collecting data. ISPs can see the websites you visit, your search queries, even your device’s unique IP address.
Your ISP isn’t the only one tracking you, though. Online advertisers use trackers to find your online activities and send you more relevant ads and generate more revenue for themselves. That’s why if you search for “smart TVs,” for example, you may start to notice smart TV ads pop up out of nowhere.
With a VPN, you can regain your online privacy. With a VPN, your IP address will remain anonymous to third parties and your online activities will be encrypted. That way, what you do online is between only you and your VPN server.
Using AT&T Internet? AT&T and other ISPs can see your activity unless you use a VPN. See our list of the Best VPNs for AT&T.
Access Content
Did you know that some online content might not be available to you right now just because of your location? If you go to China, for example, you won’t be able to access Facebook or X (Twitter). Netflix and other streaming sites are another example. Some shows available on Netflix U.S. aren’t available on Netflix U.K. and vice versa.
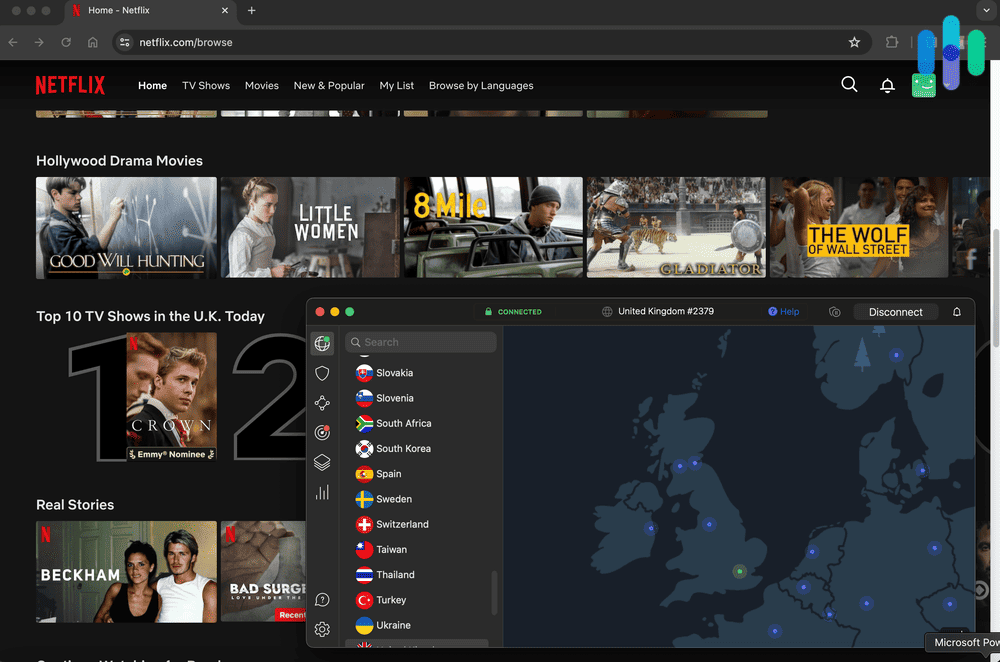
» Find Out: VPNs for Netflix
So how do VPNs help? Remember how we said that they hide users’ IP addresses? They don’t just hide IPs, but also change them to the IP address of the server. So if you connect to a U.K. server, you’ll get a U.K. IP address. Since most websites use IP addresses to determine a user’s location, your streaming service will think you’re in the United Kingdoms and will let you browse and binge U.K.-exclusive shows.
» Learn more: How to change your Netflix region
Torrenting
If you want to torrent more entertainment options, a VPN is a good safety measure (although we can’t and don’t recommend doing anything illegal).
Even if you’re torrenting completely legal files (i.e. non-copyrighted materials), the simple fact that you’re torrenting might draw some ire from your ISP and the government. You may receive a copyright infringement notice in the mail, or even have your internet connection throttled down by your ISP.
A VPN can hide the fact that you’re torrenting the same way it protects your online privacy, but again, we don’t condone torrenting illegal files and online piracy.
Bypass government restrictions
According to our survey, nine percent of VPN users utilize VPNs to avoid government internet censorship. China, for example, has a “Great Firewall” that doesn’t allow its people to view websites from outside the country,1 so a VPN would be helpful to access sites like Youtube, Google and Netflix. For example, you could connect to a U.K. IP address to access BBC content or connect to a U.S. IP address to access Netflix U.S.
VPNs vs. Routers vs. Bridges vs. Dongles vs. Tor
Of course, VPN software isn’t the only way to hide your IP address and web traffic; there are other methods, all of which have their advantages and disadvantages.
Private routers
Instead of using a VPN app or browser extension on your device itself, some people opt to use a VPN directly on a router, which will then encrypt their web traffic from all devices connected to the router automatically. This is certainly easier than connecting a VPN on each individual device, but not all VPNs work with routers.
Bridges
Rather than connecting to VPN software, you can also use a bridge, a physical ethernet adapter, which contains a different IP address that connects your computer to an entire local network. Of course, this uses a lot of bandwidth, so it’s not an ideal option compared to a VPN.
Dongles
Sure, it’s a silly word, but dongles are another way to connect to VPNs, so we have to mention them here. In essence, they’re adapters that plug into a computer’s port and can contain VPNs.
Tor browser
Finally, Tor is a network that utilizes its users’ computers to create a worldwide network that encrypts web traffic. The network is accessible through special browsers. However, Tor is pretty slow and doesn’t let us access all websites, unlike VPNs that open up access to the entire World Wide Web.
What VPNs Do
If we haven’t already made it clear, we’ll say it again for the cheap seats in the back: VPNs encrypt web traffic and change IP addresses. This means that their Internet Service Provider won’t be able to see what the user did online or their originating IP address, which leads to greater privacy, security and access to websites.
FYI: Curious as to how secure you really are both online and offline? Take our Security Score test to find out your physical and digital security score, which is determined based on a number of factors, including the prevalence of physical and digital security crimes in your area, lifestyle factors, and more.
How VPNs Work
VPNs connect a user’s device and a network, typically public, via an encrypted tunnel. The tunnel encrypts the user’s online activity and hides their IP address, replacing it with the IP address of the private server the user connects to. Most VPNs use AES-256 bit encryption, which is the current standard in the industry. To transmit the data itself from the device to the private server, VPNs use Internet protocols that put the data in packets and make sure it gets sent in the proper order. If the VPN fails, most come with kill switches that will shut down all windows or apps with web traffic, leaving the user protected and private online.
When Do I Use A VPN?
Want to hide all your information from your ISP? If so, use a VPN whenever you connect to the Internet. But for most people, VPNs on your home network aren’t necessary. Instead, most people use VPNs in the following networks:
Public Wi-Fi networks
You may not think much of joining Starbucks’ Wi-Fi network to browse Airbnbs for this weekend, but joining a public network makes you vulnerable to hacking,2 as your private IP address will be on the network’s router and thus, the public space’s ISP. Joining a VPN lets you encrypt your web traffic and hide your IP address while still allowing you to connect to that Wi-Fi you so desperately want.
Wired hotel networks
So you’re in a hotel’s workspace using their wired desktop computer. Is a VPN necessary? In our opinion, yes, it is necessary if you want to hide your activity and IP address from the hotel’s server; this is especially important if you’re dealing with sensitive customer or business information.
Office networks
If you’re in your office, connecting to a VPN probably isn’t necessary, but if you’re working remotely like 40 percent of Americans during the COVID-19 pandemic, a VPN can help. How? VPNs with split tunneling let you access a public and a private network at the same time, which decreases bandwidth creating faster speeds. So you can spend all day on your office network while enjoying those baguettes at your favorite cafe simultaneously. Bon appetit!
LTE networks
When Wi-Fi networks aren’t available, we revert to using data, typically through 4G LTE networks. The bottom line? VPNs are still necessary on LTE networks. Researchers have found 36 vulnerabilities on 4G LTE networks that would make devices vulnerable to hacking, so even on data, be sure to connect to your VPN.
VPN Pros and Cons
Bret Michaels says that every rose has its thorn, and the same is true of VPNs. Of course, they’re worthwhile overall, but still have their drawbacks, like anything else in the world.
Pros
- Anonymity: The big advantage of VPNs is that they give you the privacy you’ve never had while surfing the web. Not even your ISP can see your online activity when you’re connected to a VPN.
- Geo-shifting: By connecting to another country’s server, you can bypass government censorship and website limitations, like watching Netflix Canada instead of Netflix U.S. This really opens up the entire web for your browsing pleasure, regardless of where you are physically. Learn more about how VPNs hide your browsing history.
- Split tunneling: If you need to access a private network while using public Wi-Fi, VPNs with split tunneling will let you do both simultaneously with the click of a button.
Cons
- Slower browsing speeds: No matter the VPN and how fast they say they are, all VPNs slow down your Internet speed by some measure, as the data has to go through an encrypted tunnel rather than connecting directly to your router. Of course, we always test out our VPNs for their latency, download speed and upload speed so we can see exactly how much slowdown there really is.
- Blocked servers: While some VPNs allow for Netflix access, Netflix is getting smarter and blocks many VPN servers, so it’s never a guarantee.
- Cost: How much are VPNs? Although VPNs aren’t expensive, with prices starting at only a couple of dollars a month with some long-term plans, they are an additional cost, and depending on what you need them for or how long you need them, they may not be worth it. As an alternative to VPNs, you can use a proxy server, as these are usually free. You may also want to check out the VPN’s cancellation policy to know how to cancel your VPN or how to disable your VPN in the future.
Can I Stream with VPNs?
Even with thousands of options at hand, some people may want to stream movies and TV shows not available on their country’s server, or may not be accessible through streaming sites at all. For these instances, VPNs can help, allowing users to access streaming services in other countries as well as protection for torrenting. However, not all VPNs work with Netflix, or other streaming services like Prime Video, Hulu, and the like, so be sure to check this out before clicking purchase. And as an aside, VPNs also work with video game consoles like Xbox; learn how to use Xbox on a VPN.
Will VPNs Slow Down My Internet?
Unfortunately, VPNs will slow down your Internet to some extent, which we’d like to be as minimal as possible. Because of VPNs’ encrypted tunnels, your web data can’t connect directly to the router, but goes through a middle man, of sorts. Think of it like avoiding main highways and instead taking backroads. While you eventually get to the same place, the journey will take longer, although it has its advantages compared to conspicuous highways.
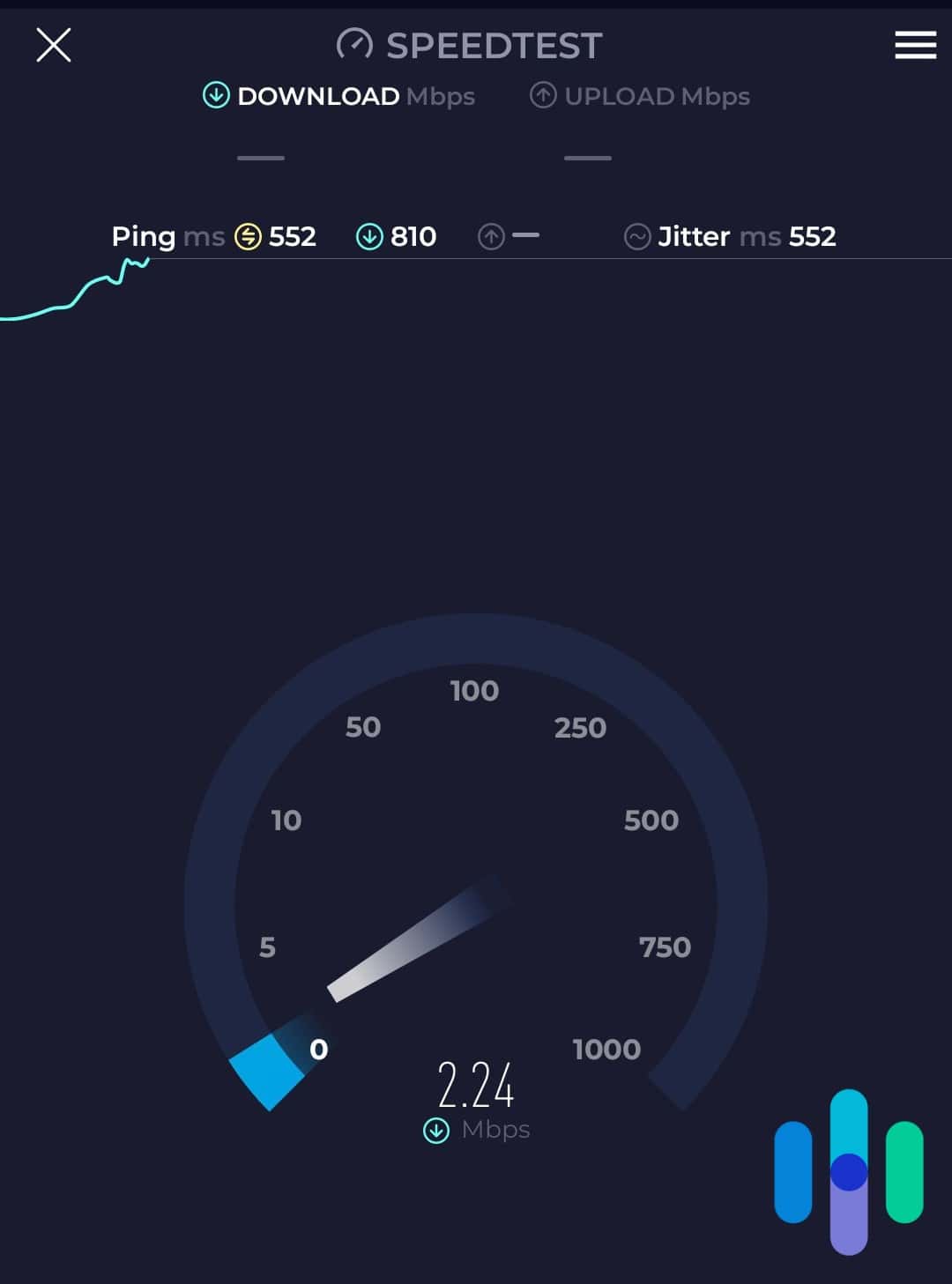
Of course, that doesn’t mean we want our Internet connection to be like molasses, which is why we test out all of our VPNs to see how they affect our download speeds, upload speeds, and ping, otherwise known as latency. But we’ll talk more about that in our methodology section, which goes over exactly how to test that VPNs are working.
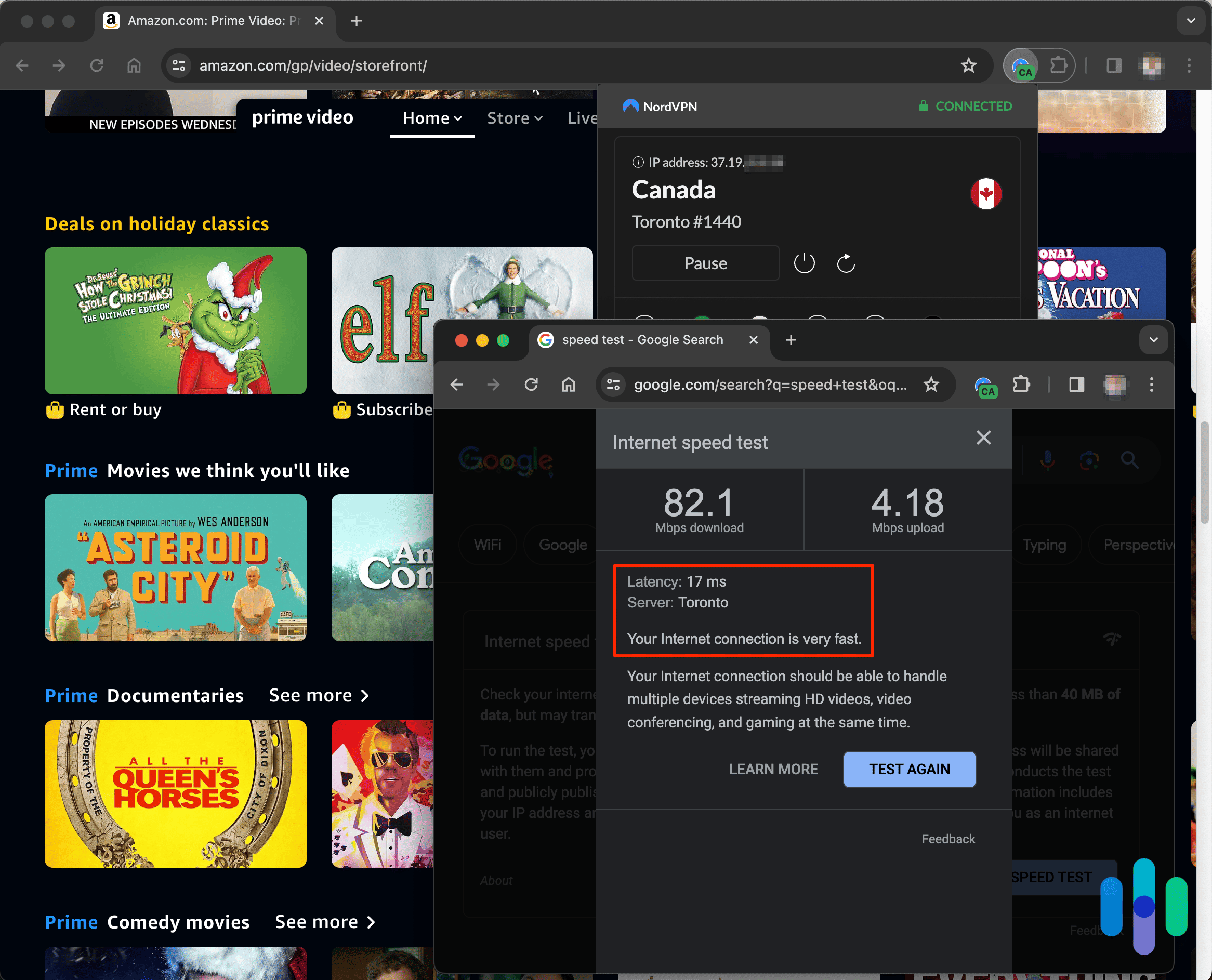
Are VPNs Legal?
Many people may be wondering if VPNs are legal in the first place. In the United States, VPNs are legal, but that doesn’t mean that everything a user does on them is legal. For example, torrenting copyrighted material is still illegal, even if you use a VPN (that would be like saying that burglary is legal if you just wear a mask). So while VPNs are legal in the United States, don’t think of them as a free-for-all. Also, keep in mind that different countries have different laws when it comes to VPNs; Russia, for example, has banned popular VPNs that we’ve tested out like NordVPN, ExpressVPN, HideMyAss, and IPVanish.3 In sum? If you’re traveling, be sure to familiarize yourself with a country’s laws before connecting to your good old VPN.
Are VPNs Hackable?
Can you hack something that’s meant to prevent hacking in the first place? The meta nature of this question makes our heads hurt but ultimately yes, even VPNs can be hacked (although in some cases, VPNs can prevent DDoS attacks). That’s because nothing that uses the Internet is 100 percent protected from hacking, including VPNs and identity theft protection services. However, there are some practices you can take to protect your VPN from being hacked, like using a strong password that you haven’t used on any other online account, or setting up two or multi-factor authentication. To sign in, we recommend requiring a passcode or your fingerprint or face ID, dramatically reducing unauthorized access to your VPN account.
VPN Limitations
While VPNs can be extremely useful in terms of protecting your data online, they have their limitations, depending on the specific brand as well as the subscription level you choose. Some things to look out for:
- Security breaches: If you’ve read any of our individual VPN reviews, you might notice how much time we spend on companies’ logging policies, typically buried on their websites’ privacy policies. That’s because we want to make sure that if a company has a security breach, they haven’t saved or logged any of our web traffic, just the basic information needed to uphold our accounts. Just last October, NordVPN had a third party breach4 which remained on their server for over a month before the company discovered it. Much to our dismay, security breaches are possible whenever a company stores customer data online, even with encrypted cloud storage and limited logging policies, so don’t think your VPN is invincible.
- Reliability: Not all VPNs are reliable, so some may have spotty service. We’ve definitely had technical difficulties while trying to connect to our nearest servers, only to try again the next day and find that it connected fine.
- Availability: Not every VPN will work for everyone in the world. Rather, it’s dependent on the locations of their servers, so make sure to find out if your area is covered before you choose one service over another.
- Data usage: Some VPNs put limits on data usage depending on which subscription you choose. TunnelBear, for example, has a 500 MB limit on its free subscription, but most paid VPN subscriptions allow for unlimited data use. Learn more about how VPNs use data.
- Server switches: Similarly, some subscriptions only allow for a limited number of server switches, although most are unlimited.
- Number of total devices: It’s more common for VPN subscriptions to differ based on how many devices you can connect to the VPN overall. If you want your entire family protected by a VPN, look for a company that allows for an unlimited number of devices.
- Number of simultaneous connections: We often find ourselves using multiple devices at once, watching TV on our Chromecast, texting our friends on our iPhones and looking for cute bedding on our Macbook. Sure, it sounds ridiculous, but when we want multiple devices to be connected to a VPN at once, we make sure that our subscription allows for that. While some VPNs allow an unlimited number of devices to be connected at the same time, some only allow one, five or 10.
VPN Buying Guide
Now that you’re a bonafide VPN expert like us, it’s time to actually pick out the VPN you want to use. But before you get too excited, here are some considerations you should make when making your purchase decision.
- Server locations: The distance from a server can affect the speed of your VPN, so check out the VPN’s list of server locations to make sure you’ll go full speed ahead.
- Speed: Speaking of speed, you should take all speed tests with a grain of salt, even the ones we perform. Why? Because speed is dependent on so many factors other than just a VPN, like the make of our computer or phone, the year it’s from, what operating system we’re using, and more. So even though you should consider factors like download speed, upload speed and ping, you may want to get the VPN and test it out for yourself; look for VPNs with free trial periods or subscriptions or money-back guarantees. More info on how to test out the speed of your VPN below!
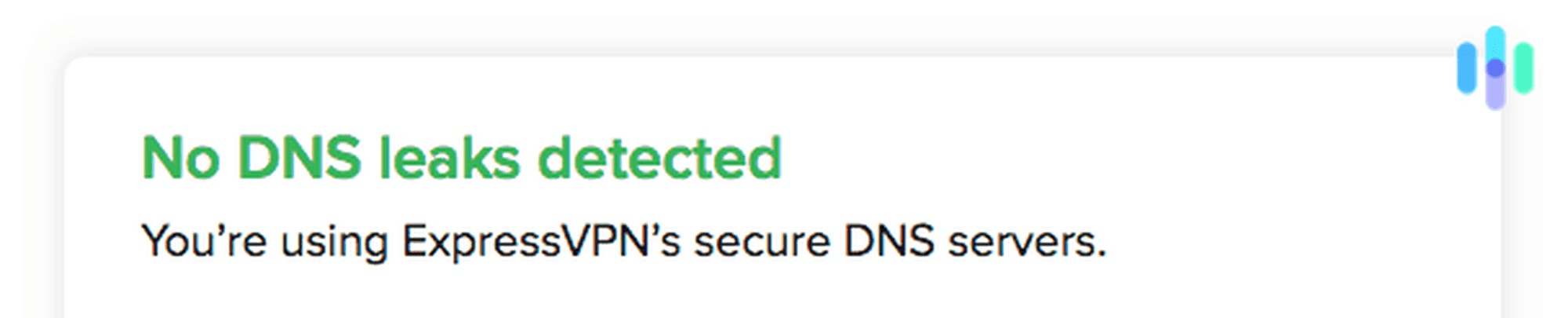
- DNS/ WebRTC Tests: Basically, a VPN only does what it says it does if it hides our Domain Name Server or DNS, basically the websites we go to, as well as our private IP addresses, which are exposed when our browsers default to WebRTC. Fortunately, there are simple tools available online to test this out, which we write about in each VPN’s individual review; however, if you want to do the test yourself, skip to the next section.
- Encryption: Another essential feature of a VPN is encryption. We want all of our web traffic and our private IP addresses to be encrypted so that even if someone hacks into our VPN, they won’t actually be able to see any of our data. We look for VPNs with either OpenVPN or AES-256 encryption, the most secure methods available.
- Privacy policy: You know the lines upon lines of small text that you typically agree to without even skimming? We actually read those to find out if the VPN company keeps our data, and if so, exactly what data they keep. While we understand the company keeping information necessary to uphold our accounts, like our names and payment information, it’s not acceptable for a company to keep any of our web traffic or originating IP address, in our opinion.
- Headquarters: We also care about where a company is based. Why? Because if a company’s headquarters are based in a country that’s a member of Five Eyes, Nine Eyes or 14 Eyes, it could mean that they could be forced to hand over customer data to the government. Countries like the United States and the United Kingdom are members, so we prefer VPNs based in non-member countries like Panama or Romania. This is especially important if privacy is a major concern for you!
- Device compatibility: Don’t forget to make sure that the VPN will work on the devices you want to use it on; normally, this shouldn’t be a problem for popular devices like iOS, MacOS, Android or Windows, but if you have a device from a less popular manufacturer, you’ll want to double check for compatibility. Read more about how to set up a VPN on iPhones, how to set up a VPN on Macs, or how to set up an Android VPN. You can even set up a VPN on your Fire TV Stick or set up a VPN on Kodi, set up a VPN on a router, or set up a VPN in general.
- Kill switch: If we’re using a VPN and it fails, does that mean our Internet Service Provider can access which websites we’re on? The answer is yes, unless of course the VPN has a kill switch that automatically shuts down all web browsers in case it fails. Needless to say, we prefer this option, which is why we always look for kill switches, also called network lock features.
- Netflix: Whether you want to bypass a country’s restrictions or even check out the offerings Netflix has in another country, make sure that Netflix hasn’t blocked the VPN’s IP addresses if that’s something you’re interested in. Read about how to watch Netflix with a VPN.
- Torrenting: The same goes for torrenting; if you want to torrent files, make sure your VPN allows for it, as not all of them do. Learn how to use a VPN for torrenting, or check out our VPN how to page for more step-by-step instructions.
- IP addresses: We prefer VPNs with dynamic IP addresses, meaning that they give us a new IP address every time we connect, or sometimes even more often. This is better than a static IP address that stays the same every time, much easier to trace. However, if the IP address is static, that’s okay as long as it’s shared by multiple users.
- Internet protocols: Internet protocols determine exactly how a VPN transmits our data from our device onto their private network. Our individual reviews go into each protocol and how it works, but typically we prefer protocols like TCP, Transmission Control Protocol, or UDP, User Datagram Protocol, both commonly used with VPNs.
- Subscriptions: How much is a VPN? Money is always a factor with any VPN service. While there are some VPNs that offer free options, they are typically limited, either by the amount of data we could use while on the VPN or by the number of days we had to connect. Most likely, you’ll need to shell out a bit of money for a VPN, so it’s important that you don’t overpay.
- Pricing: The below chart has all of the most recent payment information from each VPN that we’ve reviewed. As you can see, you can get a VPN for only a few dollars a month, although prices go all the way up to $15 a month. But that depends largely on the contract length, which brings us to our next point…
| VPN Reviews | VPN Pricing Pages | Cost of Monthly Plan | Monthly Cost with Three Month Plan | Monthly Cost with Six Month Plan | Monthly Cost with Annual Plan | Monthly Cost with 18 Month Plan | Monthly Cost with Two Year Plan | Monthly Cost with Three Year Plan |
|---|---|---|---|---|---|---|---|---|
| Astrill VPN Review | Astrill VPN Pricing | $25 | n/a | $16.67 | $12.50 | n/a | n/a | n/a |
| Avast SecureLine VPN Review | Avast SecureLine VPN Pricing | n/a | n/a | n/a | $4.60 | n/a | $4.20 | $3.75 |
| Betternet VPN Review | n/a | $12.99 | n/a | n/a | $7.99 | n/a | n/a | n/a |
| CyberGhost Review | CyberGhost Pricing | $12.99 | n/a | n/a | $4.29 | n/a | $3.25 | $2.29 |
| ExpressVPN Review | ExpressVPN Pricing | $12.95 | n/a | $9.99 | $6.67 | n/a | n/a | n/a |
| FastestVPN Review | FastestVPN Pricing | $10 | n/a | n/a | $2.49 | n/a | n/a | $1.11 |
| HideMyAss Review | HideMyAss Pricing | n/a | n/a | n/a | $4.99 | n/a | $6.99 | $2.99-$5.99 |
| Hotspot Shield Review | Hotspot Shield Pricing | $12.99 | n/a | n/a | $7.99 | n/a | n/a | n/a |
| IPVanish Review | IPVanish Pricing | $10.99 | $5.32 | n/a | $3.99 | n/a | n/a | n/a |
| Ivacy VPN Review | Ivacy VPN Pricing | $9.95 | n/a | n/a | $3.99 | n/a | n/a | n/a |
| IVPN Review | n/a | $6 for 2 devices, $10 for 7 devices | n/a | n/a | $5 for 2 devices, $8.33 for 7 devices | n/a | $4.16 for 2 devices, $6.66 for 7 devices | $3.88 for 2 devices, $6.11 for 7 devices |
| KeepSolid VPN Unlimited Review | KeepSolid VPN Unlimited Pricing | $9.99 for 5 devices, $14.99 for 10 devices | n/a | n/a | $5 for 5 devices, $7.50 for 10 devices | n/a | n/a | $2.78 for 5 devices, $4.17 for 10 or $199.99 for a lifetime subscription on 5 devices |
| Mozilla VPN Review | Mozilla VPN Pricing | $4.99 for 5 devices | n/a | n/a | n/a | n/a | n/a | n/a |
| NordVPN Review | NordVPN Pricing | $11.95 | n/a | n/a | $4.99 | n/a | $3.99 | n/a |
| Norton Secure VPN Review | Norton Secure VPN Pricing | $4.99 for 1 device, $7.99 for 5 devices, $9.99 for 10 devices | n/a | n/a | $2.49 for 1 device, $1.25 for 5 devices, $5 for 10 devices | n/a | n/a | n/a |
| Perfect Privacy Review | Perfect Privacy Pricing | $12.99 | n/a | n/a | $9.99 | n/a | $8.95 | n/a |
| Private Internet Access Review | Private Internet Access Pricing | $11.99 | n/a | n/a | $7.50 | n/a | $2.19 | n/a |
| ProtonVPN Review | ProtonVPN Pricing | $0 for 1 device, $5 for 2 devices, $10 for 5 devices, $30 for 10 devices | n/a | n/a | $0 for 1 device, $4 for 2 devices, $8 for 5 devices, $24 for 10 devices | n/a | $0 for 1 device, $3.29 for 2 devices, $6.63 for 5 devices, $19.96 for 10 devices | n/a |
| PureVPN Review | PureVPN Pricing | $10.95 | n/a | n/a | $2.99 | n/a | $1.99 | n/a |
| StrongVPN Review | StrongVPN Pricing | $10.99 | n/a | n/a | $3.66 | n/a | n/a | n/a |
| Surfshark Review | Surfshark Pricing | $15.45 | n/a | n/a | $3.19 | n/a | $2.19 | n/a |
| Trust.Zone Review | Trust.Zone VPN Pricing | $8.88 | n/a | n/a | $3.33 | n/a | $2.33 | n/a |
| TunnelBear Review | TunnelBear Pricing | $9.99 | n/a | n/a | $4.99 | n/a | n/a | $3.33 |
| Windscribe Review | Windscribe Pricing | $9.00 | n/a | n/a | $4.08 | n/a | n/a | n/a |
| VPNSecure Review | VPNSecure Pricing | n/a | $8.32 | $6.66 | $5 for 5 devices, $7.50 for 10 devices | n/a | $2.99 | n/a |
| VyprVPN Review | VyprVPN Pricing | $15.00 | n/a | n/a | $8.33 | n/a | $n/a | n/a |
- Contract Length: To get the most savings, sign up for the longest term-length; the longest we’ve seen is three years. However, if you aren’t sure about the VPN or only need it for a little, sign up for a month-to-month option; it’ll cost more, but you won’t be locked in.
- Simultaneous connections: How many devices can be connected to the VPN at the same time? If you are a device-head or are getting a VPN for multiple people to use, make sure the subscription allows for enough simultaneous connections. Some even allow for unlimited connections at the same time, although this might slow down your Internet connection significantly.
- Server switches: Some VPNs have limits on the number of servers you can connect to, so if you’re a big traveller, make sure the one you choose allows for sufficient server switches.
- Total number of devices: The same goes for the total number of devices you can connect to the VPN, whether simultaneously or not. Many VPN subscriptions only apply to a limited number of devices, so that’s something to keep in mind, as well.
- Discounts: Our ears perk up whenever we hear or think about savings. Any VPNs offer discounts, whether they’re seasonal or for students, so make sure to take advantage of these deals.
- Free VPNs: Again, some VPNs, like iTop VPN, have free options, but these are typically limited by the amount of data transferred or the time period you can use them in. Unless you only need a VPN for a specific task or time period, it probably makes sense to cough up a few dollars a month for a paid subscription.
- Customer Support: Unfortunately, customer support isn’t an area where most VPNs shine, as the majority lack phone lines. However, we appreciate VPNs with a bunch of different ways to contact customer support, be it through email, live chat, or phone, as well as a robust online help center to answer any questions we may have.
- App: Finally, take a look at the VPN app ratings on either the Apple or Google Play store; some VPN apps are super buggy, to the point where we couldn’t even connect, so this is definitely a major area of concern.
VPN Comparisons
- CyberGhost vs. ExpressVPN July 24, 2024
- CyberGhost vs. NordVPN November 26, 2024
- Private Internet Access vs. ExpressVPN May 9, 2025
- Private Internet Access vs. NordVPN November 26, 2024
- ProtonVPN vs. NordVPN November 27, 2024
- PureVPN vs. NordVPN December 2, 2024
- Surfshark vs. ExpressVPN January 23, 2024
- Surfshark vs. NordVPN April 14, 2025
- Norton Secure VPN vs. Surfshark February 19, 2025
- TunnelBear vs. ExpressVPN August 22, 2024
- TunnelBear vs. NordVPN December 3, 2024
- Windscribe vs. NordVPN March 28, 2025
- NordVPN vs. ExpressVPN April 14, 2025
- NordVPN vs. Norton Secure VPN November 26, 2024
- NordVPN vs. VyprVPN November 27, 2024
- Surfshark vs. Windscribe August 22, 2024
VPN Alternatives
- 3 Best NordVPN Alternatives in 2025 November 26, 2024
- 3 Surfshark Alternatives Our Experts Recommend in 2025 December 19, 2024
- Best ExpressVPN Alternatives, Vetted by Experts January 6, 2025
- Best IPVanish Alternatives in 2025 January 6, 2025
Have you tried a VPN and found that it wasn't for you? Take a look at some alternatives to some of the bigger brands.
How We Test VPNs
Aside from looking for the above features, we put each of our VPNs through three tests on two different types of devices, typically a Macbook and a Windows computer. We perform these tests on our home and office Wi-Fi networks, making sure we’re the only ones using them, with and without the VPN as a baseline. Typically, we do these tests from our office in Brooklyn, but in travelling, we’ve also done them from Poland and even the Philippines, in some cases. Here’s exactly how we do each speed and security test:
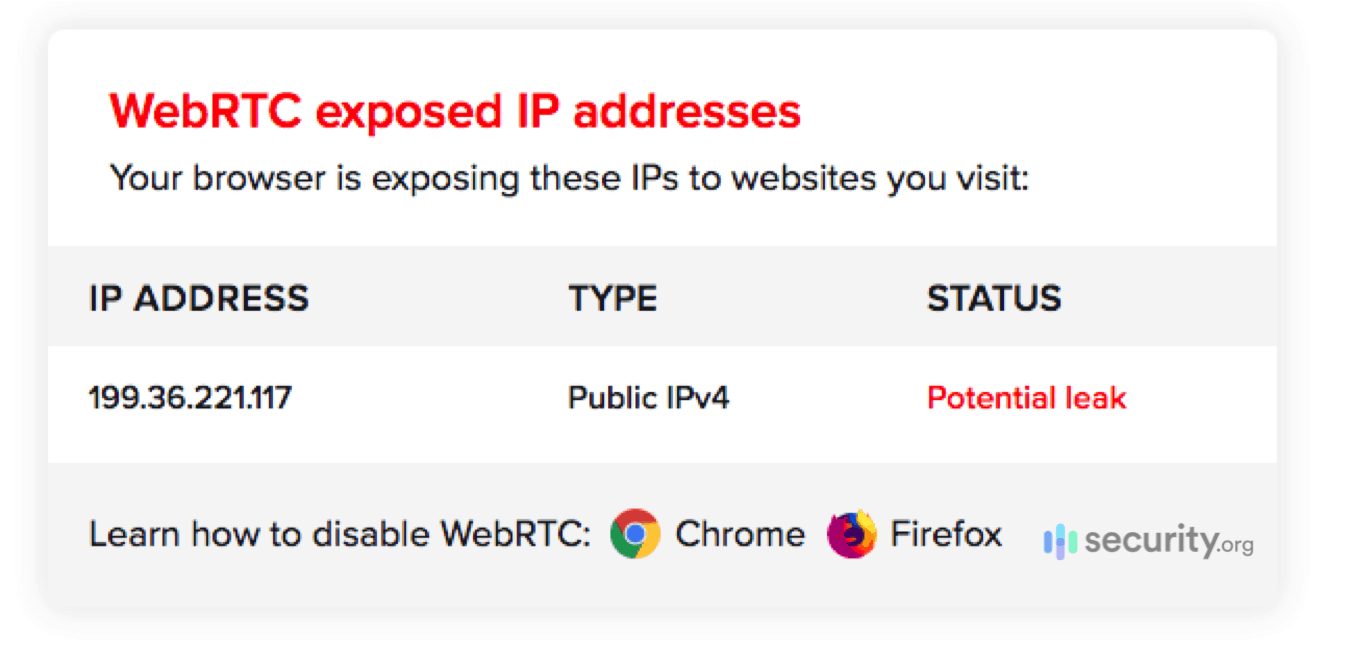
- WebRTC leak test: To make sure our private IP addresses are being hidden with the VPN on, we use the WebRTC leak test5 on ExpressVPN’s website, making sure that it shows a different IP address with our VPN connected and not connected. If your IP address is not private, there are many things that someone can do with this information.
- DNS leak test: The same goes for our Domain Name Servers, or website URLs. To check for DNS leaks, we use the tool on DNSLeakTest.com,6 again, noting a change in IP address with the VPN connected.
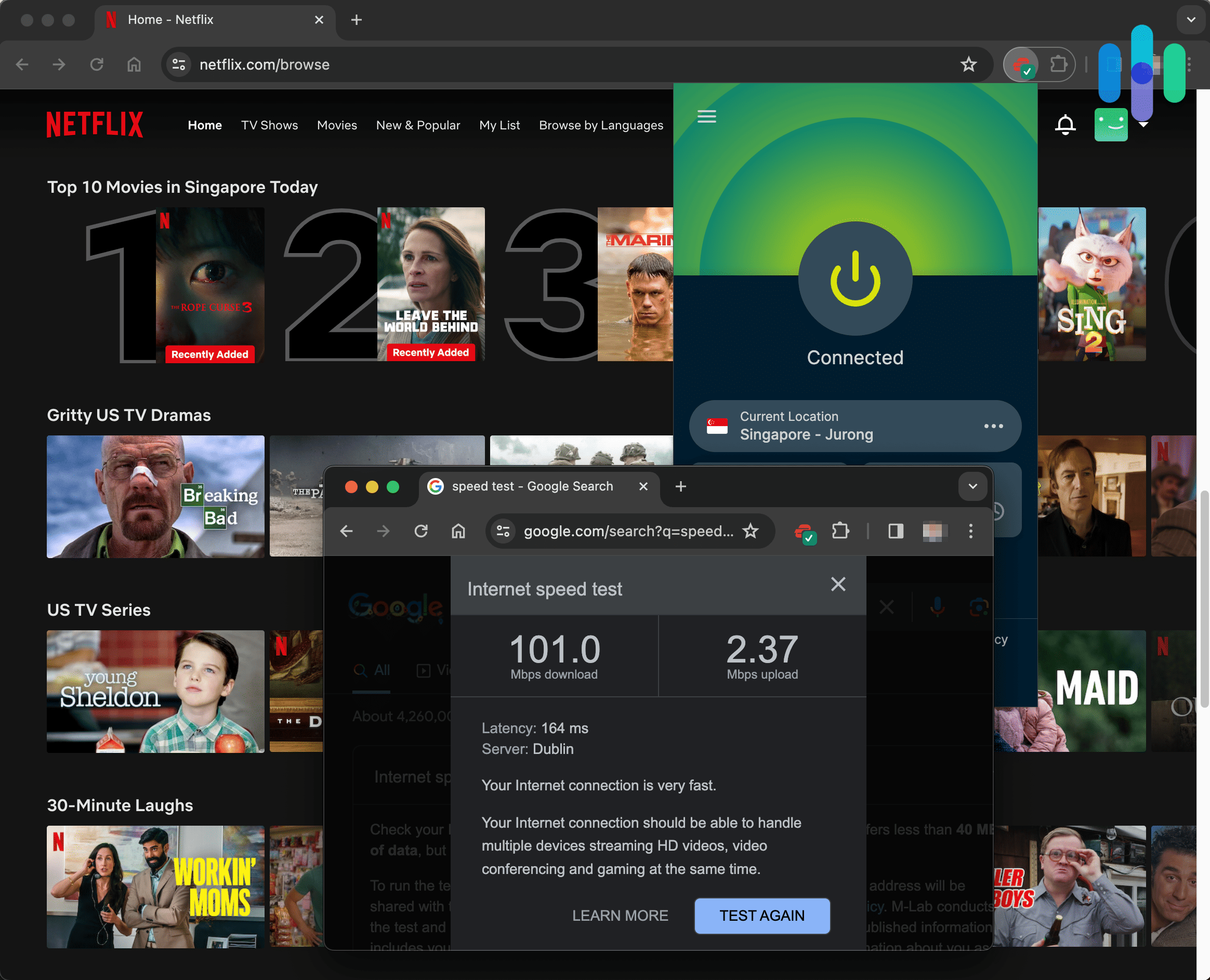
- Speed test: Finally, to test for a difference in ping (latency), download speed and upload speed, we use the speed test from Ookla,7 which measures the speed in ms for ping and mbps for download and upload speeds. Then, we do some math to figure out how much these speeds changed with and without the VPN; you could do this by hand, but we prefer using an online percentage calculator.8 Hey, we’ve got places to be and VPNs to test out and math is not our thing, unlike technology.
VPNs and Net Neutrality
Net neutrality means that web pages aren’t throttled or slowed down based on how new they are, how popular they are, and how many paid ads they have. That means that smaller or newer websites won’t be punished with slower speeds, upheld in the U.S by the FCC in 20169 and confirmed by the Restoring Internet Freedom Order which took effect in 2018.10
But while the U.S protects net neutrality, this isn’t the case in all countries, and VPNs can help. By hiding your web activity, your ISP won’t be able to see what websites you go on, which means that they can’t enforce throttling. Just another way that VPNs lead to more accessibility, as all websites will run as fast as they’re able.
» Learn more: What Is a VPN Concentrator?
How to Remain Anonymous Online
VPNs aren’t the only way to remain anonymous online; however, we’d argue that they are the top option. Still, there are other browsers and software available along with best practices to stay as private online as possible, such as:
-
- Use Tor: Tor is an encrypted browser that hides a user’s web activity by encrypting it three times; however, unlike a VPN, Tor does not cover web apps and does not encrypt device IP addresses.
- Use proxy servers: Proxy servers are another VPN alternative, but again, comparing proxy servers vs VPNs is a little like comparing apples and oranges, as proxies only encrypt device IP addresses and the web activity of only one browser or web app. Again, VPNs provide better coverage, but proxies are typically free, with the caveat that they could potentially sell user data. Based on all of our testing, see our top picks for proxy servers.
- Don’t give out personal information: Whenever possible, avoid giving websites or apps your PII, or personally identifiable information.
- Disable cookies: In the same vein, do not accept cookies whenever possible, as that leads to tracking your online activity
- Use a fake email address: If you need to give out your email address, create a fake one to conceal your identity.
- Use an encrypted messaging app: Apps like Signal won’t log the content of your messages, allowing you to communicate free from the eyes of your internet service provider.
- Delete social media accounts: While making your social media accounts private is a start, staying truly anonymous online requires deleting accounts completely instead of deactivating them. For example, if you deactivate your Facebook, some of your information will still be visible, like the messages you’ve sent. To delete this message history requires deleting your account.11
- Limit app permissions: Apps should only be allowed to access as little of your data as possible, so make sure to turn off as many permissions as you can.
- Turn off Wi-Fi and location: In general, you should only join public Wi-Fi networks with VPNs, so make sure your phone doesn’t join networks automatically and turn location services off unless you need them to use a specific app.
- Use an ad blocker: Finally, ad blockers can limit tracking across sites, reducing the chances that your data will be used for targeted advertising.
Recap
Finally, we’ve reached the end of our VPN guide, but if you’d like to learn more about how to stay safe and private online, read our digital privacy guide, our page of 2025 data security statistics, our page of VPN statistics, or our piece on the Internet and data privacy. While there’s no way to completely prevent security breaches, hacking, phishing and the like, the more you learn, the better you can protect yourself.
FAQs
Since we’ve tested out dozens of VPNs (and counting), we get a barrage of questions about VPNs, which we thought we’d attempt to answer here.
-
What does a VPN do?
VPNs encrypt a user’s web traffic and replace their IP address with the IP address of their private server, essentially hiding their browsing.
-
How much does a VPN cost?
VPNs typically cost anywhere from two to 15 dollars a month, depending on the service, contract length, amount of simultaneous connections and other features.
-
Can my Internet provider see my VPN?
No, Internet Service Providers (ISP) cannot see your VPN. VPNs hide your web activity and IP address so your ISP has no idea what you do online.
-
Can you be tracked if you use a VPN?
It is possible to be tracked if you use a VPN if you have a static IP address, meaning you get the same IP address every time you connect to the private server. However, with a dynamic IP address that changes every time you connect, it becomes harder to be tracked while using a VPN.